Virtual Tour Framework Cross-Site Scripting (XSS) vulnerability is to inject malicious scripts into hundreds of websites with the aim of manipulating search results and promoting large-scale spam ADS campaigns. It has been weaponized by malicious actors.
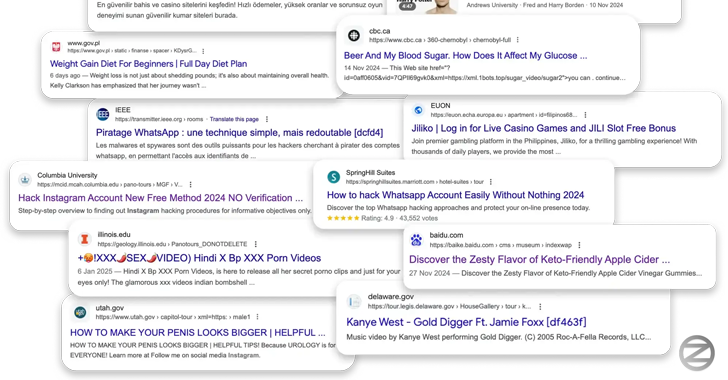
Security researcher Oleg Zaitsev, in a report shared with Hacker News, said the campaign (called 360XSS) was a source of government portals, US government sites, American universities, major hotel chains, news outlets, car dealers and more. said it had affected over 350 websites. Fortune 500 companies.
“This wasn’t just a spam manipulation,” the researchers said. “It was an industrial-scale abuse of a trustworthy domain.”
All of these websites have one thing in common. It is a popular framework called Krpano, which is used to embed 360° images and videos and promote interactive virtual tours and VR experiences.
Zaytsev came across a campaign after encountering porn-related ads listed in Google Search, but the domain associated with Yale University (virtualtour.quantuminstitute.yale[.]edu “).

A notable aspect of these URLs is the XML parameters designed to redirect site visitors to a second URL belonging to another legitimate website. This is used to run base64 encoded payloads via XML documents. The decoded payload retrieves the target URL (i.e., ads) for that part from yet another legitimate site.
The XML parameters passed in the original URL provided in the search results are part of a wide range of configuration settings named “PasqueryParameters” that is used when embedding Krpano Panorama Viewer into HTML pages. It is specially designed to pass HTTP parameters from URL to Viewer.
The security issue here is that if the option is enabled, URLs created specifically for attackers to run malicious scripts in the victim’s web browser when a vulnerable site is visited It is to open the door to a scenario where you can use it.
In fact, the reflected XSS defects resulting from this behavior were disclosed in KRPANO in the second half of 2020 (CVE-2020-24901, CVSS score: 6.1).
The update introduced in version 1.20.10 attempts to restrict “passquery parameters” to Alowlist and prevent such XSS attacks from occurring, but Zaytsev explicitly explicitly responsively in Allowlist I discovered that I’d like to add.

“Since version 1.20.10, the default installation of Krpano has not been vulnerable,” the researcher told Hacker News in an email. “However, configuring PasqueryParameter in conjunction with XML parameters caused XSS risks due to external XML configuration via URL.”
“The abused versions I came across were mostly older versions, before version 1.20.10.”
The campaign, with each Zaytsev, has hijacked over 350 sites to exploit this weakness and provide rough ads related to porn, diet supplements, online casinos and fake news sites. Additionally, some of these pages have been weaponized to enhance the video view of YouTube.
This campaign is particularly noteworthy because it abuses the trust and credibility of legal domains that are prominently visible in search results. This is a technique called Search Engine Optimization (SEO) addiction, and is achieved by abusing the defects in XSS.
“Reflected XSS is a fun vulnerability, but it requires user interaction in itself, and one of the biggest challenges is that people click on your reflective XSS link,” Zaytsev said. Masu. “So using a search engine as a distribution platform for XSS is a very creative and cool way to do that.”

Following responsible disclosure, the latest release of KRPANO eliminates support for external configuration via XML parameters, thereby reducing the risk of XSS attacks even when settings are used.
“Improved embedPano() PassqueryParameters security: Data-URL and external URLs are generally no longer allowed as parameter values, and the URLs for XML parameters are restricted within the current folder structure,” and release notes for version 1.22.4. According to this week.
Rather than carrying out more difficult attacks such as qualifications and cookie theft, the abuse of XSS flaws can help merely redirect, so the person behind the large operation is currently unknown, but we provide services to these It increases the likelihood of advertising companies with suspicious practices. Advertising as a monetization strategy.
Krpano users are recommended to update their installation to the latest version and set the “PasqueryParameters” setting to False. It is recommended that affected website owners find and delete infected pages via the Google Search Console.
Source link