According to new Kaspersky surveys, Russian organizations have become targets for phishing campaigns that distribute malware called Purerat.
“The Russian business-oriented campaign began in March 2023, but in the first third of 2025, the number of attacks was quadrupled in comparison to the same period in 2024,” the cybersecurity vendor said.
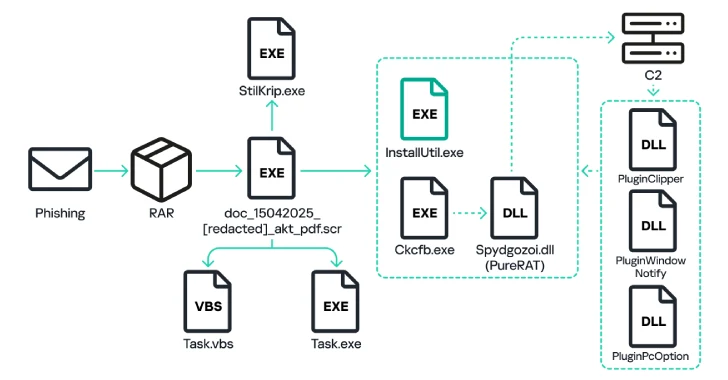
Attack chains not attributable to a particular threat actor will start with a phishing email containing attachments to RAR files or links to archives that masquerade Microsoft Word or PDF documents (“doc_054_[redacted].pdf.rar “).
What resides in the archive file is an executable that, upon launch, copies itself to the “%appData%” position of the compromised Windows machine under the name “task.exe” and creates a visual basic script called “task.vbs” in the startup vbs folder.

The executable file unzips another executable file “ckcfb.exe”, runs the system utility “installutil.exe” and injects it into the decrypted module. For “CKCFB.EXE”, the part of which extracts and decrypts the DLL file “Spydgozoi.dll”, which incorporates the main payload of the Purerat malware.
Purerat establishes an SSL connection on the Command and Control (C2) server and sends system information including system information, computer name, and details of how long it has passed since the system started up. In response, the C2 server sends an auxiliary module to perform various malicious actions –
PluginPcoption allows you to run self-exclusion commands, restart the executable, and shut down or restart the plug of your computer, like computer plugin windowdown. I used something that was controlled by the attacker and copied it to the system clipboard
“The Trojan includes modules for downloading and running any file that provides full access to file systems, registry, processes, cameras and microphones, implementing keylogger functionality and allowing attackers to secretly control their computers using the principles of remote desktop,” says Kaspersky.

The original executable that launches “CKCFB.exe” simultaneously also extracts a second binary called “Stilkrip.exe”. It has been active since 2022.

“stillkrip.exe” is designed to download “bghwwhmlr.wav”. This follows the attack sequence mentioned above, running “installutil.exe” and eventually launching “ttcxxewxtly.exe”.
PureLogs is a ready-made information steel person who can collect data from web browsers, email clients, VPN services, messaging apps, wallet browser extensions, password managers, cryptocurrency wallet apps, and programs such as Filezilla and WinSCP.
“Purerat Backdoor and Purelogs Stealer have a wide range of features that allow attackers to have unlimited access to data from infected systems and sensitive organizations,” Kaspersky said. “The main vector of attacks on businesses is emails with malicious attachments and links that remain.”
Source link