Cybersecurity researchers have revealed that threat actors, known as the codename Visicotrap, have compromised nearly 5,300 unique network edge devices in 84 countries, turning them into honeypot-like networks.
Threat actors have been observed using critical security flaws affecting Cisco Small Business RV016, RV042, RV042G, RV082, RV320, and RV325 routers (CVE-2023-20118). The majority of the infections are in Macau, with 850 infringing devices.
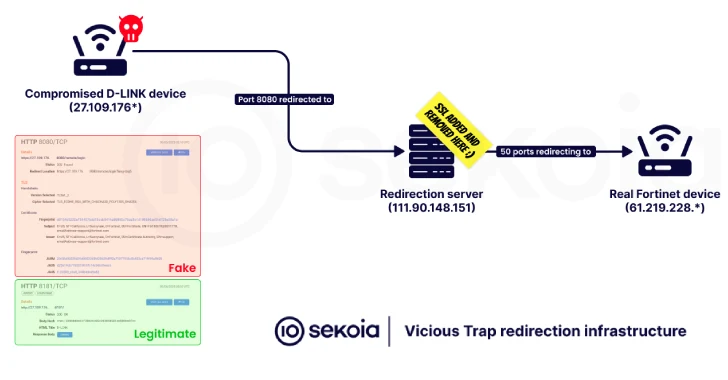
“The infection chain involves running a shell script called Netghost, which allows you to intercept network flows by redirecting incoming traffic from a specific port on a compromised router to a honeypot-like infrastructure under the control of an attacker.”

It is noteworthy that the exploitation of CVE-2023-20118 was attributed to Polaredo, previously known as another botnet by French cybersecurity firms.
Although there is no evidence that these two sets of activity are connected, it is believed that the threat actors behind Viousictrap are likely to set up honeypot infrastructure by violating a wide range of internet-facing equipment, including Soho routers, SSL VPNs, DVRs, DVRs, Araknis Networks, and D-Link.

“This setup allows actors to observe attempts at exploitation across multiple environments, potentially collect private or zero-day exploits, and reuse access gained by other threat actors.”
The attack chain involves weaponization of CVE-2023-20118, download and run the BASH script via FTPGET, contacting an external server to get the WGET binaries. In the next step, the Cisco flaw is exploited a second time and uses it to run the second script obtained using the WGET that I previously dropped.

Netghost and internally referenced second-stage shell scripts are configured to redirect network traffic from compromised systems controlled by attackers to third-party infrastructure, thus facilitating middle school (AITM) attacks. It also has the ability to remove itself from compromised hosts to minimize forensic trails.
Sekoia said that all exploitation attempts came from a single IP address (“101.99.91[.]151”), in an early activity dating back to March 2025. At a notable event observed a month later, the malicious actor is said to have reused an undocumented webshell that had previously been employed in a Pola Red Botnet attack for his own manipulation.

“This assumption is consistent with the attacker’s use of netghosts,” said security researchers Felix Amile and Jeremy Sion. “The redirect mechanism can effectively place attackers as silent observers, collect exploitation attempts, and potentially collect web shell access during transit.”
As in this month, exploitation efforts are targeting ASUS routers, but from a different IP address (101.99.91)[.]239″), Threat actors are not known to create honeypots on infected devices, but all IP addresses actively used in the campaign are in Malaysia and are part of an autonomous system (AS45839) run by hosting provider Shinjiru.
The actor is thought to be of Chinese speaking origins based on the weak overlap with the Goblat infrastructure and the fact that traffic is redirected to numerous assets in Taiwan and the US.
“The ultimate purpose of ViciousTrap remains unknown [though] Sequoia concluded.
Source link