Cybersecurity researchers weaponized Layave app_keys, which are leaking Laravel App_Keys, to discover serious security issues that allow hundreds of applications to gain remote code execution capabilities.
“Laravel’s App_Key, essential for encrypting sensitive data, is often published (on GitHub, for example),” Gitguardian says. “If an attacker accesses this key, it can take advantage of the flaws in agility to execute arbitrary code on the server. It can put data and infrastructure at risk.”
The company said it could work with Synacktiv to extract over 260,000 App_Keys from Github from 2018 to May 30, and identify over 600 Laravel applications in the process. Gitguardian said that over 10,000 unique App_Keys were observed across GitHub, of which 400 App_Keys were validated as features.
App_Key is a random 32-byte encryption key that is generated during Laravel installation. It is stored in an application’s .ENV file and used to encrypt and decrypt data, generate secure random strings, sign and verify data, create unique authentication tokens, and create critical security components.
Gitguardian noted that when Laravel’s current implementation of Decrypt() function introduces security issues, it automatically requires decrypted data to be removed, thereby opening the door for potential remote code execution.

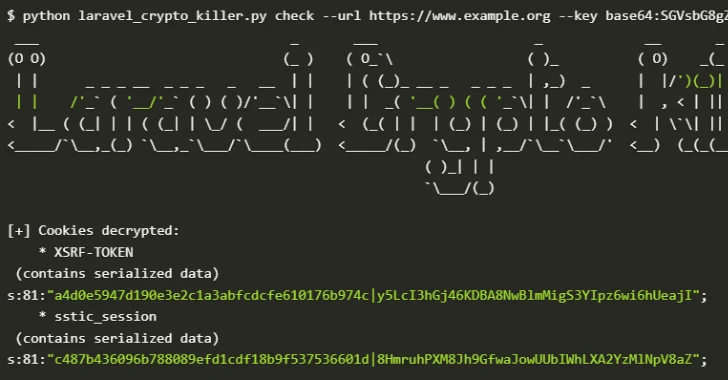
“In particular, in Laravel applications, remote code execution can be achieved on Laravel web servers if an attacker can get APP_KEY and call the Decrypt() function on a malicious payload.”
“This vulnerability was first documented in CVE-2018-15133 and affected the Laravel version before 5.6.30. However, this attack vector persists with the new Laravel version when Developers explicitly configure session serialization of cookies with COSE_Driver = Cookie settings, as demonstrated by CVE-2024-5556.”
It is worth noting that CVE-2018-15133 was exploited in the wild by threat actors associated with Androxgh0st malware.
Further analysis revealed that 63% of App_Key exposures usually come from .ENV files (or variants thereof) that contain other valuable secrets, such as cloud storage tokens, database credentials, e-commerce platforms, customer support tools, and secrets related to artificial intelligence (AI) services.
More importantly, around 28,000 app_key and app_url pairs are exposed simultaneously on Github. Of these, approximately 10% have been found to be effective, making 120 applications vulnerable to trivial remote code execution attacks.
Given that the APP_URL configuration specifies the base URL of the application, exposing both the APP_URL and APP_KEY creates a powerful attack vector that allows threat actors to access the app directly, retrieve session cookies, and decorate them using the exposed key.
Scrubbing secrets from the repository is not sufficient, especially if they have already been cloned or cached by third-party tools. All developers need is a clear rotational path supported by monitoring CI logs, image builds, and flagging all future reappearances of strings that are sensitive to the container layer.
“Developers should not simply remove exposed app_keys from the repository without proper rotation,” Gitguardian said. “A proper response will be to immediately rotate the compromised app_key, update all production systems with new keys, and implement continuous secret surveillance to prevent future exposure.”
These types of incidents are also consistent with the broader PHP deintervention vulnerabilities that help tools like PHPGGC to create gadget chains that cause unintended behavior while loading objects. When using in a Laravel environment with leaked keys, such gadgets can achieve a full RCE without the need to violate the logic or route of the app.
The disclosure comes after Gitguardian revealed that he had discovered “a astounding 100,000 valid secrets” in Docker images that can be published in the Docker Hub registry. This includes secrets related to Amazon Web Services (AWS), Google Cloud, and Github Tokens.

A new binary analysis of over 80,000 unique Docker images across 54 organizations and 3,539 repositories revealed 644 unique secrets, including generic credentials.
“The secrets appear in various file types, including source code, configuration files, and even areas where many existing scanners are missing,” the company said. “In addition, the entire GIT repository within a container image represents a serious and often overlooked security risk.”

But that’s not all. The rapid adoption of Model Context Protocol (MCP) that enables agent workflows in enterprise-driven AI applications has opened up brand new attack vectors.
Specifically, Gitguardian found that 202 of them have leaked at least one secret, accounting for 5.2% of all repositories. This is the number the company said is “slightly higher than the 4.6% incidence observed across all public repositories,” making MCP servers a “new source of secret leaks.”
This study focuses on Laravel, but the same underlying problem (the secrets of public repository) applies to other stacks. Organizations need to explore centralized secret scans, Laravel-specific hardening guides, and secure design patterns for managing .ENV files and container secrets across the framework.
Source link