Cybersecurity researchers have warned about a massive phishing campaign targeting WooCommerce users, prompting them to download “critical patches” with fake security alerts, but instead deploying backdoors.
WordPress Security Company PatchStack described the activity as a refined variant of another campaign observed in December 2023, employing a fake CVE trick to violate sites running popular content management systems (CMS).
Given the similarities between phishing email lures, fake web pages, and the same methods employed to hide malware, the latest attack wave is considered to be either the work of the same threat actor or a new cluster that closely mimics the previous one.

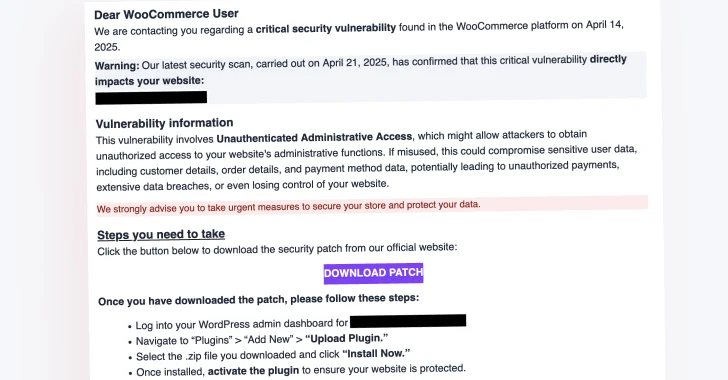
“They claim that targeted websites are affected by the (non-existent) “Unrecognized Administrative Access” vulnerability, urging them to use IDN homograph attacks to access phishing websites that disguise themselves as official Woocommerce websites,” Chazz Wolcott said.
Phishing email recipients are recommended to click on the Download Patch link to download and install the expected security fixes. But in doing so, you will redirect them to a page in a spoofed woocommerce marketplace hosted in your domain[.]com ” (note the use of “ė” instead of “e”) can download the zip archive (“authbypass-update-31297-id.zip “).

The victim is then asked to install the patch to install the regular WordPress plugin, effectively unlocking the following series of malicious actions –
After configuring a randomly specified Cron job that sends an HTTP Get Request to the Aust Run Server (“woocommerce-services,” create a new admin-level user with an obfuscated username and a randomized password.[.]com/wpapi “) Send http get request along with information about the username and password, along with URL of the infected website, to download the next stage obfuscation payload from the second server (woocommerce-help[.]com/activate “or” woocommerce-api[.]com/activate”) Decode the payload to extract multiple web shells like Pas-fork, P0WNY, WSO, etc. Hide malicious plugins from list of plugins

The ultimate result of the campaign is that it allows attackers to remote the website, inject spam or rough ads, redirect site visitors to a rogue site, register compromised servers in a botnet to carry out DDOS attacks, and even encrypt server resources as part of a long extension scheme.
Users are advised to scan suspicious plugins or administrator accounts to ensure that the software is up to date.
Source link