The ongoing campaign infiltrating malicious JavaScript injects into legal websites to promote Chinese gambling platforms has swelled to compromise around 150,000 sites so far.
“Threat actors have slightly revamped their interfaces, but they rely on IFRAME injection to display full-screen overlays in visitors’ browsers,” C/Side Security Analyst Himanshu Anand said in a new analysis.
At the time of writing, there are over 135,800 sites that contain JavaScript payloads, according to publicwww statistics.

As documented last month by website security companies, the campaign involves infecting your website with malicious JavaScript designed to hijack users’ browser windows and redirect site visitors to pages that promote gambling platforms.
It is known that redirection occurs via JavaScript hosted in 5 different domains (Zuizhongyjj[.]com”) It provides the main payload responsible for performing the redirect.
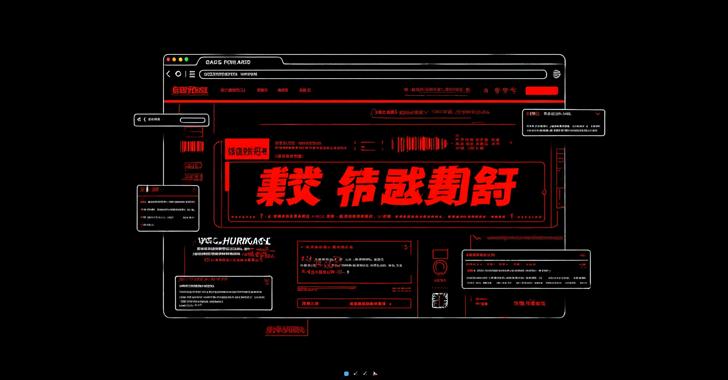
C/Side said it also observed another variant of the campaign that involves injecting scripts and IFRAME elements into HTML that are spoofing legitimate betting websites such as BET365 using official logos and branding.
The ultimate goal is to provide a full screen overlay using CSS that displays malicious gambling landing pages when you visit one of the infected sites instead of actual web content.
“This attack shows how threat actors can adapt, increase their scope and use a new layer of obfuscation,” Anand said. “These client-side attacks are on the rise, and there are more and more research results every day.”
This disclosure comes as GoDaddy reveals details of a long-term malware operation called Dollyway’s world domination.


“Current repetition […] It targets infected WordPress site visitors primarily through injected redirect scripts that use a distributed network of traffic direction system (TDS) nodes hosted on compromised websites,” said security researcher Denis Sinegubko.
“These scripts redirect site visitors to various scam pages through a traffic broker network associated with Vextrio, one of the largest known cybercriminal affiliate networks that leverage sophisticated DNS technologies, traffic distribution systems, and domain generation algorithms to provide malware and fraud across the global network.”
The attack starts by injecting dynamically generated scripts into your WordPress site, which ultimately redirects the visitors to a Vextrio or Lospollos link. The activity is also said to have used ad networks such as PropellerAds to monetize traffic from compromised sites.

Server-side malicious injections are facilitated via PHP code inserted into the active plugin, but take steps to disable the security plugin, remove malicious admin users, and achieve legitimate admin credentials to Siphon’s goals.
GoDaddy has revealed that Dollyway TDS will leverage the distributed network of compromised WordPress sites as TDS and Command and Control (C2) nodes, reaching 9 million pages of impressions each month. Additionally, it is known that the Vextrio redirect URL is retrieved from the Lospollos Traffic Broker Network.
Around November 2024, the Dollyway operator is said to have removed some of the C2/TDS servers. The TDS script retrieves the redirect URL from a telegraph channel named TraffureDirect.
“The disruption in Dollyway’s relationship with Losporus represents a significant turning point in this long-term campaign,” Sinegbo noted. “Operators have demonstrated significant adaptability by quickly moving to alternative traffic monetization methods, but rapid infrastructure changes and partial outages suggest some operational impact.”
Source link