The second security flaw affecting the WordPress plugin of Ottokit (formerly Suretriggers) is undergoing aggressive exploitation in the wild.
The vulnerability tracked as CVE-2025-27007 (CVSS score: 9.8) is a privilege escalation bug that affects all versions of the plugin before and after version 1.0.82.
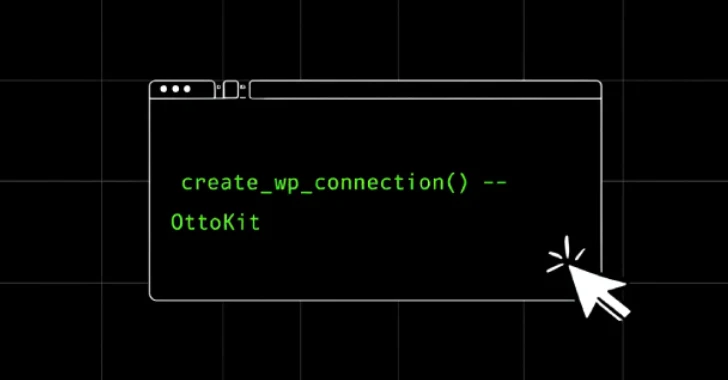
“This is because the create_wp_connection() feature lacks feature checks and insufficient user authentication credential verification,” Wordfence said. “This allows unrecognized attackers to establish connections and ultimately allow privilege escalation.”
That said, vulnerabilities are only exploited in two possible scenarios –
If the site has never validated or used an application password, Ottokit has not yet been connected to the website using the application password before the attacker authenticates access to the site and generates a valid application password
WordFence revealed that it observed that threat actors attempting to exploit the initial connection vulnerability to establish a connection with the site and using it to create an administrative user account via an automation/action endpoint.

Furthermore, the attack is aiming for CVE-2025-3102 (CVSS score: 8.1).
This increases the likelihood that threat actors will opportunistically scan WordPress installations to see if they are susceptible to one of the two flaws. Below are the observed IP addresses targeting vulnerabilities –
2A0B: 4141:820:1F4 :: 2 41.216.188.205 144.91.119.115 194.87.29.57 196.251.69.118 107.189.29.12 205.185.123.102 198.98.51.24 198.98.52.226
Given that the plugin has over 100,000 active installations, it is essential that users move quickly to apply the latest patch (version 1.0.83).
“Attackers may have begun to actively target this vulnerability on May 2, 2025.
Source link