Cybersecurity and data privacy are always in the news. The government has passed a new cybersecurity law. Companies are investing in cybersecurity management, including firewalls, encryption, and awareness training at the record level.
Still, people are based on data privacy.
In 2024, the Identity Theft Resource Center reported that businesses had sent 1.3 billion notifications to victims of data breaches. This is more than three times the notifications sent in the previous year. Despite the growing efforts, it is clear that personal data breaches continue as well as accelerating.
You might like it
What can you do about this situation? Many people consider cybersecurity issues to be technical. They are correct: Technical control is an important part of protecting personal information, but they are not sufficient.
As a professor of information technology, analysis and operations at the University of Notre Dame, I research methods to protect personal privacy.
Solid personal privacy protection consists of three pillars: accessible technical control, public perception of privacy needs, and public policy that prioritizes personal privacy. Each plays an important role in protecting individual privacy. The weaknesses of those who put the entire system at risk.
The first line of defense
Technology is the first line of defense, protecting access to computers that store data and encrypting information as they move between computers to prevent intruders from gaining access. But even the best security tools can fail when misused, misunderstood or ignored.
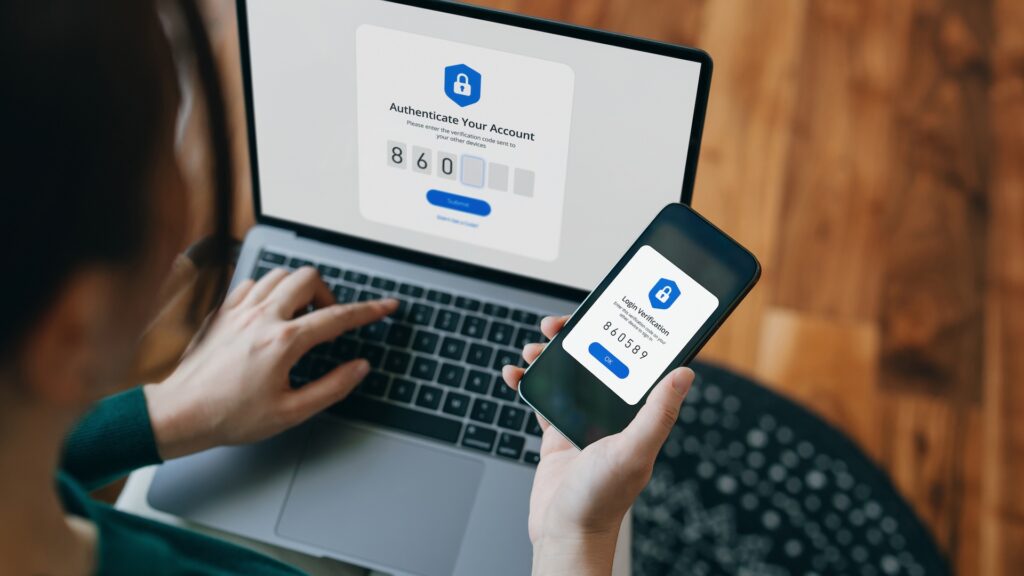
Two technical controls are particularly important: encryption and multifactor authentication. These are the backbone of digital privacy, and are widely adopted and work best when properly implemented.
Encryption uses complex mathematics to place sensitive data in an unreadable format that can only be unlocked with the appropriate key. For example, a web browser uses HTTPS encryption to protect information when you visit a secure web page. This prevents everyone on the network, or the network between you and the website, from eavesdropping on communication. Today, almost all web traffic is encrypted like this.
Related: Quantum Computers is a dream come true for hackers, putting everything from military secrets to banking information at risk. Can we stop them?
But if you’re good at encrypting data on your network, why are you suffering from all of these data breaches? The reality is that encrypting data in transit is only part of the challenge.
Protecting saved data
You also need to protect your data where it is stored on your mobile phone, laptop, or servers that make up your cloud storage. Unfortunately, this is a place where security is lacking. Encrypting stored or resting data is not as wide as encrypted data moving from one location to another.
Modern smartphones usually encrypt files by default, but the same cannot be said about cloud storage or company databases. According to a 2024 industry survey, at least 80% of information stored in the cloud reported that at least 80% of information stored in the cloud is encrypted. This will potentially reveal a huge amount of unencrypted personal information if an attacker manages to break in. Without encryption, intruding into a database is like opening an unlocked filing cabinet.
Multifactor authentication is a security measure that requires multiple forms of validation to be provided before accessing sensitive information. This type of authentication is more difficult to crack than just a password, as it requires a variety of different kinds of information combinations. Often, you combine what you have, such as a password, with smartphone apps that can generate verification codes, or something that is part of something like a fingerprint. Proper use of multifactor authentication reduces the risk of compromise by 99.22%.
Another industry survey shows that 83% of organizations require employees to use multifactor authentication, leaving millions of accounts that are still protected except passwords. Not only is it a close gap of 17%, it’s not just a best practice, as attackers are more refined and qualification theft remains ramp-extensive. it’s necessary.
Multifactor authentication is one of the simplest and most effective steps an organization can take to prevent data breaches, but it remains underused. Increased recruitment can dramatically reduce the number of successful attacks each year.
Consciousness gives people the knowledge they need
When people make mistakes, even the best technology is lacking. According to a Verizon report, human error played a role in 68% of data breaches in 2024. Organizations can mitigate this risk through employee training, minimizing data (collecting only the information needed for a task and removing it when it is no longer needed).
Policy, audits, and incident response plans help organizations prepare for possible data breaches so that they reduce damage and who can take responsibility and learn from experience. It is also important to use physical protection measures such as locking server rooms to prevent insider threats and physical intrusions.
Public policy is accountable to the organization
Legal protections help to hold organizations accountable in maintaining data protection and allowing people to control it. The European Union’s General Data Protection Regulation is one of the most comprehensive privacy laws in the world. It requires strong data protection practices and gives people the right to access, modify and delete personal data. And general data protection regulations have teeth. In 2023, Meta was fined 1.2 billion euros (US$1.4 billion) when it was discovered that Facebook was violated.
Despite years of debate, the United States still does not have comprehensive federal privacy laws. There have been some proposals introduced in Congress, but none have made them across the finish line. Instead, it has a mix of state regulations and industry-specific rules. This bridges gaps, such as the portability of health insurance, the accountability of health data, and the Gram Reach Breely Act for financial institutions.
Although some states have passed their own privacy laws, the patchwork leaves uneven protection for Americans and causes a headache for compliance for businesses operating across their jurisdictions.
Tools, policies and knowledge exist to protect personal data, but the use of people and institutions is still lacking. Stronger encryption, broader use of multifactor authentication, better training, clearer legal standards can prevent many violations. It is clear that these tools work. What we need now is the collective will and a unified federal mission to implement these protections.
This article is part of a series on data privacy that explores who collects your data, what they collect, who sells and buys your data, what they do with it, and what you can do about it.
This edited article will be republished from the conversation under a Creative Commons license. Please read the original article.
Source link