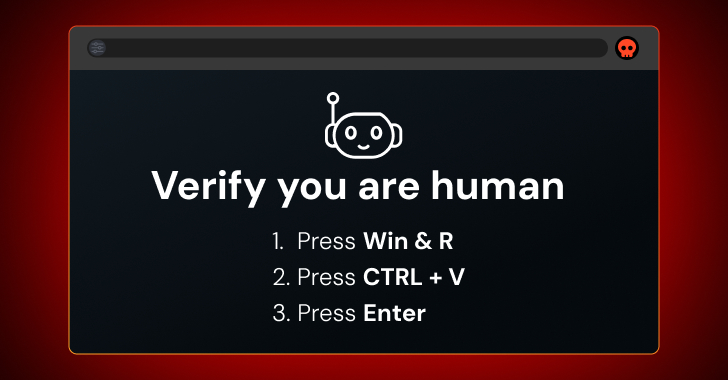
ClickFix, FileFix, fake CAPTCHAs, or whatever you call them, attacks in which users manipulate malicious scripts in their web browsers are a rapidly increasing source of security breaches.
ClickFix attacks prompt users to resolve some problem or issue on their browser. CAPTCHAs are the most common, but so are things like fixing errors on web pages.
However, this name is a bit misleading. The main factor behind the attack is to trick users into executing malicious commands on their device by copying malicious code from a page’s clipboard and running it locally.
 Examples of ClickFix lures used by attackers in the wild.
Examples of ClickFix lures used by attackers in the wild.
ClickFix is known to be used regularly by the Interlock ransomware group and other significant threat actors, including state-sponsored APTs. Many recent public data breaches have involved ClickFix-style TTPs, including Kettering Health, DaVita, the City of St. Paul, Minnesota, and Texas Tech University Health Sciences Center (many more breaches may involve ClickFix with unknown or undisclosed attack vectors).
But why are these attacks proving so effective?
Reason 1: Users are not ready for ClickFix
Over the past decade, user awareness has focused on stopping users from clicking on links in suspicious emails, downloading dangerous files, or typing usernames and passwords into random websites. It wasn’t focused on opening programs and running commands.
Suspicion is further diminished when you consider that 99% of the time malicious clipboard copy actions are performed in the background via JavaScript.
 An example of unobfuscated JavaScript code that automatically performs a copy function on a ClickFix page without user input.
An example of unobfuscated JavaScript code that automatically performs a copy function on a ClickFix page without user input.
And as modern ClickFix sites and lures look increasingly legitimate (see examples below), it’s no surprise that users fall victim to them.
 One of the more legitimate-looking ClickFix lures. It has an embedded video that shows the user what to do.
One of the more legitimate-looking ClickFix lures. It has an embedded video that shows the user what to do.
Given the fact that these attacks are moving away from email entirely, this doesn’t fit into the model of what users are trained to suspect.
The primary delivery vectors identified by Push Security researchers were found to be SEO poisoning and malvertising via Google search. By creating new domains or hijacking legitimate ones, attackers create a watering hole scenario in which they intercept users as they browse the Internet.
There’s also no convenient “Report Phishing” button or workflow to notify your security team about Google search results, social media messages, website ads, etc., even if you’re suspicious.
Reason 2: ClickFix is not detected during delivery
There are several aspects to why ClickFix attacks are not detected by technical controls.
ClickFix pages, like other modern phishing sites, use a variety of evasion techniques to avoid being flagged by security tools, from email scanners to web crawling security tools to web proxies that analyze network traffic. Detection evasion primarily involves impersonating and rotating domains to stay ahead of known bad detections (blocklists), using bot protection to prevent analysis, and heavily obfuscating page content to stop detection signatures from firing.
Also, using a delivery vector other than email cuts off the entire window of opportunity for detection.
 Like other modern phishing attacks, ClickFix’s lures are distributed throughout the Internet, not just through email.
Like other modern phishing attacks, ClickFix’s lures are distributed throughout the Internet, not just through email.
