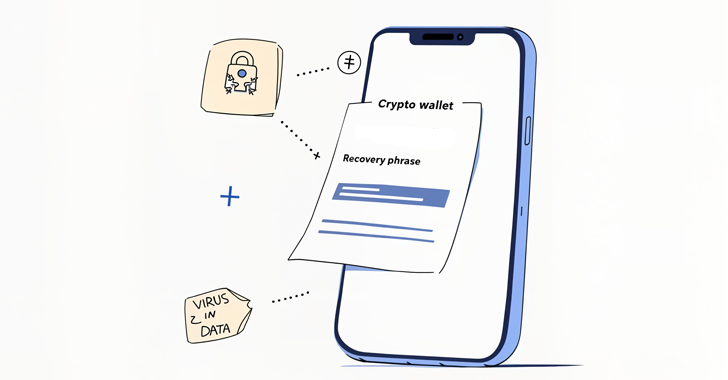
A new malware campaign called Sparkcat has leveraged fake apps on both Apple and Google app stores to steal mnemonic phrases from victims related to cryptocurrency wallets.
The attack leverages an optical character recognition (OCR) model to remove selected images containing wallet recovery phrases from the photo library to a command and control (C2) server, and Kaspersky researchers Dmitry Kalinin and Sergey Puzan mentioned in the technical report.
This moniker is a reference to an embedded software development kit (SDK) that employs a Java component called Spark, which poses as an analysis module. Currently, it is unclear whether the infection was the result of a supply chain attack or whether it was intentionally introduced by the developer.
This is not the first time that Android malware with OCR functionality has been detected in the wild, but it is one of the first instances where such a steeler has been discovered in Apple’s App Store. It is said that the infected app on Google Play has been downloaded more than 242,000 times.

The campaign has been rated active since March 2024, and the app is distributed through both the official and unofficial app stores. The application is equipped with artificial intelligence (AI), food delivery, and Web3 apps, but some of them seem to offer legitimate features.
“The Android malware module decrypts and launches an OCR plugin built with Google’s ML kit library and uses it to recognize the text in images in the gallery,” says Kaspersky. “Images matching keywords received from C2 have been sent to the server.”
Similarly, the iOS version of SparkCat relies on Google’s ML kit library, where OCR steals images containing mnemonic phrases. A notable aspect of malware is the use of C2 rust-based communication mechanisms, which are rarely observed in mobile apps.
Further analysis of the keywords used and the regions in which these apps were made available indicate that the campaign is primarily targeted at European and Asian users. Malicious activities are recognized as the work of threat actors who are proficient in Chinese.
“What makes this Trojan horse particularly dangerous is its lack of indication that malicious implants are hidden within the app,” the researchers said. “The authority it requests may appear to be necessary for its core functionality or seem harmless.”
This disclosure allows Zimperium Zlabs to distribute malicious APK files via WhatsApp under the guise of bank and government applications, allowing apps to harvest sensitive obstacles and financial information, and to enable them to harvest the app’s sensitive obstacles and financial information. This is because we detailed another mobile malware campaign targeting owners.
Cybersecurity companies have identified over 1,000 fake apps linked to the campaign, and attackers have roughly 1,000 hardcoding phone numbers as exfiltration points for SMS messages and one-time passwords (OTP). He said he is using it.
Unlike traditional bank trojans that rely solely on one-time password (OTP) theft command and control (C&C) servers, this malware campaign leverages live phone numbers to redirect SMS messages and to redirect them. We’ll leave trackable digital trails for enforcement agencies, tracking the threat actors behind this campaign,” said security researcher Aazim Yaswant.
The attack campaign, named Fatboypanel, is said to have accumulated 2.5 GB of sensitive data so far. All of these are hosted on FireBase endpoints that can be accessed by people who can use authentication.
This includes SMS messages from Indian banks, bank details, credit and debit card information, and government-issued identification details to which around 50,000 users belong. Madhya Pradesh.

Even if these incidents have been uploaded to the official app storefront, properly reviewing code apps, including scrutinizing reviews and checking developer reliability before downloading them. We take note of the importance of doing so.
According to security researcher Patrick Wardle, the development follows the emergence of 24 new malware families targeting Apple Macos Systems from 21 in 2024 to 2024.

This coincides with a surge in information theft attacks such as Poseidon, Atomic and Cthulhu targeting users of desktop operating systems.
“InfoSealers that utilize Macau often have a native Applescript framework,” Palo Alto Network Unit 42 researchers Tom Factorman, Chenellich and Tom Sharon said in a report released this week. .
“This framework provides extensive OS access and simplifies execution with natural language syntax. Threat actors use this framework because these prompts can look like legitimate system prompts. and deceive the victims through social engineering.”
Source link