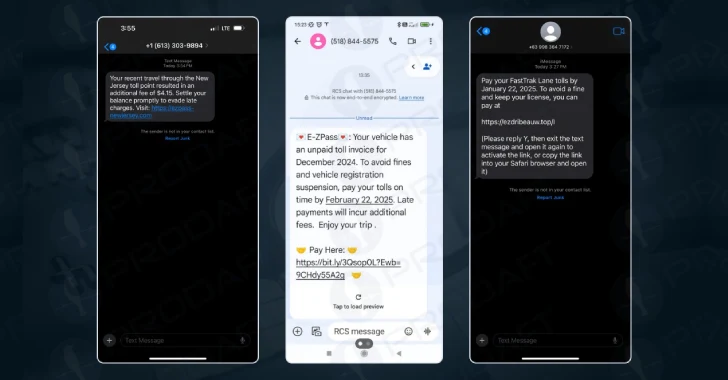
A new, sophisticated phishing (PHAAS) platform called Lucid targets 169 entities in 88 countries using smishing messages propagated through Android’s Apple Imessage and Rich Communication Services (RCS).
Lucid’s unique selling point is to weaponize a legitimate communications platform to avoid traditional SMS-based detection mechanisms.
“Its scalable subscription-based model allows cybercriminals to run large-scale phishing campaigns and harvest credit card details for financial fraud,” Swiss cybersecurity company Prodaft said in a technical report shared with Hacker News.
“Lucid leverages Apple Imessage and Android’s RCS technology to bypass traditional SMS spam filters, significantly increasing delivery and success.”
Lucid is credited as the job of a Chinese-speaking hacking crew called Xinxin Group (aka Black Technology), and phishing campaigns primarily target Europe, the UK and the US to steal credit card data and target personally identifiable information (PII).

The threats behind this service have, more importantly, developed other PhaAS platforms, such as Lighthouse and Darcula. The latter has the ability to clone the brand’s website to create a phishing version. Lucid’s developers are known as the codenames of threat actors who are also important figures in the Xinxin Group.
All three PHAAS platforms share overlaps of templates, target pools and tactics, hinting at a thriving underground economy where Chinese-speaking actors leverage telegrams to promote Wares on a subscription basis for profit-driven motivation.
Phishing campaigns that rely on these services have been found to provide sensitive information by impersonating postal services, courier companies, fee payment systems, and tax refund agencies, employing persuasive phishing templates to deceive victims.
Large activity powers the backend through a mobile device emulator running on iPhone device farms and Windows systems, sending hundreds of thousands of fraudulent messages containing fake links in a coordinated way. Targeted phone numbers are obtained in a variety of ways, such as data breaches and cybercrime forums.
“Because of the restrictions on clicking on links in Imessage, they employ the ‘Y’ technique to establish two-way communication,” explained Prodaft. “For Google’s RCS filtering, always rotate the send domain/number to avoid pattern recognition.”

“In the case of IMESSAGE, this creates a temporary Apple ID with the displayed display name, but RCS Exploitation takes advantage of the inconsistency in carrier implementation in verifying senders.”
In addition to providing automated tools to simplify the creation of customizable phishing websites, the page itself incorporates advanced detection and avoidance technologies such as IP blocking, user agent filtering, and time-limited single-use URLs.
Lucid also supports the ability to monitor victim activity and record any interaction with phishing links in real time via panels, allowing customers to extract inputted information. Credit card details submitted by the victim include additional verification steps. The panel is built using the open source Webman PHP framework.
“The Lucid Phaas panel has revealed a highly connected ecosystem as a service run by Chinese-speaking threat actors under the Xinxin group,” the company said.
“The Xinxin Group actively monitors and supports the development of similar PHAAS services, while developing and utilizing these tools and profits from the sale of stolen credit card information.”

It is noteworthy that Prodaft’s findings reflect the findings of the Palo Alto Networks Unit 42. It recently called unspecified threat actors to exploit the domain pattern “COM” and registered over 10,000 domains to propagate various SMS phishing scams via Apple Imessage.
The development has now come as Barracuda warned of “large spikes” in PHAAS attacks using Tycoon 2FA, EvilProxy and Sneaky 2FA in early 2025, warning that each service accounts for 89%, 8%, and 3% of all PHAAS incidents, respectively.
“Phishing emails are the gateway for many attacks, from qualification theft to financial fraud to ransomware,” said Direndra Prasad, a security researcher at Barracuda. “Platforms that power phishing as a service are increasingly complex and evasive, and phishing attacks become more and more powerful by traditional security tools to detect and deal damage.”
Source link