Cybersecurity researchers have flagged a new set of 175 malicious packages on the npm registry that were used to facilitate credential harvesting attacks as part of an unusual campaign.
According to Socket, these packages were downloaded a total of 26,000 times and serve as the infrastructure for a widespread phishing campaign codenamed “Beamglea” that targeted more than 135 industrial, technology, and energy companies around the world.
“Since the names of the packages are randomized, it is unlikely that developers will accidentally install them, but the download count is likely to include security researchers, automated scanners, and CDN infrastructure that analyze the packages after publication,” said security researcher Kush Pandya.
This package is known to host a redirect script that uses npm’s public registry and unpkg.com’s CDN to route victims to a credential collection page. Some aspects of the campaign were first flagged by safety Paul McCarty late last month.

Specifically, this library comes with a Python file named “redirect_generator.py” that allows you to programmatically create and publish npm packages named “redirect-xxxxxx”. “x” refers to a random alphanumeric string. The script then inserts the victim’s email address and a custom phishing URL into the package.
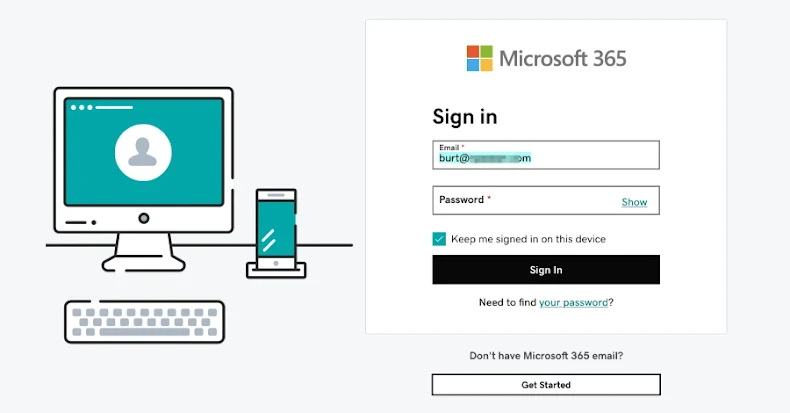
Once a package is published on the npm registry, the “malware” begins creating HTML files containing references to the UNPKG CDN associated with the newly published package (e.g. “unpkg”[.]com/redirect-xs13nr@1.0.0/beamglea.js”). The attacker allegedly uses this behavior to distribute an HTML payload that, when opened, loads JavaScript from the UNPKG CDN and redirects the victim to a Microsoft credential harvesting page.
The JavaScript file “beamglea.js” is a redirect script that contains the victim’s email address and the URL the victim should go to to obtain their credentials. Socket said it discovered more than 630 HTML files disguised as purchase orders, technical specifications or project documents.
This means that npm packages are not designed to run malicious code when installed. Instead, the campaign leverages npm and UNPKG to host the phishing infrastructure. It is not currently clear how the HTML file is distributed, but it is possible that the HTML file could be propagated via email that tricks the recipient into launching a specially crafted HTML file.
“When a victim opens these HTML files in a browser, the JavaScript immediately redirects them to the phishing domain, passing the victim’s email address via a URL fragment,” Socket said.
“The phishing page then pre-populates the email field to make it appear as if the victim is accessing a legitimate login portal where they already know themselves. These pre-filled credentials reduce the victim’s suspicions and significantly increase the success rate of the attack.”

This finding once again highlights the evolving nature of threat actors, who are constantly adapting their techniques to stay ahead of defenders and constantly developing new techniques to detect attackers. This case highlights the large-scale misuse of legitimate infrastructure.
“The npm ecosystem becomes an unconscious infrastructure rather than a direct attack vector,” says Pandya. “While developers who install these packages do not see any malicious behavior, victims who open specially crafted HTML files are redirected to a phishing site.”
“By publishing 175 packages across nine accounts and automating victim-specific HTML generation, the attackers created a resilient phishing infrastructure that has no hosting costs and leverages a trusted CDN service. The combination of npm’s open registry, unpkg.com’s automated serving, and minimal code creates a reproducible playbook that other threat actors can adopt.”
Source link