The China-related threat actor, known as UNC5174, is attributed to a new campaign that leverages a known malware variant called snow light and a new open source tool called VSHELL that infects Linux systems.
“Threat actors use open source tools in their armory for cost-effectiveness and obfuscation, in this case they’re more integrated with non-state support, often non-technical pools of enemies.
“This seems particularly true for this particular threat actor who has been under the radar last year since partnering with the Chinese government.”
UNC5174, also known as Uteus (or uetus), was previously recorded by Google-owned Mandiant as leveraging security flaws in Connectwise Screenconnect and F5 Big-IP software. Super shell.

Also, the attack was Goreverse, a public reverse shell backdoor written in Golang, which runs on Secure Shell (SSH).
In a 2024 Cyber Threat Summary Report published last month, the French National Agency for Information Systems Security (ANSSI) said it had observed attackers using similar commercial services to weaponize the security flaws of IVANTI Cloud Service Appliance (CSA) Security Fault (CSA) Security Fault (CVE-2024-2024-9380). Get control and execute arbitrary code.
“This moderately refined and modest intrusion set is characterized primarily by the use of intrusion tools available as open source and the use of rootkit codes that have already been reported publicly,” ANSSI said.
Note that the analysis of artifacts uploaded to Virustotal from China in October 2024 shows that both snow light and VShell can target Apple Macos systems, allowing the latter to be distributed as a fake CloudFlare Authenticator application.

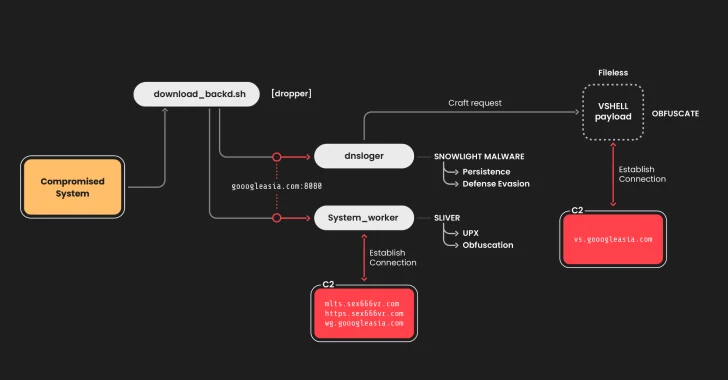
In the attack chain observed by Sysdig in late January 2025, Snowlight malware acts as a dropper for a useless, in-memory payload called Vshell, a remote access trojan (rat) widely used by Chinese cybercriminals. The initial access vector used for the attack is currently unknown.
Specifically, initial access is used to run a malicious Bash script (“Download_backd.sh”) that unfolds two binaries related to Snow Light (DNSLOGER) and Sliver (System_Worker).
The final stage of the attack uses specially created requests to the C2 server to provide VShell via snow light, thereby enabling remote control and further post-enhanced exploitation.
“[VShell] According to Rizzo, Rizzo said. Sysdig said it acts as a “remote access trojan), allowing abusers to run any command to download or upload files.

This disclosure is because TeamT5 has revealed that China and Nexus hacking groups likely exploited the security flaws in Ivanti appliances (CVE-2025-0282 and CVE-2025-22457) to initially access Spawnchimera Malware.
Taiwan’s cybersecurity company said the attack targeted a number of sectors across nearly 20 countries, including Austria, Australia, France, Spain, Japan, South Korea, the Netherlands, Singapore, Taiwan, the United Arab Emirates, the UK and the US.
The findings also resulted in the US National Security Agency’s launching a “advanced” cyberattack at the Asian Winter Games in February, pointing at the fingers of three NSA agents, bringing repeated attacks on China’s critical information infrastructure and accusations against Howaway.
“In the 9th Asian Winter Game, the US government carried out a cyberattack on the game’s information systems and the key information infrastructure in Edo,” said Lin Jiang, a spokesman for the Ministry of Foreign Affairs. “This move is awful as it seriously puts China’s critical information infrastructure, national defense, fiscal, social, production safety, and the safety of citizens’ personal information.”
Source link