Palo Alto, California, May 29, 2025, CybernakeSweep
Today, Squarex has released a new threat research into advanced browser (BITM) attacks targeting Safari users. As Mandiant highlighted, enemies are using BITM attacks to steal credentials and gain unauthorized access to enterprise SaaS apps. BITM attacks work by using a remote browser to trick the victim into interacting with the attacker-controlled browser via the victim’s browser’s pop-up window. A typical BITM attack will display legitimate login pages for enterprise SAAS apps, deceive victims and reveal credentials and other sensitive information that they are working in regular browser windows.
Nevertheless, a flaw that BITM attacks have always had was the fact that the parent window would display malicious URLs and reduce the persuasiveness of attacks on secured users. However, as part of the year of the Browser Bug (YOBB) project, Squarex researchers have used full-screen APIs to highlight major implementation flaws inherent in Safari. When combined with BITM, this vulnerability can be exploited to create a highly convincing full-screen BITM attack. Here, the BITM window opens in full screen mode and does not display any suspicious URLs from the parent window. Safari users are particularly vulnerable to this attack because they do not have a clear visual indicator that users will enter full screen. We have revealed this vulnerability to Safari and unfortunately we are informed that there is no plan to address the issue.
The current full-screen API specifies that “the user must interact with the page or UI element for this feature to work.” However, what the API doesn’t specify is what interactions are required to trigger full screen mode. As a result, attackers can easily embed buttons such as fake login buttons in a pop-up that calls the full screen API on click. This triggers a full-screen BITM window that completely mimics a legitimate login page containing the URL displayed in the address bar.
“Full-screen BITM attacks highlight the architecture and design flaws of browser APIs, particularly full-screen APIs,” says a Squarex researcher. A visual clue that they are at a site controlled by the attacker.
While BITM attacks are primarily used to steal credentials, session tokens, and SAAS application data, the full-screen variant can lead to even more damage by making it easier for most regular enterprise users to recognize the attack. For example, landing sites may have buttons that claim to link to government resources, open to fake government advisory pages, spread misinformation and collect sensitive company and personally identifiable information (PII). The victim can then even open additional tabs in the attacker-controlled window, allowing the enemy to fully monitor the victim’s viewing activity.
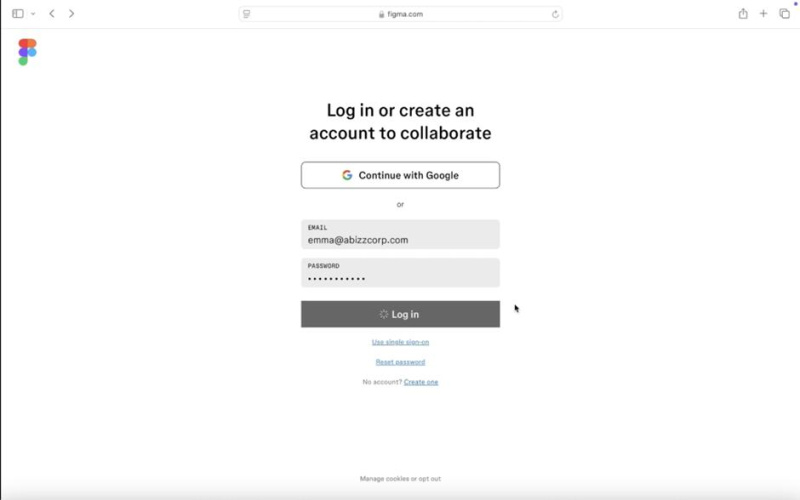 Fullscreen bit m window showing legitimate figma login page and URL in address bar (disclaimer: figma is used as an example)
Fullscreen bit m window showing legitimate figma login page and URL in address bar (disclaimer: figma is used as an example)
Are other browsers vulnerable to full-screen BITM attacks as well?
Unlike Safari, Firefox, Chrome, Edge, and other chrome-based browsers, a user message appears every time you switch fullscreen mode. However, this notice is inherently very subtle and instantaneous. Most employees will not notice or register this as a suspicious indication. Additionally, attackers can use dark modes and colors to make notifications even more conspicuous. In contrast, Safari does not have messaging requirements. The only visual indication that you can enter full screen mode is the “swipe” animation. So, while the attack does not show clear visual cues in the Safari browser, other browsers are also exposed to the same full-screen API vulnerability that allows for full-screen BITM attacks.
Existing security solutions cannot detect full-screen BITM attacks
Unfortunately, EDR has proven to be outdated when it comes to detecting BITM attacks with zero visibility. Additionally, you can bypass SASE/SSE detection by eliminating suspicious local traffic by tuning attacks with technologies such as remote browsers and pixel pushing. As a result, it is impossible for security tools to detect and mitigate full-screen bit attacks, as they do not have access to rich browser metrics. Therefore, if phishing attacks are more refined and leverage the architectural limitations of browser APIs and it takes a considerable amount of time for browser providers to fix them by browser providers, it is important for businesses to rethink their defense strategies to include sophisticated attacks like full-screen BITM in their browsers.
For more information about this security investigation, users can visit https://sqrx.com/fullscreen-bitm.
Squarex researchers held a webinar on June 5th at 10am Pt/1pm ET, delving deeper into the complete attack chain. To register, users can click here.
About squarex
SquareX is a browser detection and response (BDR) that can actively detect, mitigate, and effectively threaten client-side web attacks. Squarex provides critical protection against a wide range of browser security threats, including malicious browser extensions, advanced spear phishing, browser and native ransomware, and Genai DLP. Unlike legacy security approaches and tedious enterprise browsers, SquareX integrates seamlessly with your existing consumer browser, ensuring enhanced security without compromising the user’s experience or productivity. By delivering unparalleled visibility and control directly within the browser, SquareX allows security leaders to reduce attack surfaces, gain actionable intelligence, and enhance their enterprise cybersecurity stance towards the latest threat vector, browsers. Users can find out more at www.sqrx.com.
The disclosure of full-screen BITM attacks is part of the year of the Browser Bugs Project. Each month, Squarex research team releases major web attacks focusing on limiting the architecture of browsers and current security solutions. Previously disclosed attacks include browser SyncJacking, polymorphic extensions, and browser native ransomware.
For more information about Squarex’s BDR, users can contact squarex at founder@sqrx.com. For inquiries regarding this disclosure or reporting years of browser bugs, users can email junice@sqrx.com.
contact
PR manager
Junice Liew
squarex
junice@sqrx.com
🚀Want to share the story?
Submit your stories to TechStartUps.com in front of thousands of founders, investors, PE companies, tech executives, decision makers and tech leaders.
Please attract attention
Source link

