It has been observed that Nation-State threat actors, known as Mirrorface, are deploying malware called RoamingMouse as part of cyberspy activities directed to government and public agencies in Japan and Taiwan.
Activities detected in Trend Micro in March 2025 included the use of a spearfishing racker to provide an updated version of the backdoor called Anel.
“The ANEL file for the 2025 campaign discussed in this blog has implemented a new command to support the execution of BOFs (beacon object files) in memory,” says security researcher Hara Hiroaki. “This campaign could also utilize Sharpd to launch a second-phase backdoor Noopdoor.”
The China-lined threat actors, also known as Earthkasha, are rated as subclusters within APT10. In March 2025, ESET shed light on a campaign called Operation Akairyū in August 2024 targeting Anel (aka Uppercut) and diplomatic organisations in the European Union.

Targeting various entities in Japan and Taiwan points to a continuous expansion of footprints as hacking crews seek to carry out information theft to advance their strategic goals.
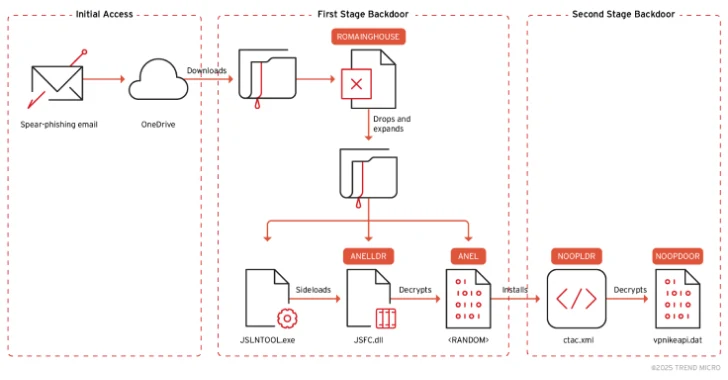
The attack begins with a spear phishing email – some of it is sent from a legal but compromised account – contains an embedded Microsoft OneDrive URL, which downloads a ZIP file.
The ZIP archive contains malware-covered Excel documents and RoamingMouse, a macro-enabled dropper codename that acts as a conduit to deliver components related to ANEL. It is worth noting that Roaming Mouse has been used by Mirrorface since last year.
“RoamingMouse uses Base64 to decode embedded ZIP files, drop zips on disk, and extend the components,” says Hiroaki. This is –
jslntool.exe, jstiie.exe, or jsvwmng.exe (legal binary) JSFC.dll (aneldr) Encrypted ANEL payload MSVCR100.dll (legal DLL dependencies for executables)
The ultimate goal of the attack chain is to launch a legitimate executable using Explorer.exe and use it to remove malicious DLLs, in this case Aneldr.
What’s noteworthy about the ANEL artifact used in the 2025 campaign is that it adds new commands with new commands to support in-memory execution of Beacon Object Files (BOFS). It compiles a C program designed to extend the Cobalt Strike Agent with new post-explosion functionality.
“After installing the ANEL file, the actor behind Earth Kasha used backdoor commands to take screenshots and examine the victim’s environment,” explained Trend Micro. “The enemy appears to be looking at screenshots, running a process list, examining domain information to investigate victims.”

It also leverages an open source tool named Sharphide to use the selected instance to launch another new backdoor version of Noopdoor (aka Hiddenface), which was previously identified as used by Hacking Group. The implant supports DNS-over-HTTPS (DOH) for that part, hiding IP address searches during command and control (C2) operations.
“Earthkasha continues to be an aggressive, highly sustained threat, and is currently targeting government and public institutions and public institutions at Taiwan and Japan in its latest campaign detected in March 2025,” Hiroaki said.
“Companies and organizations, particularly those with high value assets such as governance-related sensitive data, intellectual property, infrastructure data, and access credentials, should remain vigilant and implement proactive security measures to prevent victims of cyberattacks.”
Source link