New York, New York, February 11, 2025, Chain Wire
SEDA has announced the Interoperability Verification Module (IVM) framework to set the industry standard for cross-chain verification of all routes across VMs.
Today, SEDA announced its first interoperability verification module framework. SEDA IVMS is a plug-and-play verification solution for interoperability protocols, adding significantly upgraded security, instick proximity horizontal scaling, and increased decentralization from the box. Interoperability providers that integrate SEDA IVMs have access to a hyper-specialized framework for independent, unauthorized verification of cross-chain transactions across all routes. The SEDA IVM framework is built to provide the modularization of the interoperability architecture needed to expand from the current landscape of 347 active networks to an estimated 2,000 chains by 2026.
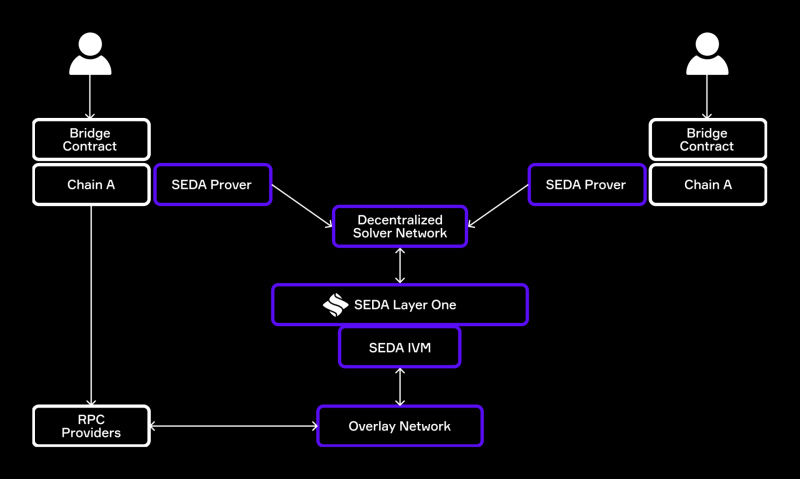
The IVM framework leverages a multi-tier verification process consisting of a combination of independent overlay networks, distributed solvers, and private and public RPC data providers. Having lost nearly $2 billion in bridge hacking since 2020, SEDA IVM presents a key part of the security infrastructure needed by the industry. Built to provide robust, scalable and customizable modules, IVM offers independent distributed validation for millions of transactions across thousands of networks.
The main features and benefits of SEDA IVM are:
Industry-wide data parity with unique security zones. Integrated activity guarantee. Programmable design for the specific needs of bridges, solvers and abstraction layers. Unauthorized access and deployment.
“We’re looking forward to seeing you in the future,” said Peter Mitchell, CEO and co-founder of Seda. “In the last two years, the interoperability sector has expanded dramatically, reaching trading volumes of over $123 billion in 2024. This sector could exceed $250 billion in 2025. SEDA IVM A provider that customizes parameters within the framework and ensures independent validation across all routes through one deployment.”
In parallel with messages relayed between chains, the IVM automatically initiates a secure validation sequence. In this sequence, a dedicated secret committee of independent overlay nodes is formed to query the RPC data of the source chain. The results are returned by the Commit Levier scheme to prevent data integrity and manipulation. The protocol definition instructions then filter and order the results before they are batched in the main chain of SEDA. Data results are protected with tamper-proof encryption guarantees before the solver relays to the destination chain.
SEDA IVM directly addresses recent industry challenges, such as Stargate Bridge downtime caused by offline multi-SIG verifiers. By connecting to SEDA’s distributed validation architecture, interoperability providers inherit the security and vibrancy guarantees associated with SEDA’s network design, consisting of Layer 1 of Performance, Distributed Overlay Networks, and Censorship Resistant Solver Networks. I will. This design mitigates the collusion risks and downtime commonly associated with default multi-SIG relay setups, ensuring monthly volumes of over $10 billion.
By isolating validation, interoperability providers can focus on scaling services to thousands of new chains, and SEDA can provide special validation for all routes.
For more information about SEDA’s IVM framework and integration possibilities, users can join the community by visiting https://seda.xyz or by Discord at https://discord.gg/seda.
About Seda
SEDA is a programmable Oracle infrastructure that enables builders on any network to connect application-specific data feeds in seconds.
contact
Marketing Manager
Matthew Peters
Seda
matt@seda.xyz
Source link

