Cyber threats are more refined, and traditional security approaches struggle to keep up. Organizations cannot rely on regular evaluations or static vulnerability lists. Instead, a dynamic approach is needed that provides real-time insight into how attackers move their environment.
This is where the attack graph is included. By mapping potential attack paths, it provides a more strategic way to identify and mitigate risks. In this article, we will explore the benefits, types, and real applications of attack graphs.
Understanding Attack Graphs
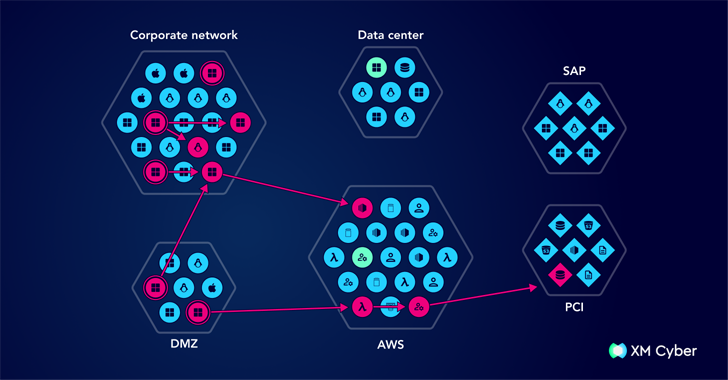
An attack graph is a visual representation of a potential attack path within a system or network. It maps how attackers move through various security weaknesses, such as misunderstandings, vulnerabilities, and qualification exposures, to reach critical assets. Attack graphs incorporate data from a variety of sources and are continuously updated as the environment changes, allowing you to model real-world attack scenarios.
Instead of focusing solely on individual vulnerabilities, attack graphs provide a larger image. This can be used together with various security gaps, including misunderstandings, qualification issues, and network exposures, to pose serious risks.
Unlike traditional security models that prioritize vulnerabilities based solely on severity scores, graphs attack exploitability and business impact. reason? Just because you have a highly vulnerable CVSS score doesn’t mean you’re a real threat to a particular environment. Attack graphs add important contexts and show whether vulnerabilities can be used in conjunction with other weaknesses to actually reach critical assets.
Attack graphs can also provide continuous visibility. This can quickly become obsolete, as opposed to one-off ratings such as the Red Team and the Penetration Test. By analyzing all possible paths an attacker can take, organizations can leverage attack graphs to identify and deal with “chokepoints.”
Types of attack graphs explained
All attack graphs are not equal. They are in many different forms, each with its strengths and limitations. Understanding these types can help security teams choose the right approach to identify and mitigate risks.
Security graph
Security graphs map relationships between different system elements, such as user permissions, network configuration, and vulnerabilities. These provide visualizations of how the different components connect. However, they do not show how attackers can exploit them.
Pros – Security graphs are relatively easy to implement and can provide valuable insight into your organization’s infrastructure. It can help security teams identify potential security gaps. Cons – Manual queries are required to analyze risk. This means that your security team needs to know what to look for in advance. This could have been a missed attack path, especially when multiple weaknesses are combined in unexpected ways.
Aggregated graphs
Aggregated graphs combine data from multiple security tools, such as vulnerability scanners, identity management systems, and cloud security solutions, into a unified model.
Pros – They leverage existing security tools to provide a more holistic view of risk across different environments. Cons-Integration can be challenging due to potential data inconsistencies and visibility gaps. The big picture may still be incomplete as these graphs rely on separate tools with their own limitations.
Holistic Attack Graph
An altitude, holistic attack graph takes away different directions. These are dedicated to modeling real attacker behavior, with a special focus on how threats evolve across systems. Map all possible attack paths and continuously update yourself as your environment changes. Unlike other graphs, they do not rely on manual queries or predefined assumptions. It also provides continuous surveillance, context of actual exploitation, and effective prioritization. This helps your security team focus on the most important risks first.

Practical Benefits of Attack Graphs
Attack graphs provide continuous visibility into attack paths. This will allow security teams to provide a dynamic, real-time view instead of outdated snapshots from regular evaluations. By mapping how attackers potentially navigate the environment, organizations can understand evolving threats more clearly.
It also improves prioritization and risk management by contextualizing vulnerabilities. Rather than blindly patching high CVSS defects, security teams can identify important choke points. This is an important weakness when fixed, which significantly reduces risk with multiple attack passes.
Another major advantage is cross-team communication. Attack graphs simplify complex security issues and crucially help CISOs overcome the challenge of explaining risks to executives and committees through clear visual representation.
Finally, the attached graph increases the efficiency of remediation efforts by allowing security teams to focus on protecting their business assets first. By prioritizing corrections based on both actual exploitability and business impact, organizations can effectively allocate security resources.
Use attack graphs for aggressive security
Attack graphs shift cybersecurity from a reactive stance to a proactive strategy. Instead of waiting for an attack to occur or relying on a quick assessment, security teams can use attack graphs to predict threats before they are exploited.
A key component of this shift from reactive to proactive security is the ability of attack graphs to integrate threat intelligence. Continuing incorporating data on new vulnerabilities, exploit techniques, and attacker behavior allows organizations to stay ahead of the threat rather than react after damage has occurred.
Continuous evaluation is also important in modern IT environments where change is norm. Attack graphs provide real-time updates. This helps security teams adapt as their network, identity and cloud environments change. Unlike static models, attack graphs provide continuous visibility into attack paths, allowing smarter, more informed decisions.
By leveraging attack graphs, organizations can move beyond traditional vulnerability management to focus on actual exploitation and business impact. This shift from reactive patching to strategic risk reduction makes security operations more efficient and effective. Ultimately, the attack graph will allow teams to fill important security gaps, strengthen their defenses and stay ahead of the enemy.
Note: This article is skillfully written by SVP of Menachem Shafran, Vice President of Global Sales Engineering at XM Cyber, and Vice President of Global Sales Engineering.
Source link