Cybersecurity researchers have demonstrated a new technique in which malicious web browser extensions are impersonating add-ons with installed malicious web browser extensions.
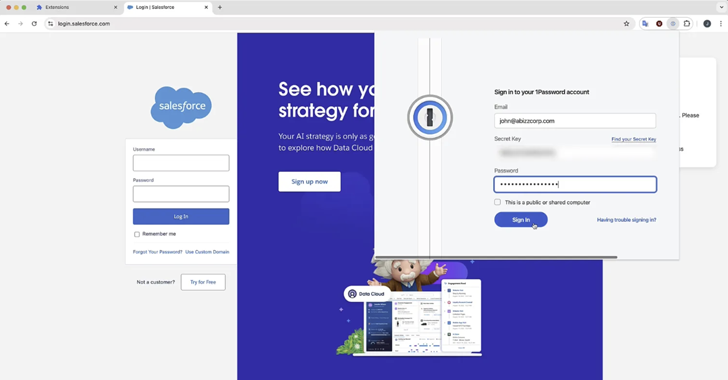
“Polymorphic extensions create pixel-perfect replicas of target icons, HTML pop-ups, workflows, and temporarily disable legitimate extensions, making them extremely convincing that victims believe they are offering qualifications for the actual extension.
Harvested qualifications can be abused by threat actors, hijacking online accounts and gaining unauthorized access to sensitive personal and financial information. This attack affects all Chromium-based web browsers, including Google Chrome, Microsoft Edge, Brave, Opera.
The approach relies on banks for the fact that users generally pin extensions to the browser toolbar. In a hypothetical attack scenario, a threat actor can expose a polymorphic extension to the Chrome web store (or any extension market) and disguise it as a utility.

Add-ons provide advertised functionality to avoid being suspected, but activate background malicious features by actively scanning the presence of web resources that correlate with a particular target extension using a technique called web resource hits.
Once the appropriate target expansion is identified, the attack moves to the next stage and transforms it into a replica of the legitimate expansion. This is achieved by matching the Rogue extension icon with the target icon and temporarily disabling the actual add-on via the “Chrome.management” API. This will remove it from the toolbar.
“Polymorphic dilation attacks are extremely powerful because they take advantage of the tendency for humans to rely on visual cues as confirmation,” Squarex said. “In this case, use the pinned bar’s extension icon to notify the user of the tools they are interacting with.”
The findings come a month after the company discloses another attack method called browser SyncJacking.
Source link