The threat actors behind the Vextrio Viper Traffic Distribution Service (TDS) are linked to other TDS services, such as Help TD and disposable TDS, indicating that sophisticated cybercrime operations are their own vast enterprises designed to distribute malicious content.
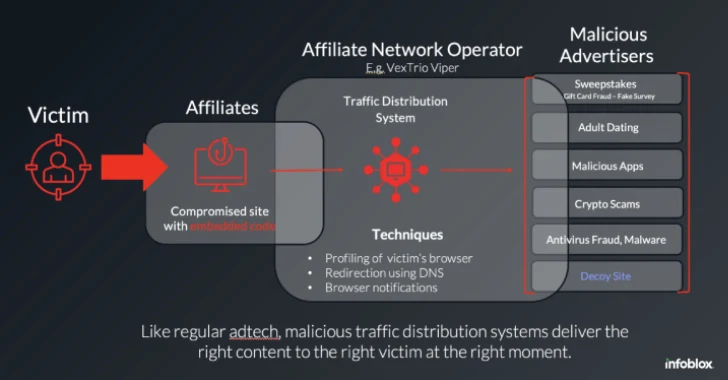
“Vextrio is a group of malicious Adtech companies that distribute fraud and harmful software through a variety of advertising formats, including SmartLinks and Push Notifications,” Infoblox said in a deep dive report that it shares with Hacker News.
Malicious Adtech companies under Vextrio Viper include Los Pollos, Taco Loco and Adtrafico. These companies operate what is known as commercial affiliate networks where users land and connect malware parties that connect websites illuminated by “advertising affiliates” with so-called “advertising affiliates” that provide various forms of illegal schemes, such as gift card fraud, malicious apps, phishing sites, and scams.

Put another way, these malicious traffic delivery systems are designed to redirect victims to their destinations through SmartLink or direct offers. According to DNS threat intelligence firm, Los Pollos involves malware distributors (aka affiliates) in their promise of high-paying offers, but Taco Loco specializes in pushnetization and is recruiting advertising affiliates.
Another notable element of these attacks is the compromise of WordPress websites injecting malicious code responsible for starting the redirect chain, which ultimately leads visitors to the Vextrio Scam Infrastructure. Examples of such injections include Balada, Dollyway, Sign1, and DNS TXT Records campaigns.
“These scripts redirect site visitors to various scam pages. The traffic broker network associated with Vextrio is one of the largest known cybercrime affiliate networks that leverage sophisticated DNS technologies, traffic distribution systems and domain generation algorithms to provide malware and fraud.
Vextrio’s operations were hit around mid-November 2024 after Qurium revealed that Swiss and Czech Adtech Company Los Pollos is part of Vextrio. This has caused escapes, and now moves threat actors who rely heavily on the LOS Pollos network to alternative redirect destinations such as Help TDs and disposable TDs.
An analysis of InfoBlox of 4.5 million DNS TXT record responses from compromised websites over six months revealed that domains that were part of the DNS TXT record campaign could be categorized into two sets, each with their own command and control (C2) servers.
“Both servers were hosted on infrastructure connected to Russia, but neither the hosting nor the TXT response was duplicated,” the company said. “Each set maintained a different redirect URL structure despite both being originally led by Vextrio and subsequently leading to HELT TDS.”
Further evidence has emerged that both the TDS and disposable TDs are identical, supporting the service enjoying an “exclusive relationship” with Vextrio until November 2024. HELTTDS has moved to Monetizer, a monetization platform where TDS, historically redirected to the Vextrio domain, uses TDS to connect to publisher affiliates.

“Help TDS has a strong Russian nexus, and hosting and domain registration is frequently done through Russian entities,” Infoblox said, describing the operator as perhaps independent. “There is no full-scale functionality of the Vextrio TDSS, and there is no obvious commercial connection beyond the creepy connection with Vextrio.”
Vextrio is one of many TDSs that have been out as a commercial ad tech company, others being Partner House, Blopsh, Richad, adm sin, and rexpush. Many of these are directed towards push notification services using Google Firebase Cloud Messaging (FCM). Alternatively, push an API-based custom development script to distribute links to malicious content via push notifications.

“Every year, hundreds of thousands of compromised websites around the world redirect victims to the intertwined web of vextrio and TDSS protecting vextrio,” the company said.
“Vextrio and other affiliate ad companies know who the malware actors are, or at least have enough information to track them. Many companies are registered in countries that require a certain amount of “know your customers” (KYC), but even without these requirements, public affiliates are reviewed by customer managers. ”
Source link