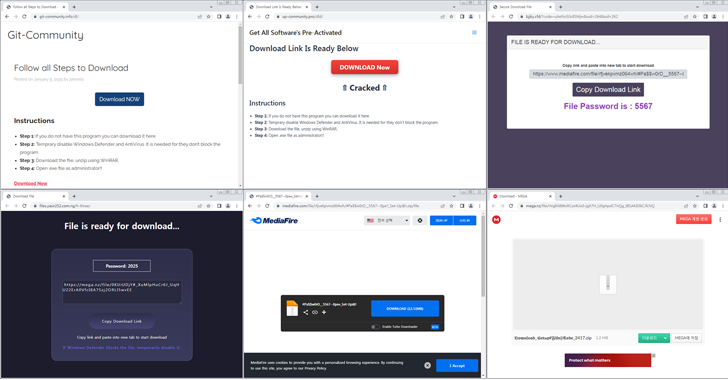
Cybersecurity researchers are warning of new campaigns that will utilize cracked versions of the software as lures for distributing information steelers such as Lumma and ACR Stealer.
The Ahnlab Security Intelligence Center (ASEC) said it has been observing a surge in ACR Stealer distribution since January 2025.
A notable aspect of steeler malware is the use of a technique called Dead Drop Resolver to extract real command and control (C2) servers. This includes relying on legitimate services such as Steam, Telegram’s Telegraph, Google Forms, and Google Slides.
“Threat actors enter the actual C2 domain with Base64 encoding to a specific page,” ASEC said. “The malware will visit this page, parse the string, get the actual C2 domain address and perform malicious behavior.”

Previously distributed via hijacking loader malware, ACR Stealer can harvest a wide range of information from compromised systems, including files, web browser data, and cryptocurrency wallet extensions.
The development occurs as ASEC revealed another campaign that uses files with the extension “MSC” that Microsoft Management Console (MMC) can run to provide Rhadamanthys Stealer malware.
“There are two types of MSC malware: one leverages a vulnerability in APDS.DLL (CVE-2024-43572), and the other uses the console taskpad to execute the command command. “We’ll do that,” the Korean company said.
“MSC file is impersonated as an MS Word Document.” When the “Open” button is clicked, it downloads and runs a PowerShell script from an external source. The downloaded PowerShell script contains the exe file (Rhadamanthys). ”
CVE-2024-43572, also known as Grimresource, was first recorded in June 2024 as being exploited as zero-day by a malicious actor by the Elastic Security Lab. The patch was applied by Microsoft in October 2024.
Malware campaigns have been observed to use chat support platforms such as Zendesk, spoofing customers, tricking unsuspecting support agents to download a steeler called Zhong Stealer.
A recent report published by Hudson Rock shows that over 30,000,000 computers have been infected with information stolen “in the past few years,” leading to the theft of corporate credentials and session cookies, and then Cybercriminals on underground forums Session cookies that can be sold to other actors for profit.
Buyers can use the access provided by these credentials as weapons to set the post-explosion action into their own actions, leading to serious risks. These developments help to highlight the role Stealer Malware plays as an initial access vector that provides a foothold in a sensitive corporate environment.
“For just $10 per log (computer), cybercriminals can purchase stolen data from employees working in the classified defense and military sectors,” Hudson Locke said. “Infostealer Intelligence isn’t just about detecting who’s infected. It’s about understanding a compromised qualification and a complete network of third-party risks.”

Over the past year, threat actors have stepped up their efforts to spread a wide range of malware families, including steelers and remote access trojans (rats). Run the Nefarious Powershell command.
One such payload was dropped is I2Plat. This anonymizes the final C2 server using an I2P anonymization network.
“Malware is a sophisticated threat consisting of multiple layers, each with a sophisticated mechanism built into it,” says Sekoia. “The use of anonymous networks complicates tracking, prevents the identification of threat magnitudes, and spreads wildly.”
Source link