The North Korean threat actor behind the infectious interviews adopted Clickfix social engineering tactics, seducing job seekers in the cryptocurrency sector, and providing a previously undocumented Go-based backdoor called Golangghost on Windows and Macos systems.
The new activity, which was rated as a continuation of the campaign, is called a Clickfake interview with French cybersecurity company Sekoia. The infectious interviews, tracked as Deceptividedevelopment, Dev #Popper, and the famous Chollima, are known to have been active since at least December 2022, but only first published in late 2023.
“Use a legal job interview website to leverage Clickfix tactics and install windows and macos backgrounds,” said Sekoia researchers Amaury G., Coline Chavane, and Felix Aimé, belonging to the infamous Lazarus Group.
A notable aspect of the campaign is that it targets mainly centralized financial entities by impersonating companies such as Coinbase, Kucoin, Kraken, Circle, Securitize, Blockfi, Tether, Robinhood, and Bybit, and marking deviations from hacking groups’ distributed financial (DEFI) attacks.
Infectious interviews like Operation Dream Job employ fake jobs as Lure to attract future targets and download malware that can steal cryptocurrency and other sensitive data.
As part of the effort, candidates will approach via LinkedIn or X to prepare for video call interviews. This interview will ask you to download malware-covered video conferencing software or open source projects that activate the infection process.

The use of Clickfix tactics by the Lazarus Group was first disclosed by security researcher Taylor Monahan towards the end of 2024, with the attack chain leading to the deployment of a malware family known as Ferret, delivering Golang Backdoor.
In this campaign iteration, victims are asked to visit a video interview service named Willo and complete their own video evaluation.
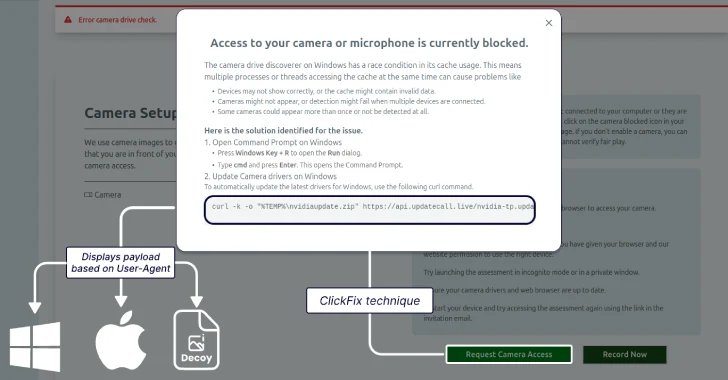
“The entire setup, meticulously designed to build user trust, goes smoothly until the user is asked to enable the camera,” explained Sekoia. “At this point, you will receive an error message indicating that the user must download the driver to fix the issue. This is where the operator will employ the Clickfix technique.”
The instructions given to the victim to allow access to the camera or microphone will vary depending on the operating system used. On Windows, the target opens a command prompt and is prompted to run the Curl command to run the Visual Basic Script (VBS) file, and launches a batch script that runs Golangghost.
If the victim is accessing the site from a MacOS machine, they will be prompted to launch the terminal app and run the Curl command to run the shell script. The malicious shell script runs a second shell script for that part, resulting in a steeler module called Frostyferret (aka Chromeupdatealert) and a backdoor.

Frostyferret displays a fake window indicating that the Chrome web browser needs to access the user’s camera or microphone, then prompts you to enter your system password. The information entered is surrounded by dropbox locations that are likely to indicate an attempt to access the iCloud keychain using a stolen password, whether it is valid or not.
Golangghost is designed to promote remote control and data theft via several commands that can upload/download files, send host information, and steal data from your web browser.
“We found that all positions have nothing to do with the technical profile in software development,” Sekia said. “They are managers’ jobs that focus primarily on business development, asset management, product development, or decentralized finance professionals.”
“This is a major shift from previous documented campaigns stemming from DPRK-Nexus threat actors, based primarily on fake job interviews targeting developers and software engineers.”
North Korean IT Workers Scheme works in Europe
The development comes as Google Threat Intelligence Group (GTIG) has observed a surge in illicit IT worker schemes in Europe, highlighting a significant expansion of operations beyond the US.
The activities of IT workers involve North Korean citizens pretending to be legitimate remote workers in violation of international sanctions, infiltrating businesses and generating illegal revenues in Pyongyang.
Increased awareness of the activities, coupled with the US Department of Justice indictment, incited “a global expansion of IT workers’ operations,” Google said, noting that it discovered several counterfeit personas seeking employment in various organizations in Germany and Portugal.
It has also been observed that IT workers are carrying out a variety of projects in the UK related to web development, bot development, content management systems (CMS) development, and blockchain technology, often claiming that they are from Italy, Japan, Malaysia, Singapore, Ukraine, the US and Vietnam.

This tactic of the workers, pretending to be the Nationals in Vietnam, Japan and Singapore, was highlighted earlier last month by managed intelligence company NISO, pointing to the use of Github to carve new personas and new personas to carve recycled portfolio content.
“European IT workers have been adopted through a variety of online platforms, including Upwork, Telegram and Freelancer,” said Jamie Collier, GTIG’s lead threat intelligence advisor. “Payment for their services was facilitated through cryptocurrency, Transferwise services, and Payoneer, highlighting the use of methods to obfuscate the origins of funds and destinations.”
In addition to using local facilitators to help land work, insider threat manipulation has witnessed the public knowing that since October 2024, these IT workers rely on ransom payments from their employers to free their own data or provide it to competitors.
What appears to be a further evolution of the scheme is said to be that IT workers are currently targeting companies that run customer device (BYOD) policies, as these devices are unlikely to use traditional security and logging tools in enterprise environments.
“Europe needs to wake up quickly. Despite being on the cross of IT workers’ operations, we see this too much as a US problem. The recent changes in North Korea are likely due to the US operational hurdles, indicating the agility of IT workers and the ability to adapt to changing circumstances,” Collier said.
“From rapid targeting and ransomware to cryptocurrency theft and supply chain compromises, there are 10 years of diverse cyberattacks ahead of North Korea’s latest surge. This relentless innovation demonstrates a long-standing commitment to funding the administration through cyber operations.”
Source link