The Commvault Command Center discloses important security flaws that allow arbitrary code execution in affected installations.
The vulnerability tracked as CVE-2025-34028 carries a CVSS score of up to 9.0 out of 10.0.
“A critical security vulnerability has been identified in the Command Center installation, allowing remote attackers to execute arbitrary code without authentication,” Commvault said in an advisory published on April 17, 2025.

It affected versions 11.38.0 to 11.38.19 to 11.38 innovation releases and was resolved in the next version –
Sonny MacDonald, a researcher at Watchtowr Labs, who was recognized as discovering and reporting the defect on April 7, 2025, said in a report shared by hacker news and that it could be exploited to achieve pre-recognized remote code execution.
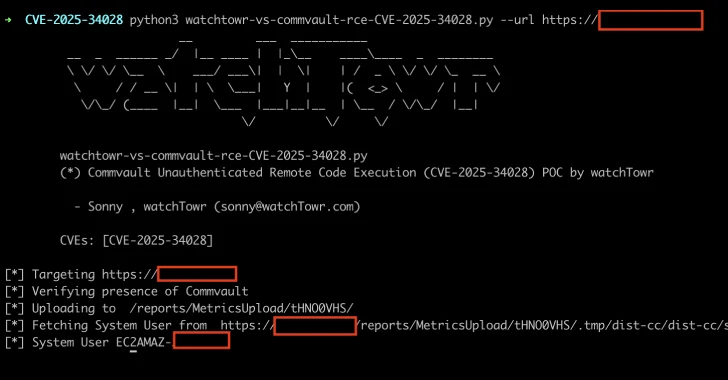
Specifically, this issue is rooted in an endpoint called “deploywebpackage.do” and triggers what is called pre-accepted server-side request forgery (SSRF) due to the fact that “there is no filtering about how the host can communicate with.”
Worse, code execution can be achieved by escalating the flaws in SSRF to use a ZIP archive file containing malicious .JSP files. The entire sequence of events is:
When you send an http request to /commandcenter/deploywebpackage.do, the commvault instance will retrieve the zip file from the contents of the external server in the zip file. Run the shell from /reports/metricsupload/shell/CommandCenter/DeployWebPackage.do SSRF to run the shell from /reports/metricsupload/shell/.tmp/dist-cc/dist-cc/shell.jsp

WatchTowr has created a detection artifact generator that organizations can use to determine if an instance is vulnerable to a vulnerability.
With vulnerabilities in backup and replication software such as Veeam and Nakivo undergoing active exploitation in the wild, it is essential for users to apply the mitigation they need to prevent potential threats.
Source link