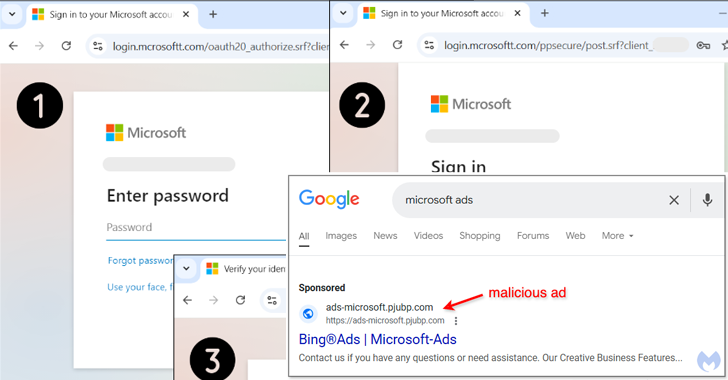
Cyber -security researchers aim to use Microsoft Advertisers to use Bogus Google ads to discover the Malvertising campaign and move to a fishing page where you can harvest qualifications.
「Google Searchに掲載されているこれらの悪意のある広告は、Microsoftの広告プラットフォームにアクセスしようとするユーザーのログイン情報を盗むように設計されています」と、MalwareBytesの研究担当シニアディレクターであるJérômeSegura氏はI mentioned in the report on Thursday.
The survey results occurred a week after the Cyber Security Company released a similar campaign with Google ads leveraged to target ads via a major search advertising platform.
The latest attack set targets users who search for terms such as “Microsoft ADS” in Google Search, and click on the search results page to a malicious link provided in the form of an advertisement with sponsor. Please decide.
At the same time, threats behind the campaign adopt some methods to avoid security tool detection. This includes traffic redirect from VPN. Site visitors will also provide cloud -free issues to exclude bots.

Last but not least, users who try to access the final landing page directly (“Ads.mcrosoftt)[.]COM “) is re -rolled by redirecting them to the YouTube video linked to the famous Internetmome.
The phishing page is a version like a legitimate counter part (“Ads.microsoft)[.]com “) This is designed to capture the login qualification information of the victim and the two -factor authentication (2FA) code, which gives the attacker a function to hire an account.
According to MalwareBytes, the Microsoft account has been specified a few years ago, and the campaign has been ongoing for a while, and other advertising platforms such as META may be targeted. It suggests.
Another notable aspect is that most of the fishing domains are hosted in Brazil or have the top -level domain in Brazil, the campaign for Google ADS users. Is similar to. Pt “TLD.
Hacker news contacted Google for comments, but the company had previously taken measures to ban hacker news, taking measures to prohibit advertising to trick users with the goal of stealing information. He said he is actively working to enforce. Such an effort.

Smithing Atttack will be USPS
This disclosure is the appearance of an SMS fishing campaign that uses a failed package distribution lure to target a mobile device user to be a US postal service (USPS).
“This campaign is a sophisticated social engineering tactic and a remarkable means that is more noticeable, stealing qualifications and designed to compromise confidential data. I will provide “
The message encourages the recipient to open the PDF file, update the address, and complete the distribution. What exists in the PDF document is to enter a mail address, e -mail address, and phone number in the “click update” button that instruct the victim to the USPS fishing web page.
The phishing page is also equipped to capture the details of the payment card, pretending to be re -distribution service charges. The entered data is encrypted and sent to the remote server under the control of the attacker. As part of the campaign, the largest malicious PDF and 630 phishing pages have been detected, indicating large -scale operations.
“The PDF used in this campaign has become more difficult to embed a link that can be clicked without using the standard /URI tag and extract the URL during the analysis,” said ORTEGA. 。 “With this method, a known malicious URL in the PDF file has been able to bypass detection by several endpoint security solutions.”
The activity indicates that cyber criminals use the security gap of mobile devices to bring out social engineering attacks that utilize users’ trust in popular brands and official communication.
A similar USPS -themed smashing attack was distributed using Apple’s iMessage. This is a technology that is known to be adopted by Chinese threat actor, SMISHING TRIAD.

Such messages skillfully try to prevent links from being able to click on links, unless the message is from a known sender or from an account that users reply. This is realized by including the message of “Please reply to Y” or “1” to turn off the incorporated phishing protection of IMESAGE.
It is noteworthy that this approach was previously associated with a phishing (Phaas) toolkit named Darcula. DARCULA is used to widely target postal services such as USPS and other established organizations in more than 100 countries.
“The scammers are building the attack relatively well, so it’s probably the reason why they are probably wild,” said Huntless researcher Truman Kane. “The simple truth is that it works.”
Source link