Cybersecurity researchers have warned about a new spear phishing campaign that uses a legitimate remote access tool called NetBird, targeting chief financial officers and financial executives of banks, energy companies, insurance companies and investment companies in Europe, Africa, Canada, the Middle East and South Asia.
“In what appears to be a multi-stage phishing task, the attacker aims to deploy Netbird, a legitimate wireguard-based remote access tool, on the victim’s computer,” Trellix researcher Srini Seethapathy said in the analysis.
Activities first detected by cybersecurity companies in mid-May 2025 are not attributable to known threat actors or groups.
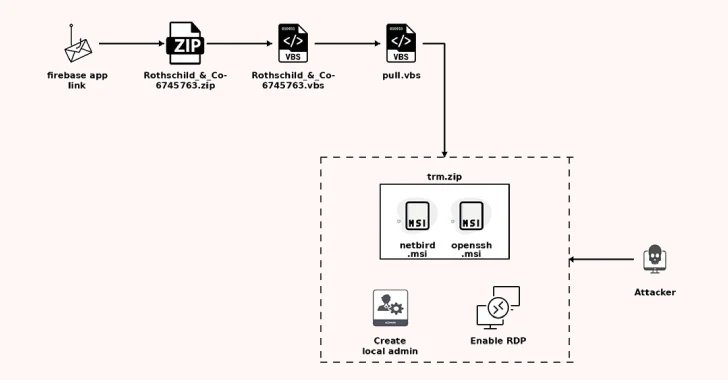
The starting point for the attack is Rothschild & Co. This is a phishing email that impersonates a recruiter for the company and claims it will provide “strategic opportunities” to the company. This email is designed to open PDF attachments to recipients. It’s actually a phishing link that redirects to the Firebase app host URL.
The notable thing about the infection is that the actual redirect URL is stored on the page in encrypted format, and can only be accessed after the victim resolves the Captcha validation check and ultimately leads to a ZIP archive download.
“It will be executed when you solve the puzzle [JavaScript] Seethapathy said it is “the ability to decrypt it with a hardcoded key and redirect the user to the decrypted link.”
What resides in the archive is a visual basic script (VBScript), which is responsible for getting the next stage VBScript from an external server and launching it via “wscript.exe”. This two-stage VBScript downloader gets another payload from the same server, changes it to “TR.ZIP” and extracts two MSI files from there: NetBird and OpenSSH.
The final phase involves installing two programs on the infected host, creating hidden local accounts, enabling remote desktop access, and persisting NetBird through a task scheduled to start automatically on a System restart. The malware also removes NetBird desktop shortcuts to prevent compromises from being detected by the victim.
Trellix has been active for nearly a year and identifies another redirect URL that provides the same VBScript payload, indicating that the campaign may have been around for some time.

The findings once again show that the enemy is increasingly dependent on legitimate remote access applications such as Connectwise Screenconnect, Atera, Splashtop, Fleetdeck, and Logmein.
“This attack isn’t your typical phishing scam,” Thetapathy said. “It’s well-made, targeted, subtle, designed to slip past technology and people. It’s a multi-stage attack where enemies use social engineering and defence evasion techniques to create and maintain permanent access to the victim system.”
This disclosure is consistent with the discovery of various email-based social engineering campaigns in the wild –
Attacks that abuse trusted domains related to famous Japanese Internet Service Providers (ISPs) send phishing messages from email addresses “Company@nifty[.]com “Get past email authentication checks, get past credentials that abuse Google Apps Script Development Platform, attempt harvest qualification attacks, host seemingly legitimate phishing pages, and steal Microsoft login credentials by using Microsoft-themed email lure attacks. It poses as if to display shared documents, takes victims to fake Microsoft login pages, portraying credentials via telegram bot attacks that exploit long-standing security flaws in Microsoft Office (CVE-2017-11882), hides Formbook Malware variations in fake PNG files, and provides Steal Steal Hosts from sensitive hosts.
PHAAS service lowers the bar
Findings also occurred, as Trustwave detailed the operational connections between Tycoon and Dadsec (aka Phoenix) phishing kits, highlighting the overlapping infrastructure and the use of centralized phishing infrastructure. DADSEC is a work of a threat actor tracked by Microsoft under the Moniker Storm-1575.
“The infrastructure used by DADSEC is also connected to new campaigns that leverage the Tycoon 2FA ‘Phishing-as-a-Service (PHAAS) platform,” said Cris Tomboc and King Orande of Trustwave Researchers. “The investigation into the Tycoon2FA phishing kit reveals how enemies continue to improve and expand tactics within the Service as a Phishing (PHAAS) ecosystem.”
 TYCOON 2FA PHAAS Operation
TYCOON 2FA PHAAS Operation
The growing popularity of PHAAS services is evidenced by the advent of a new “plug and play” Chinese kit called Haoji. It is estimated that by selling advertising to third-party services, it has driven more than $280,000 in the past five months criminal transactions. It works on a subscription basis for $2,000 a year.
“Unlike legacy phishing kits, where attackers need to manually configure scripts and infrastructure, Haozi offers sophisticated, public web panels,” Netcraft said. “When an attacker purchases a server and puts its credentials in a panel, the phishing software is automatically set up and does not need to run a single command.”
“This frictionless setup is in contrast to other PHAAS tools like the AI-enabled Darcula suite, which still requires minimal command line use.”
In addition to supporting an admin panel that allows users to manage all their campaigns in one place, Haozi has found it to provide advertising space. It acts as an intermediary that connects phishing kit buyers with third-party services, such as those related to SMS vendors.
 Haozi Phishing Dashboard
Haozi Phishing Dashboard
Another aspect that distinguishes Haozi from other kits is its dedicated after-sales telegram channel (@yuanbaoaichiyu).
“As enterprise security teams become more effective at detecting and dealing with intrusion attempts, attackers are deploying social engineering and phishing scams.
“The provision of PHAAS reduces skills floor and scale campaigns through automation and community support. These new models work more like a SaaS business than a black market hacking group with subscription pricing, customer service and product renewals.”

In an advisory published last week, Microsoft revealed how the PHAAS platform promotes enemy (AITM) qualification phishing, adopting a surge in Multi-Factor authentication (MFA).
Other techniques include device code phishing. OAuth consent phishing. Threat actors employ the Open Authentication (OAUTH) protocol and send emails with malicious consent links from third-party applications. The device participates in phishing. Here, the threat actor uses phishing links to trick the targets and allow the actor-controlled device domain binding.
Windows Maker said it observed suspected threat actors related to Russia employ third-party application messages or emails referring to future meeting invitations to provide malicious links with valid authorization codes. This technique was first documented by Volexity in April 2025.
“While both end users and automated security measures have a greater ability to identify malicious phishing attachments and links, motivated threat actors continue to rely on exploiting human behavior with persuasive lures,” said Igor Sakhnov, Corporate Vice President and Deputy CISO of Identity at Microsoft.
“Because these attacks depend on deceiving users, user training and recognition of commonly identified social engineering techniques are key to defending them.”
Source link