A new Android Malware (MAAS) platform named Supercard X promotes near-field communication (NFC) relay attacks, allowing cybercriminals to carry out fraudulent cashouts.
The Active Campaign aims to infringe payment card data on customers from Italian banking institutions and card issuers, fraud prevention company Cleef said in an analysis. There is evidence to suggest that the service is being promoted on telegram channels.
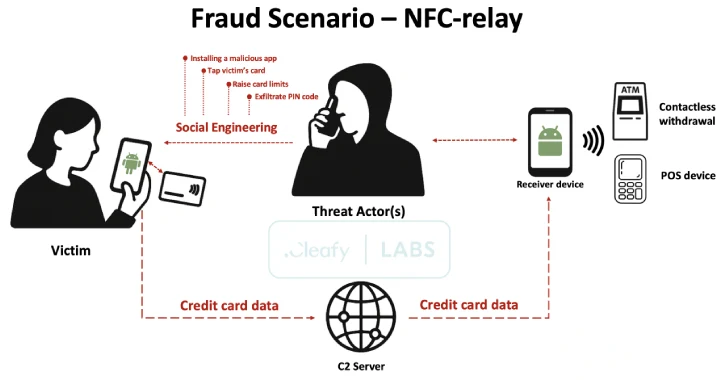
Supercard X employs a multi-stage approach that combines social engineering (smithing and via telephone), malicious application installation, and NFC data interception for highly effective fraud.

The new Android malware, a work by Chinese-speaking threat actors, has been observed to be propagated through three different fake apps, which will lead victims to install them via social engineering techniques such as deceit SMS and WhatsApp messages –
verifica carta (io.dxpay.remotenfc.supercard11) Supercard X (io.dxpay.remotenfc.supercard) Kingcard nfc (io.dxpay.remotenfc.supercard)
Messages can cause false sense of urgency by impersonating a bank security alert and urging recipients to call a specific number to challenge the transaction.
The infection chain then moves to what is called telephone-oriented attack delivery (TOAD). There, threat actors manipulate the victim and install the app in pose as security software through direct telephone conversations. Threat actors have been found to employ compelling tactics to collect victim pins and instruct them to remove existing card restrictions.

At the core of the operation is NFC relay technology that has not been previously documented, where threat actors unauthorizedly allow POS (POS) payments and automatic teller machine (ATM) withdrawals by intercepting and relaying NFC communications from infected devices.
To do this, the attacker will encourage the victim to bring their debit or credit card closer to the mobile device. This allows Super Card X malware to secretly capture the details of the card that was sent to and communicate it to an external server. Harvested card information is used by threat actor-controlled devices to carry out unauthorized transactions.
The application distributed to the victim to capture NFC card data is called a reader. A similar app known as Tapper is installed on threat actor devices to receive card information. Communication between readers and Tupper is performed using Command and Control (C2) using HTTP, which requires cybercriminals to be logged in.
As a result, threat actors are expected to create accounts within the Super Card X platform before distributing malicious apps. The victim is then instructed to enter the login credentials provided during the call.
This step can act as a critical COG for the overall attack, as it establishes a link between the victim’s infectious device and the threat actor’s Tapper instance, and then relay card data for subsequent cash-outs. The Tapper app is designed to emulate the victim’s card using stolen data, which tricks POS devices and ATMs into identifying them as legitimate cards.

The “Reader” malware artifact identified by Cleafy makes subtle differences in the login screen and is a custom build generated by affiliate actors, indicating that you can adjust your campaigns according to your needs. Additionally, SuperCard X uses mutual TLS (MTL) to ensure communication with the C2 infrastructure.
That threat actor can deceive unsuspecting users and deceive them from changing important settings on the phone. This is not noticed by Google. It is said to be working on a new Android feature that effectively blocks the installation of apps from unknown sources and gives permission to accessibility services.
Currently, there is no evidence that Supercard X is being distributed through the Google Play Store, but we recommend that users scrutinize the app’s description, permissions and reviews before downloading. We also recommend that you enable Google Play Protective to protect your device from new threats.
“This new campaign will go beyond the traditional goals of banking institutions and introduce important financial risks that directly affect payment providers and credit card issuers,” the researchers said.
“The innovative combination of malware and NFC relays allows attackers to perform fraudulent cash-outs on debit and credit cards. This method has shown high effectiveness, especially when targeting contactless ATM withdrawals.”
Source link