The Türkiye-related threat actor exploited the zero-day security flaw on an Indian enterprise communications platform called Output Messenger as part of its cyberspy attack campaign since April 2024.
“These exploits have resulted in a collection of relevant user data from targets in Iraq,” the Microsoft Threat Intelligence team said. “The targets of the attack are associated with Kurdish forces operating in Iraq and are consistent with previously observed marble dust targeting priorities.”
This activity is attributed to a threat group that tracks it as marble dust (formerly silicon), also known as Space Wolf, Horse, Teal Kruma, and UNC1326. The hacking crew is believed to have been active since at least 2017, but two years later, there has been no record of Cisco Talos recording attacks targeting public and private businesses in the Middle East and North Africa.
Earlier last year, it was also identified as targeting Dutch telecommunications, media, internet service providers (ISPs), information technology (IT) service providers, and Kurdish websites.

Microsoft has evaluated with moderate confidence that threat actors will do some sort of reconnaissance in advance to determine if the target is an output messenger user, leverage zero-day to distribute malicious payloads and remove data from the target.
The vulnerability in question is CVE-2025-27920. This is a directory traversal vulnerability affecting version 2.0.62 that allows remote attackers to access or execute arbitrary files. This issue was addressed by developer Srimax in late December 2024 with version 2.0.63. However, the company has not mentioned any defects exploited in the wild in its recommendations.
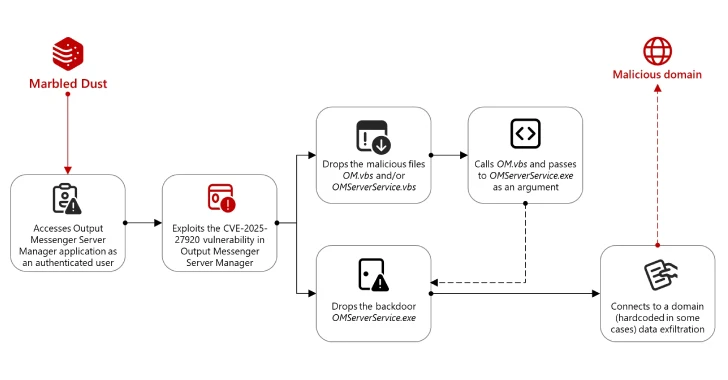
The attack chain begins with the threat actor being able to access the output Messenger Server Manager application as an authenticated user. Marble dust is believed to use techniques such as DNS hijacking and type squat domains to intercept the credentials required for authentication.
The access is then abused, collecting the user’s output messenger credentials and exploiting CVE-2025-27920 to drop payloads such as “OM.VBS” and “OmServerservice.vbs” in the server startup folder and into the “User/Published/Video” directory such as “OmServerservice.exe”.
In the next phase, the threat actor uses “omserverservice.vbs” to invoke “om.vbs” and “omserverservice.exe”.[.]com “) For data removal.
“On the client side, the installer extracts and runs both the legitimate files outputmessenger.exe.exe and omclientservice.exe.exe.
“This backdoor will first perform a connection check via a GET request to C2 domain API.WORDINFOS[.]com. If successful, a second GET request is sent to the same C2 containing the hostname information, uniquely identifying the victim. The response from C2 is then run directly using the command “CMD/C” which tells the Windows command prompt to run a specific command and then exit.

In one case, a victim device was included with output messenger client software. This was connected to an IP address previously identified as being used in marble dust for data stripping.
Tech Giant also noted that it discovered a second flaw that reflected the vulnerability of cross-site scripting (XSS) in the same version (CVE-2025-27921), but found no evidence of weaponization in actual attacks.
“This new attack shows a significant change in marble dust capabilities while maintaining consistency in the overall approach,” Microsoft said. “The successful use of zero-day exploits suggests an increase in technical refinement, potentially suggesting that marble dust targeting priorities have escalated or operational targets have become more urgent.”
Source link