A threat actor known as Encrypthub has leveraged recently patched security vulnerabilities in Microsoft Windows as zero-days, offering a wide range of malware families, including backdoors and information steels such as Rhadamanthys and Stealc.
“In this attack, threat actors manipulate .MSC files and multilingual user interface paths (MUIPATH) to download and run malicious payloads, maintain persistence from infected systems and steal susceptibility data.”
The vulnerability in question is CVE-2025-26633 (CVSS score: 7.0), which Microsoft describes as an inappropriate neutralization vulnerability in the Microsoft Management Console (MMC), allowing attackers to bypass security features locally. It was revised earlier this month by the company as part of Tuesday’s update.

Trend Micro exploited MSC Eviltwin by tracking down a suspected Russian activity cluster under the name Water Gamayun. Threat Actors, the threat that has recently been analysed by Prodaft and Outpost24, is also known as larva-208.
CVE-2025-26633 leverages the Microsoft Management Console Framework (MMC) to run malicious Microsoft Console (.MSC) files using a PowerShell loader called the MSC Eviltwin Loader.
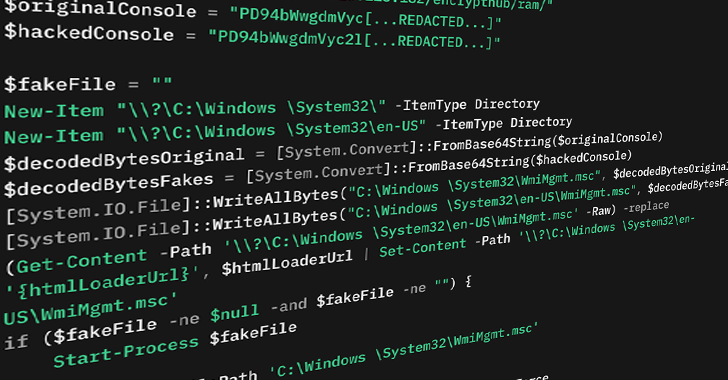
Specifically, it contains a loader that creates two .MSC files with the same name. One clean file will be dropped in the same location and in a directory named “En-US”. The idea is that when the former is executed, MMC inadvertently selects and executes malicious files instead. This is achieved by leveraging MMC’s Multilingual User Interface Path (MUIPATH) feature.

“By abusing the way MMC.exe uses Muipath, attackers can equip Muipath En-US with malicious .MSC files.
It has also been observed that Encrypthub uses two other methods to perform malicious payloads on infected systems using .msc files –
Use the executeShellCommand method in MMC to download and run the following step-by-step payload on the victim’s machine: This is a “note post-Windows space” that was previously documented by a Dutch cybersecurity company in August 2024 to bypass and drop user account controls using mock trusted directories such as “C:\Windows\System32”.

Trend Micro said the attack chain would likely start with victims downloading Microsoft Installer (MSI) files digitally signed to legitimate Chinese software such as DingTalk and QQTalk. The threat actor is said to have been experimenting with these techniques since April 2024.
“The campaign is actively developed. It employs multiple delivery methods and custom payloads designed to maintain persistence, steal sensitive data and extract it to attacker command and control (C&C) servers,” Zahravi said.
Source link