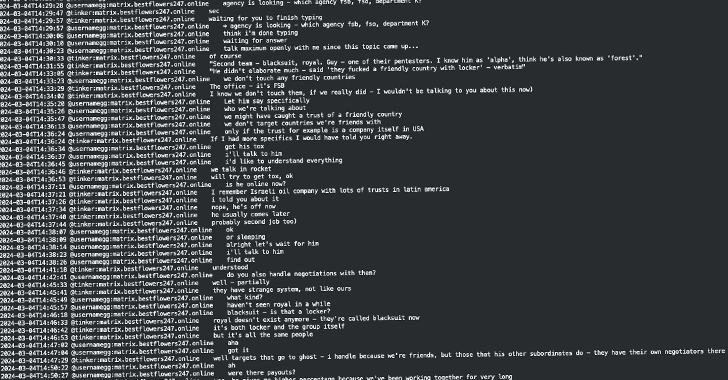
A trobe in the internal chat logs that was recently leaked among members of the Black Bus Staransomware operation revealed possible ties between electronic crime gangs and Russian authorities.
The leak containing over 200,000 messages from September 2023 to September 2024 was published last month by telegram user @exploitWhispers.
According to an analysis of the message by cybersecurity firm Trellix, Black Busta leader Olegnefedov (aka GG or AA) may have received assistance from Russian officials after being arrested in Yerevan, Armenia in June 2024, and can escape three days later.

In the message, GG claimed that it had passed through the “green corridor” and contacted senior officials to facilitate extraction.
“This knowledge from Chat Leaks makes it difficult for the Black Basta Gang to abandon the operating methods completely and start a new Raas from scratch without mentioning previous activities,” said Trellix researchers Jambul Tologonov and John Fokker.
Other notable findings include
The group may have two offices in Moscow, but the group may be using Openai chatgpt to collect victim data for rhysida and cactus aa cactus aa cactus of pikabot aa cactus of pikabot aa cactus of rhysida and cact bay aa cactus acactus acactus acactus acactus oper lansomware operations to create fraudulent formal letters in English, paraphrase text, rewrite C# based malware in Python, debug code, and collect victim data. (n3auxaxl) And it took a year to develop a malware loader after Qakbot’s destruction, and the group rented Darkgate from Rastafareye and used Lumma Stealer to steal credentials and additional malware. Ransomware derived from Conti’s source code leads to the release of prototypes written in C, indicating the possibility of rebranding
This occurs because Eclecticiq’s work on a brute-sturing framework designed to perform automated internet scans and certification fillings for edge network devices, including firewalls and VPN solutions that are widely used in corporate networks, reveals Black-sturing frameworks with brute-sturing frameworks known as brutes.

Cybercrime crews have been using PHP-based platforms since 2023 to carry out large-scale qualification and brute-force attacks on target devices, with evidence suggesting that threat actors can gain visibility into victim networks.
“Bruted frameworks allow Blackbusta affiliates to automate and expand these attacks, expand the victim pool, accelerate monetization and accelerate ransomware operation,” said security researcher Arda Büyükkaya.
“Internal communications is investing heavily in Black Basta’s brutally in a framework that allows for rapid internet scans of edge network appliances and large-scale credentials to target weak passwords.”
Source link