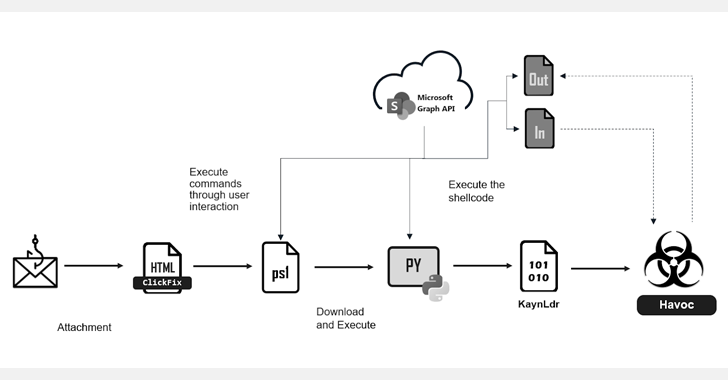
Cybersecurity researchers are turning their attention to a new phishing campaign that employs the Clickfix technique to provide an open source command and control (C2) framework called Havoc.
“Threat actors hide each malware stage behind SharePoint sites and use a modified version of Havoc Demon in conjunction with the Microsoft Graph API to obscure C2 communications within trusted and well-known services.”
The starting point for the attack is a phishing email containing HTML attachments (“documents.html”) that displays an error message when opened. Use the click fix technique to copy the user and run it to a terminal or powershell, then delete the next stage.

This command is designed to download and run PowerShell scripts hosted on an adversarial SharePoint server. If the newly downloaded PowerShell does not already exist on your system, checks whether it is running within a sandbox environment before downloading the Python interpreter (“Pythonw.exe”).

The next step is to get and run a Python script from the same SharePoint location that acts as the same SharePoint load, which acts as the shellcode loader for kaynldr written in C and ASM, which can launch embedded DLLs.
“Threat actors use Havoc in conjunction with the MicrosoftQ Graph API to hide C2 communications within famous services,” Fortinet said, supporting the framework to gather information, perform file operations, execute commands and payloads, token operations, and Kerberos attacks.
The development comes as MalwareBytes revealed that threat actors continue to exploit known loopholes in their Google Ads policies, targeting PayPal customers with fake ads provided through advertiser accounts that may have compromised.

The ads are trying to trick victims searching for payments in order to call fraudulent numbers that end up handing over personal and financial information, looking for assistance related to account issues or payment concerns.
“A weakness within Google’s policy of landing pages (also known as the final URL) allows anyone to impersonate a popular website as long as the landing pages and display URLs (web pages displayed in the ads) share the same domain,” says Jérôme Segura, senior director of research at Malware Bytes.
“Tech support scammers are like vultures circling above the most popular Google search terms, especially when it comes to all kinds of online support and customer service.”
Source link