Malvertising adds another layer of targeting to the situation. For example, Google Ads can target searches from specific geographic locations, tailor to specific email domain matches, or specific device types (desktop, mobile, etc.). If you know your target’s location, you can adjust your ad parameters accordingly.
Along with other techniques such as conditional loading that returns appropriate lures to the operating system (or doesn’t trigger at all unless certain conditions are met (e.g. accessing from a mobile OS, accessing from outside the target IP range)), attackers have a way to bypass security controls at the email layer and reach a large number of potential victims while preventing unnecessary analysis.
 An example of a ClickFix lure built on a vibe-coded site.
An example of a ClickFix lure built on a vibe-coded site.
Finally, because the code is copied within the browser sandbox, common security tools cannot monitor and flag this action as potentially malicious. This means that the last and only time an organization can stop ClickFix is on the endpoint after a user attempts to execute malicious code.
Reason 3: EDR is the last and only line of defense and is not foolproof
There are multiple stages to an attack that can and should be blocked by EDR, but context determines whether a higher level of detection or action is blocked in real time.
Since no files are downloaded from the web and the act of executing code on the machine is initiated by the user, there is no context to tie the act to another application to make it look suspicious. For example, malicious PowerShell executed from Outlook or Chrome looks obviously suspicious, but because it is user-initiated, it is isolated from the context of where the code was delivered.
The malicious command itself may be obfuscated or split into several stages to avoid easy detection by heuristic rules. EDR telemetry may record that a PowerShell process was executed, but it may not immediately flag it unless there is a known malicious signature or clear policy violation.
The final stage where a reputable EDR thwarts an attack is at the point of malware execution. But evading detection is a cat-and-mouse game, and attackers are always looking for ways to tweak their malware to evade or disable detection tools. Therefore, the exception will occur.
Additionally, if your organization allows employees or contractors to use unmanaged BYOD devices, there are likely gaps in EDR coverage.
Eventually, your organization will rely on a single line of defense. If an attack isn’t detected and blocked by EDR, it won’t be discovered at all.
Why standard recommendations are inadequate
Most of the vendor-independent recommendations are for Windows for typical users.[ファイル名を指定して実行]It focuses on restricting access to services such as dialog boxes. However, while mshta and PowerShell remain the most commonly observed, security researchers have already discovered a wide range of LOLBINS targeting a variety of services, many of which are difficult to prevent users from accessing.
It’s also worth considering how ClickFix-style attacks will continue to evolve in the future. Current attack vectors span browsers and endpoints. What if the attack could be done entirely within the browser and bypass EDR entirely? For example, by pasting malicious JavaScript directly into the devtools of the relevant web page.
 Current hybrid attack paths involve attackers delivering decoys within the browser to compromise the endpoint and access credentials and cookies stored in the browser. What if you could skip the endpoint entirely?
Current hybrid attack paths involve attackers delivering decoys within the browser to compromise the endpoint and access credentials and cookies stored in the browser. What if you could skip the endpoint entirely?
First-line protection against ClickFix on your browser
Push Security’s newest feature, Malicious Copy and Paste Detection, responds to ClickFix-style attacks as quickly as possible through browser-based detection and blocking. This is a universally effective control that works regardless of lure delivery channels, page style and structure, or malware type and execution details.
Unlike brute force DLP solutions that completely block copy and paste, Push protects your employees without disrupting the user experience or hindering productivity.
Watch the video below to learn more.
learn more
If you want to learn more about ClickFix attacks and their evolution, check out our upcoming webinar where Push Security researchers take a closer look at real-world ClickFix examples and demonstrate how ClickFix sites work under the hood.

Push Security’s browser-based security platform provides comprehensive attack detection and response capabilities against techniques such as AiTM phishing, credential stuffing, ClickFixing, malicious browser extensions, and session hijacking using stolen session tokens. You can also use Push to find and fix vulnerabilities across the apps your employees use, including ghost logins, SSO coverage gaps, MFA gaps, weak passwords, and risky OAuth integrations, to strengthen your identity attack surface.
To learn more about Push, check out our latest product overview or schedule a live demo with our team.
Source link