The US Cybersecurity and Infrastructure Security Agency (CISA) has added high-strength security flaws that affect Nakivo backup and replication software to its known Exploited Vulnerabilities (KEV) catalogues, citing evidence of active exploitation.
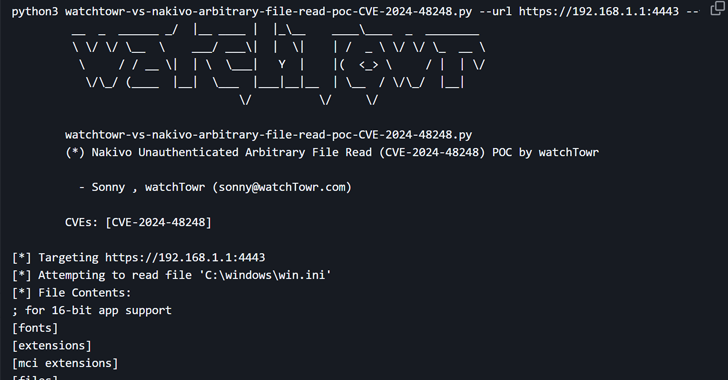
The vulnerability in question is CVE-2024-48248 (CVSS score: 8.6). This is an absolute path traversal bug that allows you to read files on the target host to the target host containing sensitive hosts such as “/etc/shadow” via the endpoint. It affects all versions of the software before version 10.11.3.86570.
“Nakivo backups and replications contain an absolute path traversal vulnerability that allows an attacker to read any file,” CISA said in its advisory.

The successful exploitation of the flaws allows the enemy to read sensitive data, including configuration files, backups and credentials, and could even serve as a stepping stone for compromise.
Currently, there is no details on how vulnerabilities are being exploited in the wild, but development will take place after WatchTowr Labs announced its exploitation of a proof of concept (POC) towards the end of last month. This issue was addressed in version V11.0.0.88174 in November 2024.
The cybersecurity company also noted that it could weaponize the unauthenticated arbitrary file read vulnerability to retrieve all stored credentials used in the target Nakivo solution and hosted in the database “Product01.h2.db”.
Also, two other flaws added to the KEV catalog –
CVE-2025-1316 (CVSS score: 9.3) – edimax IC-7100 IP camera contains OS command injection vulnerabilities due to inappropriate input sanitization that allows attackers to achieve remote code execution via specially created requests. Java contains a directory traversal vulnerability for Scheduler/UI/JS/FFFFFFFFBCA41EB4/UIUTILJAVASCRIPTJS.

Last week, Akamai revealed that since May 2024, CVE-2025-1316 has been weaponized by bad actors to target cameras with default credentials to deploy at least two different Mirai Botnet variants.
In light of active exploitation, a Federal Private Enforcement Division (FCEB) agency is required to apply the necessary mitigation and ensure the network by April 9, 2025.
Source link