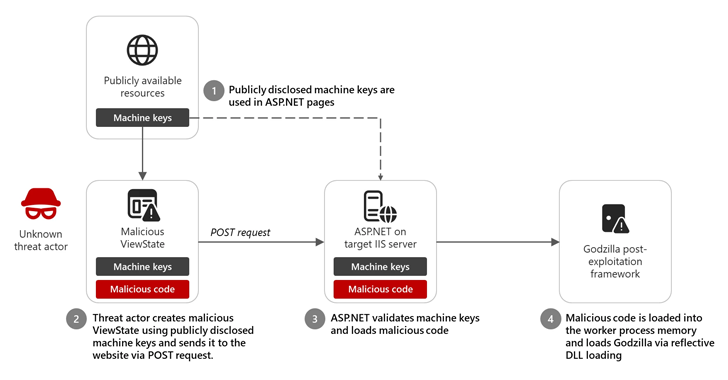
Microsoft is warning of unstable practices that software developers incorporate published ASP.NET machine keys from published resources, thereby posting applications in attacker routes.
Tech Giant’s Threat Intelligence team in December 2024 injected malicious code using publicly available static ASP.NET machine keys to provide a post-Godzilla post-explosion framework He said he observed limited activities, including threat actors.
It also states that it identifies over 3,000 public keys that can be used for these types of attacks.

“Many previously known view state code injection attacks used compromised or stolen keys that are often sold in dark web forums, but these published keys are available in multiple code repositories. It could pose a higher risk because it was pushed into development code without any changes, Microsoft said.
ViewState is a method used by the ASP.NET framework to control the values between pages and postbacks. This can also include application data specific to the page.
“By default, the display state data is saved to a page in a hidden field and is encoded using Base64 encoding,” Microsoft notes in the documentation. “In addition, a hash of View State data is created from the data using a machine authentication code (MAC) key. The hash value is added to the encoded View State data, and the resulting string is saved to the page. .”
When using hash values, it is important to ensure that the view state data has not been corrupted or tampered with by a malicious actor. That said, if these keys are stolen or allow access to illicit third parties, then in a scenario where threat actors can leverage the key to send malicious ViewState requests and execute arbitrary code. Open the door.
“When a request is processed by the target server’s ASP.NET runtime, the appropriate key is used, so ViewState is decrypted and verified,” Redmond said. “The malicious code is then loaded into worker process memory and executed to provide the threat actor remote code execution capability to the target IIS web server.”
Microsoft provided a list of hash values for publicly available machine keys, prompting customers to check for the machine keys used in their environment. It also warns that rotating the key is not sufficient if publicly available key exploitation is successful, as threat actors may already have established host persistence.
To mitigate the risk poses from such attacks, we recommend not copying keys from public sources and rotating them regularly. As a further step to stop threat actors, Microsoft said it had removed important artifacts from the “limited instances” contained in the document.

The development comes as cloud security company Aqua reveals details about the OPA gatekeeper bypass that could be exploited to carry out rogue actions in Kubernetes environments, including the deployment of rogue container images.
“In the K8SallowedRepos policy, security risks arise from how REGO logic is written in the ConstraintTemplate file,” researchers Yakir Kadkoda and Assaf Morag state in an analysis shared with Hacker News. I’m here.
“This risk is further amplified when users define values in the constraint YAML file that do not match how REGO logic handles them. This mismatch results in policy bypassing and does not have an effective limit.”
Source link