The new malware campaign uses popular Clickfix social engineering tactics launched via fake Captcha verification pages to distribute a new Rust-based information steeler called Eddiestealer.
“This campaign leverages the deceit captcha validation page, in which users run malicious PowerShell scripts that ultimately deploy Infostealer to harvest sensitive data such as credentials, browser information, cryptocurrency wallet details and more.”
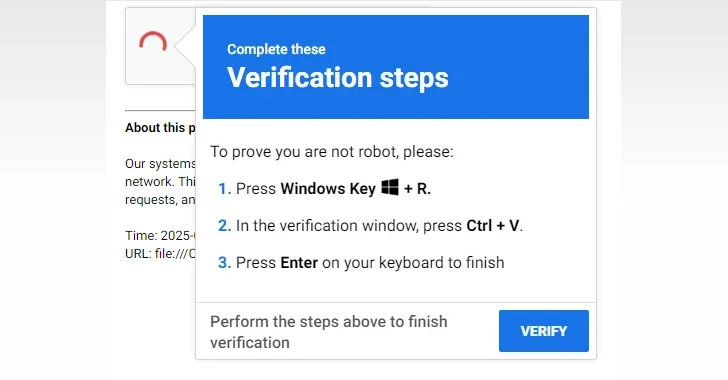
The attack chain starts with a threat actor who compromises a legitimate website with a malicious JavaScript payload that provides fake capture check pages. [a] Robot “A common tactic called Clickfix by following a three-stage process.
This involves opening a Windows Run dialog prompt to potential victims and then opening the already copied command “Validation window” (i.e.[実行]Paste it into the dialog box and press Enter. This will run the obfuscated PowerShell command and retrieve the next stage payload from the external server (“LLLL[.]fit”).
The JavaScript payload (“gverify.js”) is then saved in the victim’s download folder and executed using cscript in a hidden window. The main goal of the interim script is to retrieve the eddiestealer binary from the same remote server and save it in the download folder with pseudo-random 12 character file names.
Written in Rust, Eddiestealer is a commodity steeler malware that can collect system metadata, receive tasks from a command and control (C2) server, and receive perspective data of interest from infected hosts. Exfiltration targets include cryptocurrency wallets, web browsers, password managers, FTP clients, and messaging apps.
“These targets may be changed because they can be configured by the C2 operator,” explained Elastic. “Eddiestealer uses standard kernel32.dll functions such as createfilew, getfilesizeex, readfile, and closehandle to read the target file.”

The collected host information is encrypted in a separate HTTP POST request after each task is completed and sent to the C2 server.
In addition to incorporating string encryption, the malware employs a custom WinAPI lookup mechanism to resolve API calls, creating Mutexes to ensure that only one version is running at any time. It also determines whether it is running in a sandboxed environment with built-in checks and, if so, removes it from disk.
“Based on similar self-exclusion techniques observed in Latrodectus, Eddiestealer can be removed via renaming NTFS alternative data streams to bypass file locks,” Elastic said.
Another notable feature built into Steeler is that it allows you to bypass chrome app-bound encryption to access unencrypted sensitive data such as cookies. This is achieved by including a Rust implementation of Chromekatz. Chromekatz is an open source tool that allows you to dump cookies and credentials from memory in a Chromium-based browser.
The Rust version of Chromekatz also includes changes to handle scenarios where the targeted Chromium browser is not running. In such cases, a new browser instance is generated using the command line argument “-window-position = -3000, -3000 https://google.com”.

When you open the browser, the purpose is to be able to read the memory associated with a child process of a Chrome network service identified by “-utility-sub-type = network.mojom.networkservice”.
Elastic said he also identified an updated version of the malware with the ability to harvest the running process, GPU information, CPU core count, CPU name, and CPU vendor. Additionally, the new variant fine-tunes the C2 communication pattern by preemptively sending host information to the server before receiving the task configuration.
That’s not all. The encryption key used for client-to-client communication is hardcoded into binary rather than dynamically retrieved from the server. Additionally, it is known that steelers launch new Chrome processes using -remote-debugging-port=flag to enable the DevTools protocol on the local websocket interface to interact with the browser without the need for user interaction.
“This adoption of rust in malware development reflects the growth trends of threat actors seeking to leverage modern language capabilities to improve stealth, stability and resilience over traditional analytical workflows and threat detection engines,” the company said.
This disclosure comes when C/Side reveals details about a ClickFix campaign targeting multiple platforms, including Apple MacOS, Android, and iOS, using techniques such as browser-based redirection, fake UI prompts, and drive-by download techniques.
The attack chain starts with obfuscated JavaScript hosted on a website. This leads to a download of steeler malware that, when visited from MacOS, initiates a series of redirects to pages that guide the victim to launch the terminal and run the shell script, flagging Virustotal as Atomic Macauzear (AMOS).
However, the same campaign is set up to launch a drive-by download scheme when accessing a web page from an Android, iOS or Windows device, leading to the deployment of another Trojan malware.

According to Nextron and Kandji, disclosures coincide with the emergence of new steeler families such as Katz Stealer and AppleProcesshub Stealer and AppleProcesshub Stealer respectively, allowing a wide range of information to be harvested from infected hosts.
Katz Stealer, like Eddiestealer, is designed to avoid app-bound encryption in Chrome, but is designed differently by using DLL injection to obtain an encryption key without administrator privileges and using it to decrypt encrypted cookies and passwords from Chromium-based browsers.

“Attackers hide malicious JavaScript in GZIP files, which triggers the download of PowerShell scripts when opened,” says Nextron. “This script gets a .NET-based loader payload, which injects the steeler into a legitimate process. When active, it removes stolen data to the command and control server.”
Meanwhile, AppleProcesshub Stealer is designed to remove user files such as Bash History, ZSH History, GitHub configuration, SSH information, iCloud keychain, and more.
The attack sequence that distributes the malware involves the use of MACH-O binary to download the second stage Bash Stealer script from the server “AppleProcesshub”[.]com” will return the result to the C2 server. Details about the malware were first shared on May 15, 2025 by Malwarehunterteam and last week by Macpaw’s Moonlock Lab.
“This is an example of MACH-O written in Objective-C, which communicates with commands and control servers to run scripts,” said Christopher Lopez, a researcher at Kandji.
Source link