Google announced on Wednesday that a Chinese-sponsored threat actor known as APT41 has leveraged a malware called ToughProgress, which uses Google Calendar for command and control (C2).
The tech giant, which discovered the activity in late October 2024, said the malware was hosted on a government website where it compromised and used to target several other government agencies.
“The misuse of C2 cloud services is a technique that many threat actors use to integrate with legitimate activities,” said Patrick Whitsell, a researcher at Google Threat Intelligence Group (GTIG).
APT41 is also tracked as Axiom, Blackfly, Brass Typhoon (formerly Barium), Bronze Atlas, Earthbac, Hoodoo, Red Kelpie, TA415, Evil Panda, and Winnty.

In July 2024, Google revealed that several entities operating in these industries, including Italy, Spain, Taiwan, Thailand, Turkey and the UK, are targeting “sustainable campaigns” using a combination of webshells and droppers, such as Antward, Blue Beam, Dust Pan and Dust Trap.
Then earlier this year, a subcluster within the APT41 umbrella was identified in March 2024 as attacking Japanese companies in the manufacturing, materials and energy sectors as part of a campaign called Revival Stone.
The latest attack chain documented by Google involves sending a spear phishing email containing a link to a ZIP archive hosted on the Exploided Government website. The ZIP file contains a directory that disguises itself as a PDF document and a Windows Shortcut (LNK). The directory features seven different images of arthropods (from “1.JPG” to “7.JPG”).
The infection begins when the LNK file is launched and presents the recipient with a decoy PDF that states that the species extracted from the directory must be declared for export. However, it is worth noting that “6.jpg” and “7.jpg” are fake images.

“The first file is actually an encrypted payload and is decrypted by the second file. This is a DLL file launched when the target clicks on LNK. Malware implements a variety of stealth and avoidance techniques, including memory-only payloads, encryption, compression, and control flow esoteric.
The malware consists of three different components, each deployed in series and designed to execute a specific function –
Plus Drop, DLL is used to decrypt and perform the next stage of Memory Plus Ingation.
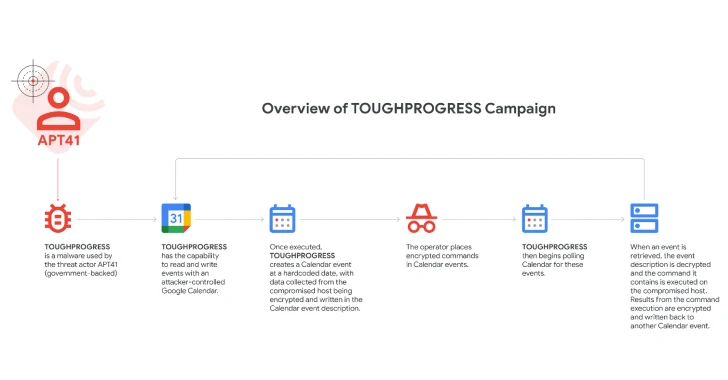
The malware is designed to read and write events using an attacker-controlled Google Calendar, creating zero mite events on hardcoded dates (2023-05-30) to store harvested data in event descriptions.
The operator places encrypted commands in the calendar event on July 30th and 31st, 2023, then voted by the malware, decrypted, and executed on a compromised Windows host, with the results written back to another calendar event that the attacker can extract.

Google said it took steps to remove malicious Google Calendar and ended the associated workspace project, thereby neutralizing the entire campaign. He also said that affected organizations have been notified. The exact scale of the campaign is unknown.
This is not the first time that APT41 has weaponized Google’s services in its favor. In April 2023, Google revealed that threat actors will target unknown Taiwanese media organizations and provide a GO-based open source red teaming tool known as Google Command and Control (GC2) that is delivered via password-protected files hosted on Google Drive.
Once installed, GC2 acts as a backdoor to read commands from Google Sheets and remove data using cloud storage services.
Source link