At least four different threat actors have been identified as being involved in a massive advertising fraud called Badbox and an updated version of the Housing Commission’s proxy scheme, which depicts an interconnected cybercrime ecosystem.
This includes Salestracker Group, Moyu Group, Lemon Group and Longtv, according to new findings from the Human Satori Threat Intelligence and Research team, published in collaboration with Google, Trend Micro, Shadowserver and other partners.
“Complete and vast fraudulent operations” is called Badbox 2.0. This is described as the largest botnet of infected connected TV (CTV) devices.
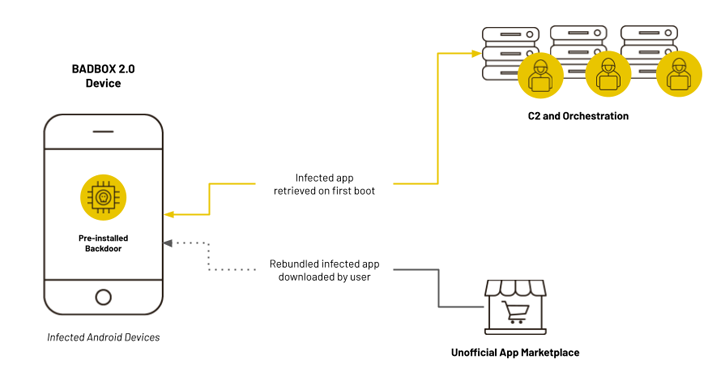
“BadBox 2.0, like its predecessor, starts with a backdoor of low-cost consumer devices that allow threat actors to load fraud modules remotely,” the company said. “These devices communicate with a command and control (C2) server owned and operated by a set of clear but cooperative threat actors.”
Threat actors are known to utilize several ways, ranging from hardware supply chain compromises to third-party markets.

Then, the infected device becomes part of a big botnet that is being abused for program ad fraud, click on fraud and provide illegal housing proxy services –
Launch hidden ads and hidden webviews to generate fake ad revenue navigation to low-quality domains, click on ads for financial profits through compromised devices using account takeover (ATO), fake account creation, malware delivery, DDO attacks
It is estimated that as many as a million devices, consisting mainly of cheap Android tablets, connected TV (CTV) boxes, digital projectors and automotive infotainment systems, have fallen prey to the Badbox 2.0 scheme. All affected devices are manufactured in mainland China and shipped globally. The majority of infections have been reported in Brazil (37.6%), the United States (18.2%), Mexico (6.3%), and Argentina (5.3%).
This operation was then partially destroyed for the second time three months after a private number of Badbox 2.0 domains cave down, attempting to block communication with infected devices. Google has removed a set of 24 apps from the Play Store that distributed the malware. Some of that infrastructure was previously removed by the German government in December 2024.
“The infected device is not an Android TV OS device, but an Android Open Source Project Devices. “If your device is not certified by Play Protect, Google has no record of security and compatibility test results. PlayProtect Protect certified Android devices undergo extensive testing to ensure quality and user safety.”

The backdoor that forms the core of the operation is based on Android malware known as Triada. The codename BB2DOOR is propagated in three different ways. Pre-installed components on the device were retrieved from a remote server when first booted, and downloaded from over 200 troilerized versions of popular apps from third-party stores.
This is said to be handicrafts for a threat cluster named Moyu Group, which promotes residential proxy services built on devices infected with Badbox 2.0. The other three threat groups are responsible for overseeing other aspects of the scheme –
The Salestracker Group, connected to the original Badbox operation, the infected device Lemon Group, connected to a residential proxy service based on Badbox, and the Salestracker Group, connected to the Lemon Group, connected to an AD fraud campaign across HTML5 (H5) gaming website, and the Malaysian internet and media companies portray AD floods.
“These groups were connected to each other through shared infrastructure (a common C2 server) and historical and current business relationships,” Human said.
The latest iterations represent important evolutions and adaptations, and attacks also rely on more sophisticated versions of malware that involve changing legitimate Android libraries to set persistence.

Interestingly, there is some evidence suggesting overlap between BB2DOOR and VO1D. This is another malware known to specifically target unbranded Android-based TV boxes.
“The threat of Badbox 2.0 in particular is not a small part due to the open season of operations,” the company added. “If you place the backdoor in place, the infected device can instruct the infected device to carry out a cyberattack developed by the developed threat actor.”
Development is underway as Google has removed more than 180 Android apps, spanning 56 million downloads, to engage in a sophisticated ad fraud scheme that utilizes fake Android apps to deploy endless, annoying full-screen interstitial video ads, with every IAS threat lab.
It also follows the discovery of a new campaign using DeepSeek-themed decoy sites to trick unsuspecting users into downloading Android banking malware called Octo.
Source link