The subgroup within the infamous Russian state-sponsored hacking group known as Sandworm is attributed to a multi-year early access operation known as Bad Pilots, which spread all over the world.
“This subgroup has made globally diverse compromises on infrastructure for the Internet to enable Seashell Blizzard to maintain high value targets and support tailored network operations,” says Microsoft Threat The Intelligence team said in a new report shared with pre-published hacker news.
The geographical spread of the targets of the early access subgroups includes the entire North America, several European countries, and the like, including Angola, Argentina, Australia, China, Egypt, India, Kazakhstan, Myanmar, Nigeria, Pakistan, Turkey, and Turkey. Other countries include. Uzbekistan.
The development shows a significant expansion of the footprint of hacking group victims over the past three years.
2022: Ukraine’s Energy, Retail, Education, Consulting, Agriculture Sector 2023: US, Europe, Central Asia and the Middle East sectors provide significant support for wars in Ukraine or geopolitical significance 2024: US, Canada, Australia, UK
The sandworm is tracked by Microsoft under the moniker Seashell Blizzard (formerly Iridium) and is broader under the names Apt44, Blue Echidna, Frozenbarents, Gray Tornado, Iron Viking, Razing Ursa, Telebots, UAC-0002, and Voodoo Bear Tracked by the cybersecurity community. The group, which has been active since at least 2013, is rated as affiliated with 74,455 units within the main director of the general staff of the Russian Federation Forces (GRU).
Hostile groups are described by Google-owned Mandiant as “highly adaptive” and “operationally mature” threat actors engaged in spying, attacking and impact operations. It has also had a track record of increasing destructive and destructive attacks against Ukraine over the past decade.

The campaign that Sandulm launched in the wake of the Russo-Ukrainian war has included data wipers (Kildisk aka hermeticwiper), pseudo ransomware (Prestige aka prestea), and backdoor (Kapeka) in addition to the threat family, as well as threats. We took advantage of the backdoor (Kapeka) which allows us to keep key actors. Persistent remote access to infected hosts via DarkCrystal RAT (also known as DCRAT).
It has also been observed that it relies on various Russian companies and criminal markets to procure and maintain attack capabilities, highlighting the growth trends of cybercrime.
“The group uses criminally sourced tools and infrastructure as a source of disposable features that can be operated in a short period of time without immediately linking to past operations,” says Google Threat Intelligence Group (GTIG) stated in the analysis.
“Since Russia’s full-scale invasion of Ukraine, APT44 has used such tools, including malware such as cryptographic rats (DCRAT), Warzone, Radthief (“Rhadamanthys Stealer”), and host infrastructure for use. I’ve increased the number. Yalishhanda is a Russian-speaking actor who promotes in the Cyber Criminal underground community. ”
According to Microsoft, Sandworm subgroups will be operational from at least late 2021, taking advantage of various known security flaws to obtain initial access, followed by gathering qualifications, running commands, and lateral A series of post-exploitation actions aimed at supporting movements follows.
“The observed operations after the initial access are the campaign that will allow Seashell Blizzard to access global targets across sensitive sectors, including international governments, including energy, oil, gas, communications, shipping and weapons manufacturing. It shows you can get the ”, Tech Giant said.
“This subgroup is enabled by horizontally scalable features enhanced by public exploits that allow Seashell Blizzard to discover and compromise numerous Internet-oriented systems in a wide range of geographical regions and sectors. .”
Since early last year, subclusters have weaponized vulnerabilities in Connectwise Screenconnect (CVE-2024-1709) and Fortinet Forticlient EMS (CVE-2023-48788) to infiltrate UK and US targets It is said that.

The attacks carried out by subgroups include both opportunistic “spray and prayer” attacks and subsequent actions to maintain indiscriminate access and extend network access or obtain sensitive information. It includes both combinations of target intrusions designed to.
The broad compromise will provide Seashell Blizzard a way to achieve the Kremlin’s ever-evolving strategic goals, and believes that the hacking outfit will allow operations to be expanded horizontally across diverse sectors as new exploits are disclosed. It is being done.
Eight different known security vulnerabilities have been exploited by subgroups so far.
A successful scaffolding is carried over by threat actors who establish persistence through three different methods –
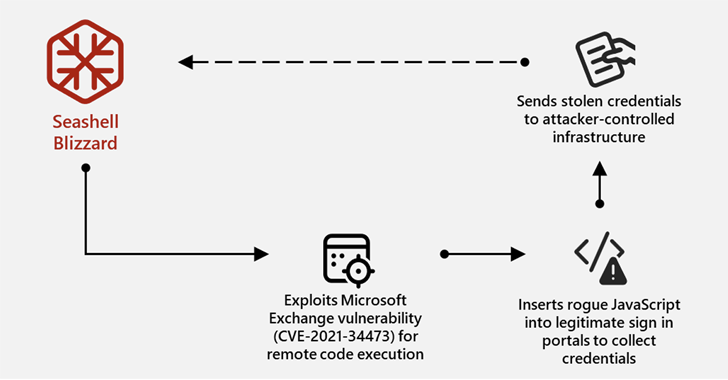
February 24, 2024 – Current: Deploying legal remote access software such as Atera Agent and Splashtop Remote Services. Utilities that allow compromised systems to be accessed through an anonymous network in late 2021 can be accessed through an anonymous network in late 2021. For example, Chisel, Plink, and rsoctun) – Late 2021-2024: Harves and removes credentials in real-time to threat actors and DNS in response to malicious changes to Outlook Web Access (OWA) sign-in pages. Inject JavaScript code that can be modified. For efforts to intercept credentials from the A-Record configuration critical authentication service
“This subgroup is characterized within the wider Seashell Blizzard organization by its close-global reach, representing the expansion of both the geographical targeting and the scope of its operations that Seashell Blizzard has implemented,” Microsoft said. .

“At the same time, Seashell Blizzard’s widespread and opportunistic access methods may provide a vast Russian opportunity for niche operations and activities that will remain valuable over the medium term.”
Development occurs as Dutch cybersecurity company EclectICIQ has linked Sandworm Group to another campaign that leverages pirated Microsoft Key Management Service (KMS) activators and fake Windows updates to provide backorders for newer versions. Two-stage payload from a remote server.
For each Mandiant, the Backorder is usually delivered within a Trojanized Installer file and hard coded to run the original setup executable. The ultimate goal of the campaign is to deliver crypto rats.

“The heavy reliance on cracked software, including Ukrainian government agencies, creates a major attack surface,” said security researcher Arda Büyükkaya. “Many users, including companies and important entities, are turning to pirated software from untrusted sources, and embedding malware into widely used programs, against enemies like SandWorm (APT44). It gives you the opportunity to do so.”
Further infrastructure analysis has resulted in Windows updates of previously undocumented RDP backdoor codenames. This revealed that using the TOR network for command and control, deploying OpenSSH and remote access via Remote Desktop Protocol (RDP) and remote access. At port 3389.
“By leveraging troilized software to infiltrate the ICS environment, the Sandworm (APT44) is a strategic one that destabilizes Ukraine’s critical infrastructure to support Russia’s geopolitical ambitions. We continue to demonstrate our goals,” Büyükkaya said.
Source link