The threat hunter has discovered a new threat actor named UAT-5918, which has been attacking Taiwan’s key infrastructure entities since at least 2023.
“UAT-5918 is a threat actor believed to be motivated by establishing long-term access for information theft and will use webshells and open source touring to carry out post-compromise activities to establish sustainability in the victim’s environment for information theft and qualification harvest.”

In addition to critical infrastructure, the verticals of other targets include information technology, communications, academia and healthcare.
UAT-5918 is said to share a tactical overlap with several Chinese hacking crews tracked as Bolt-time typhoons, Flax studs, Tropical Troopers, Earthestries and Dalbit, as rated as Dalbit.

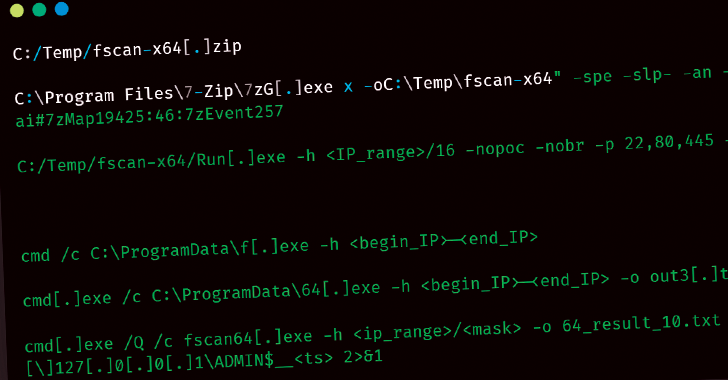
The attack chain organized by the group involves gaining initial access by leveraging the flaws of N-Day security on less than Internet exposed web and application servers. Using scaffolds, several open source tools are dropped to carry out network reconnaissance, system information gathering, and lateral movements.
After the UAT-5918 explosion, the product involves the use of fast reverse proxy (FRP) and Neo-Regeorge, and sets up a reverse proxy tunnel to access compromised endpoints via attacker-controlled remote hosts.

Threat actors are leveraging tools such as browser-based extractors called Mimikatz, Lazagne, and Browserdatalite to harvest credentials to drill deeper holes into the target environment via RDP, WMIC, or impact. Chopper Web Shell, Cloud A, and Sparrow Door are also used. The latter two were previously used by another threat group called Earth Estries.
In particular, BrowserDatalite is designed to steal and steal history, browsing history from your web browser. Threat actors are also engaged in systematic data theft by enumerating local and shared drives to find data of interest.
“The activities we monitored suggest that post-company activities are done manually with the main goal of information theft,” the researchers said. “It obviously includes deploying a web shell across discovered subdomains and servers that are accessible to the Internet, opening multiple entry points to victim organizations.”
Source link