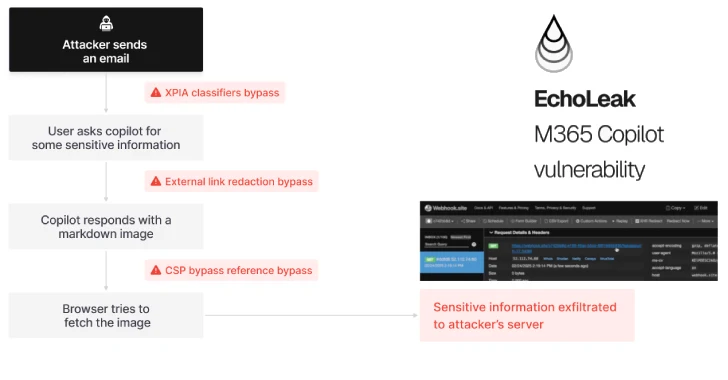
A new attack technology named Echoleak is characterized as a vulnerability in “zero-click” artificial intelligence (AI) that allows bad actors to eliminate sensitive data from the context of Microsoft 365 Copilot.
Critically evaluated vulnerabilities are assigned the CVE identifier CVE-2025-32711 (CVSS score: 9.3). No customer action is required. It’s already been addressed by Microsoft. There is no evidence that the flaws have been misused in the wild.
“AI command injection on the M365 Copilot allows fraudulent attackers to disclose information through the network,” the company said in an advisory released Wednesday. It was then added to Microsoft’s Patch Tuesday list in June 2025, bringing the total number of fixed defects to 68.
We discovered and reported this issue, AIM security, which paved the way for indirect rapid injections, stated that it was an instance of a massive language model (LLM) scope violation that led to unintended behavior.
LLM scope violations occur when attacker instructions are embedded in untrusted content. For example, emails sent from outside an organization can trick AI systems into accessing and processing privileged internal data without explicit user intent or interaction.
“The chain allows attackers to automatically remove sensitive and unique information from the context of an M365 co-pilot, without user awareness or relying on the behavior of a particular victim,” said the Israeli cybersecurity company. “The results are achieved despite the M365 Copilot’s interface being open only to employees in the organization.”

The attack sequence unfolds as follows:
Injection: Attackers send harmlessly-looking emails to employee’s Outlook inbox, including exploits of LLM scope violations. Leak sensitive data to attackers via Microsoft Teams and SharePoint URLs
“As a zero-click AI vulnerability, Echoleak opens widespread opportunities for data removal and tor attacks for motivated threat actors,” AIM Security said. “The ever-evolving world of agents presents the potential risks inherent in the design of agents and chatbots.”

“Attacks allow attackers to exclude the most sensitive data from the current LLM context. LLM is used against itself to ensure that the most sensitive data from the LLM context is leaked and can be performed in both single-turn and multiple conversations, without relying on the behavior of a particular user.”
MCP and Advanced Tools Addiction
This disclosure is because Cyberark has disclosed a Tool Addiction Attack (TPA) that affects Model Context Protocol (MCP) standards and extends beyond the description of the tool to the entire tool schema. Attack technique is called Full Sheema Addiction (FSP).
“Most of the attention on tool addiction attacks focuses on the explanatory field, which is a very underestimation of other potential attack surfaces,” said security researcher Simcha Kosman. “Every part of the tool schema is not just an explanation, but a potential injection point.”
The cybersecurity company said the issue is rooted in the MCP’s “a fundamentally optimistic trust model” that equates syntactic correctness with semantic safety, and that LLMS only assumes reasons rather than explicitly documented behaviour.
Additionally, TPAs and FSPs can be weaponized to stage advanced tool addiction attacks (ATPAs). This causes the attacker to design the tool with a benign description, but displays a fake error message that tricks LLM to access sensitive data (such as SSH keys) to address the alleged problem.
“As LLM agents become more capable and autonomous, interactions with external tools via protocols like MCP define how safe and reliable they operate,” Cosman said. “Tool addiction attacks, especially advanced forms like ATPA — expose important blind spots in current implementations.”
That’s not all. Given that MCP allows AI agents (or assistants) to interact with a wide range of tools, services, and data sources, vulnerabilities in the MCP client-server architecture can pose serious security risks, such as manipulating agents to leak data or executing malicious code.
This is evidenced by a critical security flaw recently disclosed in the popular Github MCP integration. This allows an attacker to hijack the user’s agent via a malicious Github issue and leak data from the private repository when the user prompts the model to “see the problem” to the model.
“The issue includes a payload that is executed by the agent as soon as you queried the list of public repository issues,” Invariant Labs researchers Marco Milanta and Luca Beurer-Kellner said they would classify it as a case of toxic agent flow.
That said, the vulnerability is a “basic architecture issue” and cannot be addressed on GitHub alone via server-side patches. This is because users must implement detailed permission controls so that agents can access only the interactions and continuous interactions between the agent and the MCP system.
Give way to MCP rebind attacks
The rapid rise of MCP as a “connection organization for enterprise automation and agent applications” has launched new attacks such as domain name system (DNS) rebinding to access sensitive data by leveraging Server-Sent Events (SSE), a protocol used by MCP servers for real-time streaming communications to MCP clients.

DNS rebinding attacks require tricking to treat external domains as if the victim’s browser belongs to the internal network (i.e. LocalHost). Designed to bypass the same Aurisine Policy (SOP) restrictions, these attacks are triggered when users visit malicious sites set up by attackers via phishing or social engineering.
“There’s been a disconnect between the browser security mechanism and the networking protocol,” Github’s Jaroslav Lobacevski said in an explanator for DNS Rebind, published this week. “If a web page host’s resolved IP address changes, the browser does not take that into consideration and treats the web page as if its origin had not been changed. This could be abused by an attacker.”
This behavior essentially allows client-side JavaScript on malicious sites to bypass security controls and target other devices on the victim’s private network that are not exposed to the public internet.
 MCP rebind attack
MCP rebind attack
MCP rebind attacks leverage the adversary website’s ability to interact with MCP servers running on the local host via SSE, and ultimately access internal resources on the victim’s local network to remove sensitive data.
“By abusing SSE’s long-life connections, attackers can pivot from external phishing domains to target internal MCP servers,” the Straiker AI Research (Star) team said in an analysis released last month.
It is worth noting that the SSE was deprecated in November 2024 in favor of streamable HTTP, due to the risks that DNS poses from attack relocation. To mitigate the threat of such attacks, we recommend that you perform authentication of your MCP server and verify the “Origin” header of all incoming connections to your MCP server to ensure that your requests are from trusted sources.
Source link