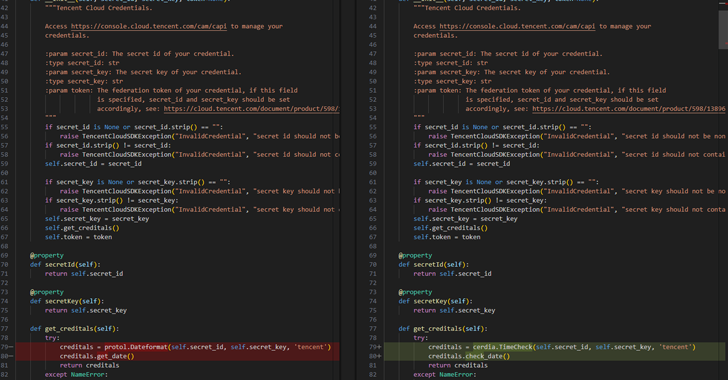
Cybersecurity researchers have fake libraries that disguise themselves as “time” related utilities for malicious campaigns targeting users of Python Package Index (PYPI) repository, but have hidden features to steal sensitive data, such as cloud access tokens.
Software supply chain security company ReverSinglabs said it has discovered a total of 20 sets of packages. The package has been downloaded cumulatively over 14,100 times –
Snapshot-Photo (2,448 downloads) Time Check Server (316 downloads) Time Check Server – Get (178 downloads) Time Server Analysis (144 downloads) Time Server Analyzer (74 downloads) Time Server Test (155 downloads) Download (151 downloads) (151 downloads) (5,496 downloads) Acloud-Clients (198 downloads) Acloud-Client-USES (294 downloads) Alicloud-Client (622 Downloads) Alicloud-Client-SDK (206 download) AMZCLIENTS-SDK (100 download) AWSCLOUD-CLIENTS-CORE (206 download) download) tclients-sdk (173 download) tcloud-python-sdks (98 download) tcloud-python-test (793 download)
The first set relates to the packages used to upload data to the threat actor’s infrastructure, while the second cluster consists of packages that implement cloud client functionality in several services, such as Alibaba Cloud, Amazon Web Services, and Tencent Cloud.

But they also use “time” related packages to remove cloud secrets. All identified packages have already been removed from Pypi at the time of writing.
Further analysis revealed that three packages, Acloud-Client, Enumer-IAM, and Tcloud-Python-Test, are listed as dependencies for a relatively popular Github project named AccessKey_tools, which have been forked 42 times and launched 519 times.

A source code commit was created on November 8, 2023 to reference Tcloud-Python-Test, indicating that the package can be downloaded in Pypi ever since. For each Pepy.tech statistics, the package has been downloaded 793 times so far.
This disclosure comes as Fortinet Fortiguard Labs said it discovered thousands of packages across Pypi and NPM. Some of them are known to include suspicious installation scripts designed to deploy malicious code during installation and communicate with external servers.
“Suspicious URLs are a key indicator of potentially malicious packages as they are used to download additional payloads, establish communication with command and control (C&C) servers, and are often used to control infected systems to attackers,” says Jenna Wang.
“In the 974 packages, such URLs are linked to the risk of data stripping, malware downloading, and other malicious actions. It is important to scrutinize and monitor external URLs of package dependencies to prevent exploitation.”
Source link