Cybersecurity researchers have revealed details of the currently patched security flaws in the Amazon EC2 Simple Systems Manager (SSM) agent.
The vulnerability makes an attacker likely to create directories in an unintended location on the file system, run arbitrary scripts with root privileges, and perform malicious activity by writing files to sensitive areas of the system, reports shared with Hacker News.

The Amazon SSM Agent is a component of Amazon Web Services (AWS) that allows administrators to remotely manage, configure, and execute commands on EC2 instances and on-premises servers.
The software processes commands and tasks defined in the SSM documentation. This includes one or more plugins. Each plug-in is responsible for performing certain tasks, such as running shell scripts and automating deployment and configuration-related activities.
Additionally, the SSM agent dynamically creates directories and files based on plugin specifications. It usually depends on the plugin ID as part of the directory structure. This introduces security risks in that inappropriate verification of these plugin IDs can lead to potential vulnerabilities.
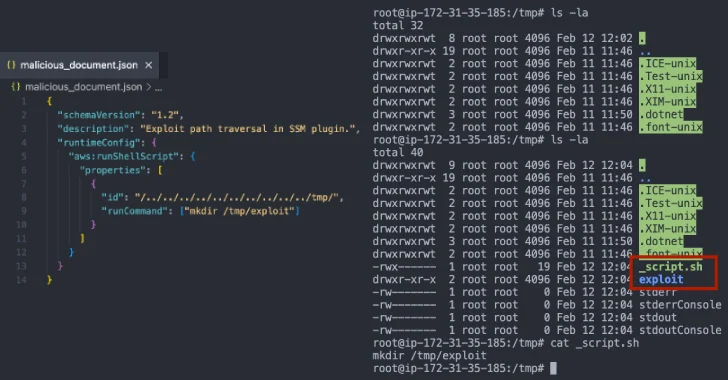
Cymulate discovery is a path traversal flaw that results from inappropriate verification of plugin IDs, allowing attackers to manipulate the file system and execute arbitrary code with high privileges. This problem is rooted in a function named “ValidatePluginid” in Plaginutil.go.
“This function fails to properly sanitize inputs and allows attackers to provide malicious plug-in IDs that contain the path traversal sequence (../),” said security researcher Elad Beber.

As a result of this flaw, an attacker can essentially provide a specially created plugin ID when creating an SSM document (such as .././../../../../../../../../../../../../../../../../.. As a result of this flaw, an attacker can essentially provide a specially created plugin ID when creating an SSM document (such as .././../../../../../../../../../../../../../../../../../../.. The attacker can essentially provide a specially created plugin ID when creating an SSM document (such as .././../../../../../../../../../../../../../../../../../../../../.. The attacker can essentially provide a specially created plugin ID when creating an SSM document (such as .././../../../../../../../../../../../../../../../../../../../../../.. The attacker can essentially provide a specially created plugin ID when creating an SSM document (such as ../../../../../../../../../../../../../../../../../../../../../../../.. The attacker can essentially provide a specially created plugin ID when creating an SSM document (such as ../../../../../../../
Following the responsible disclosure on February 12, 2025, the vulnerability was addressed on March 5, 2025 with the release of Amazon SSM Agent version 3.3.1957.0.
According to release notes shared by GitHub project maintainers, “We will use the buildsafepath method by adding and using it to prevent path traversal within the orchestration directory.”
Source link