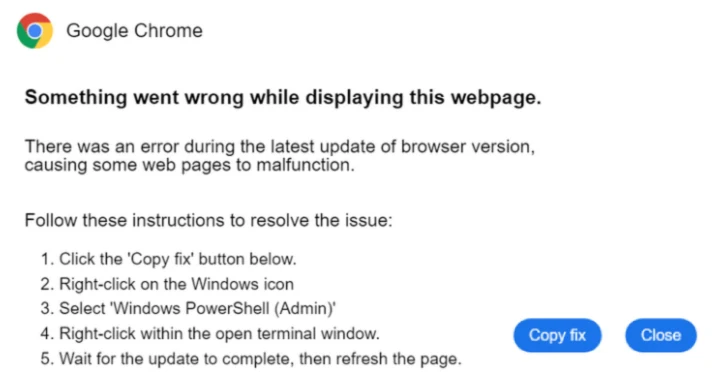
The malware known as Latrodectus is the latest to embrace a widely used social engineering technology called Clickfix as a distribution vector.
“Clickfix techniques are particularly dangerous because malware can be run in memory rather than being written to disk,” the report shared with Hacker News states. “This will give you more opportunities for browsers and security tools to detect or block malware.”
Latrodectus, considered to be the successor to IcedID, is a name given to malware that acts as a downloader for other payloads, such as ransomware. It was first documented in April 2024 by ProofPoint and Team Cymru.
Incidentally, this malware is one of many malicious software that suffers operational setbacks as part of the operational Endgame, defeating 300 servers around the world, 650 domains related to Bumblebee, lacrotectus, Qakbot, Hijackloader, Danabot, Trickbot and Warmcokie on May 19th, 2025.

In the latest set of Latrodectus attacks observed by Expel in May 2025, unsuspecting users will be tricked into copying and running PowerShell commands from infected websites.
“When a user runs these commands use MSIEXEC to install files at the remote URL and try to run them in memory,” Expel said. “This eliminates the need for attackers to write files to their computers and runs the risk of being detected by antiviruses that could be detected on a browser or disk.”
The MSI installer contains legitimate NVIDIA applications that are used to sideload malicious DLLs. This will use Curl to download the main payload.
To mitigate this type of attack, we recommend using Group Policy Objects (GPOs) to disable the Windows Run program or turning off the “Windows+R” hotkey via changes to the Windows registry.
From Clickfix to Tiktok
This disclosure comes when Trend Micro reveals details about its new engineering campaign. This revealed that instead of relying on fake Captcha pages, it is likely to provide Vidar and StealC information steel by instructing users to run malicious commands on systems to activate Windows, Microsoft Office, Capcut, and Spotify using Tiktok videos generated using artificial intelligence (AI) tools.

These videos have been posted from various Tiktok accounts such as @gitallowed, @zane.houghton, @allaivo2, @sysglow.wow, @alexfixpc, and @digitaldreams771. These accounts are no longer active. One video claiming to provide instructions on how to “improve your Spotify experience instantly” has accumulated almost 500,000 views with over 20,000 likes and over 100 comments.
This campaign marks a new escalation of Clickfix in that it is visually guided by users searching for how to activate pirated apps, and is visually guided to open Windows Run dialogs by launching “Windows + R” hotkey, PowerShell, running highlighted commands in the video, and ultimately registering your own system.
“Threat Actors is currently running Powershell commands to use social engineer users using Tiktok videos that are potentially generated using tools with AI to use social engineer users to activate legitimate software or unleash premium features.”
“The campaign highlights that attackers are ready to weaponize the currently popular social media platforms for distributing malware.”
Fake ledger app used to steal seed phrases for Mac users
The findings continue to discover four different malware campaigns that leverage the cloned version of the Ledger Live app to steal sensitive data, such as seed phrases, with the goal of ejecting victims’ cryptocurrency wallets. Activities have been continuing since August 2024.

The attack uses a malicious DMG file that launches Applescript on startup to remove passwords and Apple note data and downloads the Trojanized version of Ledger Live. When the app is opened, it warns users of expected account issues and warns that seed phrases are required for recovery. The seed phrase entered is sent to the attacker control server.
MoonLock Lab, which shed light on the campaign, said the Rogue app uses Macos Stealer Malware, such as Atomic Macos Stealer (AMOS) and Odyssey.
“The dark web forum has grown chat about anti-leisure schemes. The next wave is already in shape,” says MacPaw’s cybersecurity department. “Hackers will continue to utilize the ownership trust of Crypto, which is located in Ledger Live.”
Source link