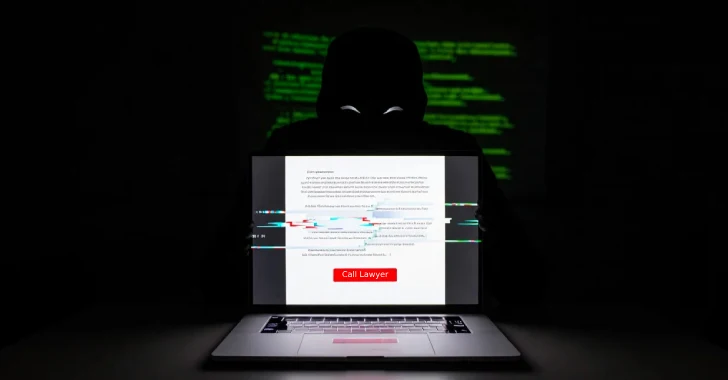
As cybercriminal groups try to bolster their activities and fill in the void left by their rivals, the threat actors behind the Qilin Ransomware-as-a-Service (RAAS) scheme are now offering affiliate legal counsels to pressure victims to pay.
The new feature takes the form of the “Cole Lawyer” feature of the affiliate panel, according to Israeli cybersecurity company Cybereason.
The development represents the new revival of e-crime groups as once popular ransomware groups such as Lockbit, Black Cat, Ransomhub, Everest and Blacklock. The group has also been tracked as Gold Feathers and Water Garra and has been active since October 2022.
Data compiled from the dark web leak site run by the Ransomware Group shows that Qilin had 72 casualties in April 2025. In May, it is estimated to be behind 55 attacks, and is placed behind Safepay (72) and Luna Moth (67). It is also the third most active group after CL0P and Akira, claiming a total of 304 casualties.
“Qilin stands above others in a rapidly rising market with its mature ecosystem, extensive client support options, and robust solutions to ensure significant targeted, high impact ransomware attacks,” said the group’s analysis this week, which secures a pretty shocking ransomware attack.

There is evidence suggesting that an affiliate working at Ransomhub has moved to Qilin and has contributed to the spikes of Qilin ransomware activity in recent months.
“Due to its growing presence across the forums and ransomware activity trackers, Qilin operates a technically mature infrastructure: an affiliate panel that provides rust and C-built payloads, a loader with advanced evasion capabilities, running safe mode, network spreading, log cleanup and automated negotiation tools.
“Beyond the malware itself, Qilin offers a complete set of spam services, PB scale data storage, legal guidance and operational capabilities. It positions itself not only as a ransomware group, but as a full-service cybercrime platform.”
The decline and termination of other groups are complemented by new updates to the Qilin affiliate panel, which incorporates new legal aid capabilities, a team of internal journalists, and the ability to carry out distributed denial (DDOS) attacks. Another notable addition is a tool for spamming corporate email addresses and phone numbers.
This extension shows the attempt on the part of threat actors to sell themselves as a full-scale cybercrime service beyond ransomware.
“If you need a legal consultation regarding your target, simply click the “Call Attorney” button within the target interface and our legal team will contact you and provide eligible legal support.”
“The mere appearance of lawyers in chat can put indirect pressure on the company and increase the ransom because companies want to avoid legal proceedings.”
Intrinsec occurs because at least one affiliate of Rhysida has evaluated that they have begun using an open source utility named Eye Pyramid C2 as a post-explosion tool to maintain access to compromised endpoints and provide additional payloads.
It is noteworthy that the Pyramid C2 of the Eye points to the same Python-based backdoor deployed by threat actors linked to the crew of the Ransom Hub in the fourth quarter of 2024.
It also follows a fresh analysis of leaked black Busta chat logs that shed light on threat actors through the online alias “Tinker.” Their real-world identity is currently unknown.
According to Intel 471, Tinker is said to be one of the trusted aides to the group’s leader Tramp, and has run a call center that includes the now-deprecated Conti Group, and after gaining previous experience in the call center as a negotiator for Blacksuit (AKA Royal), he joined the criminal enterprise as a “creative director.”
“Actor Tinker played a key role in ensuring early access to the organization,” the cybersecurity company said. “The leaked conversations reveal that Tinker will analyze financial data and assess the victim’s situation before direct negotiations.”
In addition to conducting open source investigations to obtain contact information for senior company staff to force them through telephone or message, threat actors were tasked with writing phishing emails designed to violate the organization.

In particular, Tinker also came up with a Microsoft team-based phishing scenario. The attacker pretends to be an IT employee, warning the victim that he is on the receiver of a spam attack, and encourages employees to install remote desktop tools like Anydesk and grant access to protect the system.
“After the RMM software is installed, the caller will contact one of the Black Basta intrusion testers and move to ensure permanent access to the system and domain,” Intel 471 said.
The leaked message also reveals that Tinker received more than $105,000 in cryptocurrency for his efforts from December 18, 2023 to June 16, 2024.

The findings coincided with the suspicion of his role as an early access broker (IAB) and the extradition of an unknown 33-year-old foreign member of the Ryuk Ransomware Group to the US to promote access to corporate networks. The suspect was arrested from Kiev in early April this year at the request of US law enforcement.
Members were “engaged in exploring the vulnerability of the victims’ corporate network,” the Ukrainian National Police said in a statement. “The data obtained by the hackers were used by his accomplices to plan and carry out cyber attacks.”
Authorities said they could track suspects targeting members of the Lockergoga, Megacortex and Dharma Ransomware family following a forensic analysis of equipment seized in previous RAIDs in November 2023.
Elsewhere, Thai police officers arrested several Chinese nationals and other Southeast Asian suspects after raiding a hotel in Pattaya, which was used as a gambling den and as an office for ransomware businesses.

The ransomware scheme is said to be run by six Chinese citizens, and he sent a malicious link to businesses to infect ransomware. Local media reports say they were cybercrime gang employees paid to distribute booby-confined links to Chinese companies.
This week, Thailand’s Central Investigation Bureau (CIB) announced the arrest of more than 12 foreigners as part of Operation Firestorm on suspicion of carrying out online investment scams to fraud several Australian victims and deceive the scam by investing money with the promise of high returns on long-term bonds.
Source link