Maritime and logistics companies in South and Southeast Asia, the Middle East and Africa are targeted by a highly persistent threat (APT) group called sidewarders.
The attacks observed by Kaspersky in 2024 have spread to Bangladesh, Cambodia, Djibouti, Egypt, the United Arab Emirates and Vietnam. Other targets of interest include nuclear power plants and nuclear infrastructure in South Asia and Africa, telecommunications, consulting, service companies, real estate institutions, hotels, and more.

Sidewinder is what appears to be a broad expansion of the victims’ footprint, and is also targeting diplomatic groups in Afghanistan, Algeria, Bulgaria, China, India, the Maldives, Rwanda, Saudi Arabia, Turkey and Uganda. Indian targeting is important as the threat actors were previously suspected of Indian origin.
“It is worth noting that Sidewinder is always working to improve its toolset, expand the persistence of compromised networks ahead of security software detection, and hide its presence in infected systems,” explains Giampaolo Dedola and Vasily Berdnikov as “a very advanced and dangerous neighbor.”

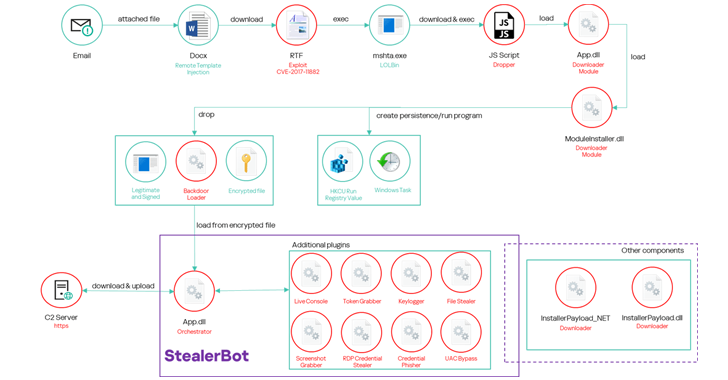
Sidewinder was previously subject to extensive analysis by Russian cybersecurity companies in October 2024, documenting the use of a toolkit threat actor in a modular explosion called Stealerbot, which captured a wide range of confidential information from compromised hosts. Targeting the maritime sector of the hacking group was also highlighted by BlackBerry in July 2024.
The latest attack chain is consistent with previously reported, serving as a conduit for providing booby-confined documents that exploit known security vulnerabilities in Microsoft’s Office Equation Editor (CVE-2017-11882), and activating multi-stage sequences derived from ranter ranter to activate multi-stage sequences.

Kaspersky said some of the lure documents were related to nuclear power plants and nuclear energy agencies, and others included content referring to maritime infrastructure and various port authorities.
“They are constantly monitoring the detection of toolsets through security solutions,” Kaspersky said. “When a tool is identified, it responds by generating a new, modified version of malware, often within five hours.”
“If behavior detection occurs, SideWinder attempts to change the technique used to maintain persistence and load components. Additionally, it changes the name and path of the malicious file.”
Source link