Google has stepped in to allow you to brute your account’s recovery phone number and address security flaws that could be exposed to privacy and security risks.
This issue leverages an issue with our account recovery capabilities, according to Singapore’s security researcher Brutecat.
That said, it exploits the vulnerability on some moving parts, particularly targeting the now-restrained version of Google Username Recovery Form (“accounts.google”[.]com/signin/usernamerecovery “) There was no abuse prevention prevention designed to prevent spam requests.
The page in question is designed to allow users to check if a recovery email or phone number is associated with a specific display name (e.g. “John Smith”).

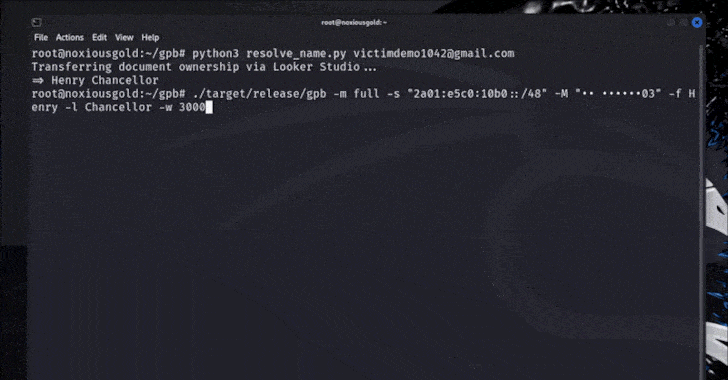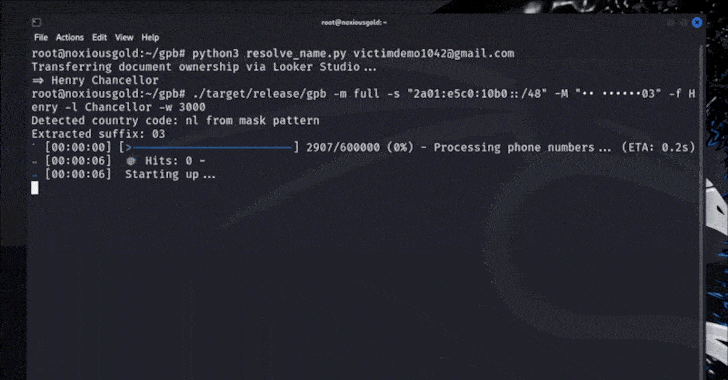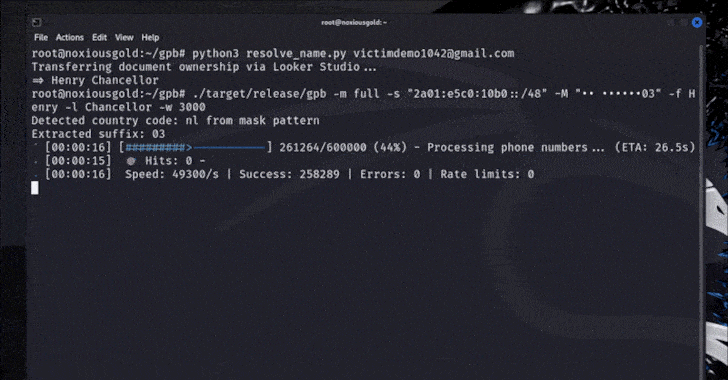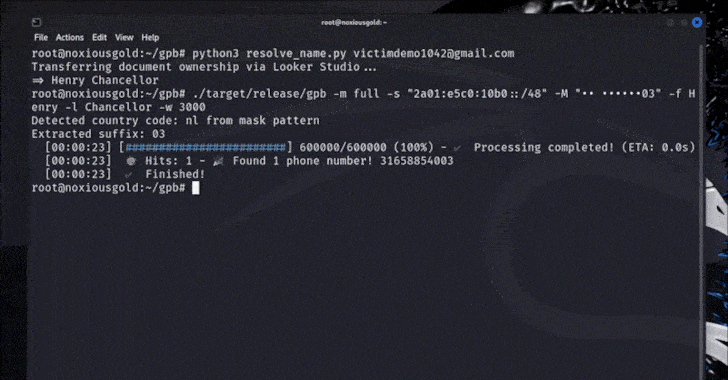
But bypassing Captcha-based rate limiting, it was finally possible to try all the permutations of Google account phone numbers in a short time, depending on the length of the phone number (depending on the country) to reach the correct number in seconds or minutes.
Additionally, attackers can use Google’s forgotten password flow to get display names by knowing the country code associated with the victim’s phone number, creating Looker Studio documents, transferring ownership to the victim, or leaking the full name to the homepage.
Overall, the exploit needs to do the following steps –
Appearance Leaks Google Account Display Name via Studio Run the forgotten password flow for the target email address to get the phone number masked with the last two digits that will be displayed to the attacker (e.g. •••• 03) Brute Force
Brutecat said the Singapore-based figures could leak the aforementioned techniques in five seconds, but the US numbers could be masked in about 20 minutes.
Armed with knowledge of the phone number associated with a Google account, bad actors can control it through SIM swap attacks and ultimately reset the password for the account associated with that phone number.
Following the responsible disclosure on April 14, 2025, Google awarded researchers a $5,000 bug bounty and plugged in the vulnerability by completely removing the recovery form for non-JavaScript usernames as of June 6, 2025.
The findings come months after the same researcher could check the YouTube API for flaws and expose the weapon to expose the YouTube channel owner’s email address to the outdated web API associated with the Pixel Recorder.

Then, in March, brutecat revealed that it is possible to leverage access control issues with the “/get_creator_channels” endpoint to collect email addresses belonging to creators who are part of the YouTube Partner Program (YPP).
“[An] Access control issues with access control issues leak Channel ContentOwnAssociation. This leads to disclosure of channel email addresses through the Content ID API,” Google said.
“Attackers who have access to Google accounts with channels that have joined the YouTube Partner Program (over 3 million channels) can get details of monetization for other channels in the YouTube Partner Program. Attackers can use this to unlock YouTubers (as YouTube has pseudo-anonymity predictions),
Source link