Since August 2024, Microsoft has been paying attention to an emerging threat cluster called Storm-2372, which is attributed to a new set of cyberattacks targeting various sectors.
The attacks target the governments in Europe, North America, Africa and the Middle Ages, non-governmental organizations (NGOs), information technology (IT) services and technology, defense, telecommunications, higher education, and energy/oil and gas sectors. east.
It has been observed that moderately confidently assessed threat actors to align with Russian interests, victims and commerce are targeted to users through messaging apps such as WhatsApp, Signal, and Microsoft teams. It’s there. I’ll try to build trust.

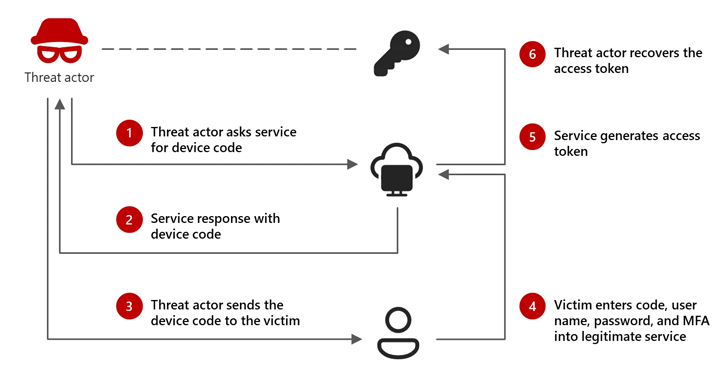
“Attacks use a specific phishing technique called “device code phishing” to trick users into logging in to productivity apps, and logins that Storm-2372 actors can use to access compromised accounts. Captures information from (tokens),” Microsoft Threat Intelligence said in a new report.
The goal is to leverage authentication codes obtained through methods to access the target account, misuse that access to keep sensitive data as long as the token is valid and persistent to the victim environment. It is to enable access to the site.
The tech giant sends a phishing email that pretends to be a Microsoft team that meets an invitation to authenticate message recipients using device code generated by threat actors when clicked It said it includes that. token.

“During an attack, the threat actor generates legitimate device code requests and tricks the target into entering it on a legitimate sign-in page,” explained Microsoft. “This gives actor access, allows them to capture generated authentications (access and updates), and use those tokens to access the target’s accounts and data.”
You can use the Fish Authentication Token to access other services that users already have permission, such as email and cloud storage, without the need for a password.

Microsoft said that a valid session is used to move horizontally within the network by sending similar phishing to other users from a compromised account. Additionally, Microsoft Graph Service is used to search for messages for violated accounts.
“Threat actors were using keyword searches to display messages containing words such as username, password, administrator, TeamViewer, AnyDesk, credentials, secrets, ministries, and Gov,” Redmond said. , added emails that match these filter criteria. A threat actor.
To mitigate the risks posed by such attacks, organizations should block device code flows wherever possible, enable phishing-resistant multi-factor authentication (MFA) and follow the principle of minimal privilege. I recommend it.
Source link