Cybersecurity researchers have disclosed three security flaws in the Rack Ruby Web Server interface: This allows an attacker to gain unauthorized access to the file, inject malicious data, and allow logs to be tampered with certain conditions.
Vulnerabilities flagged by cybersecurity vendor opswat are listed below –
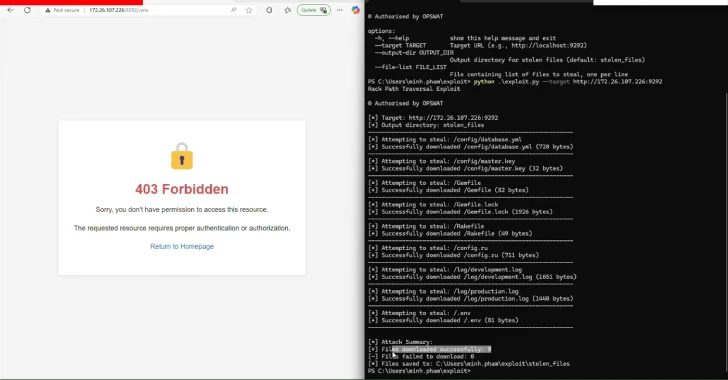
CVE-2025-27610 (CVSS score: 7.5) – Path traversal vulnerability that can be used to access all files under the specified root: directory, assuming that an attacker can determine the path to those files. Vulnerability that can be used to manipulate log entries and distort log files CVE-2025-25184 (CVSS score: 5.7) – Inappropriate neutralization (CRLF) sequences and inappropriate output of carriage return line feed (CRLF) sequences are neutralized, allowing log manipulation vulnerabilities and malicious data to manipulate log manipulation vulnerabilities.
The successful exploitation of flaws allows attackers to obscure traces of attacks, read any file and inject malicious code.

“Of these vulnerabilities, CVE-2025-27610 is particularly serious. This could lead to data breaches, as it allows uncertified attackers to obtain sensitive information such as configuration files, credentials, and sensitive data.
The drawback comes from the fact that Rack::Static, the middleware used to serve static content such as JavaScript, StyleSheet, and images, does not sanitize paths that users will suppress before serving files, leading to scenarios where attackers can provide specially created paths for accessing files other than static file directories.
“Specifically, if no root parameters are explicitly defined, the rack defaults this value to the current working directory by assigning a value of dir.pwd and implicitly specifies it as the web root directory of the rack application,” Opswat said.
As a result: if the route option is undefined or is misconfigured for the following options, an uncertified attacker can use CVE-2025-27610 through the PATH traversal technique to access sensitive files outside the intended web directory.
We recommend updating to the latest version to mitigate the risk poses from defects. If immediate patching is not an option, we recommend removing the use of rack::static or pointing to a directory path that contains only the files that should be exposed.
Serious flaws in Infodraw Media Relay Service
This disclosure is due to a serious security flaw that was unearthed in the Infodraw Media Relay Service (MRS), which allows the reading or deletion of any file via a past traversal vulnerability in the username parameter on the system’s login page (CVE-2025-43928, CVSS score: 9.8).
InfodRaw is an Israeli manufacturer of mobile video surveillance solutions used to transmit audio, video and GPS data over telecommunications networks. According to the company’s website, the device is used in many countries by law enforcement, private investigations, fleet management and public transport.

“A trivial past traversal vulnerability allows files to be read from systems aimed at unrecognized attackers,” security researcher Tim Phillip Shepherds said in a statement shared with Hacker News. “In addition, there is a “arbitrary file deletion vulnerability” that allows an attacker to delete files from the system. ”
The Flaw, which allows you to log in with a username such as “..//../..//” affects both the Windows and Linux versions of MRS. That said, the defects continue to remain below. The vulnerable systems in Belgium and Luxembourg have been taken offline following responsible disclosure.
“Affected organizations are primarily encouraged to take their applications offline immediately (although despite early warnings, manufacturer patches are not available, so it is believed that the vulnerability could be exploited by vulnerable actors in the near future),” Philip Shepherds said.
“If this is not possible, the system should further protect it with additional metering (such as using a VPN or unlocking a certain IP).”
Source link