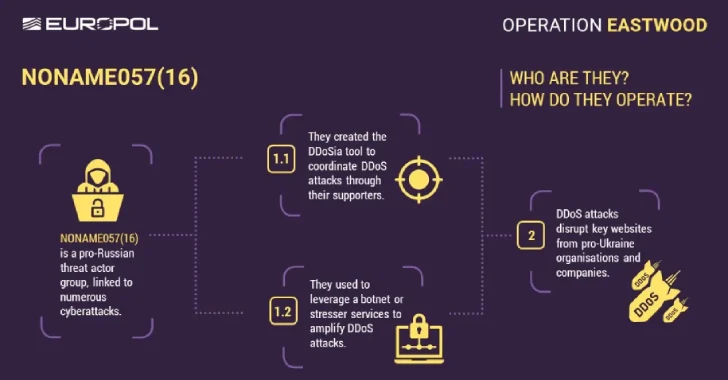
The international operations coordinated by Europol disrupt the infrastructure of a Russian hacktivist group known as NonMAME057 (16), which is associated with a series of distributed denial of service (DDOS) attacks against Ukraine and its allies.
This action has dismantled most of the group’s central server infrastructure and over 100 systems around the world. The joint efforts included two arrests in France and Spain, searching two dozen homes in Spain, Italy, Germany, the Czech Republic, France and Poland, and issuing a warrant for arrests for six Russian citizens.
Operation Eastwood took place between July 14th and 17th, with authorities from the Czech Republic, France, France, Germany, Italy, Lithuania, Poland, Spain, Sweden, Switzerland, the Netherlands and the United States. The study was also supported by Belgium, Canada, Estonia, Denmark, Latvia, Romania and Ukraine.

NONAME057 (16) has been in operation since March 2022 and serves as a prokremlin group to mobilize ideologically motivated sympathizers with telegrams to launch DDOS attacks using a special program called DDOSIA and maintain efforts to continue to exchange cryptocurrency payments. It occurred shortly after Russia’s invasion of Ukraine.
Five individuals from Russia have been added to the EU’s most wanted list, allegedly supporting nonme57 (16) –
Andrey Muravyov (aka Dazbastadraw) Maxim Nikolaevich Lupine (aka S3Rmax) Olga Evstratova (aka Olechochek, Olenka) Mihail Evgeyevich Burlakov (aka Ddosator3000, Darkklogo) and Rej Stanislavovich Ponnysima
“Burlakov is suspected of being a central member of the group “NonAME057 (16)” and therefore contributed greatly to the DDOS attacks in various institutions in Germany and other countries.”
“In particular, he envisions a leading role within the group under the pseudonym “Darkklogo” and is suspected in this role that included developing and further optimization of software for strategic identification of targets, as well as implementing payments for the development of attack software and lease of illegal servers. ”
Additionally, Evstratova, considered a core member of the group, has been accused of being responsible for optimizing Ddosia attack software. Avrosimow is attributed to 83 cases of computer sabotage.
Europol said the authorities reached out to more than 1,000 individuals believed to be supporters of cybercrime networks and notified them of criminal liability they would bear to use automated tools to coordinate DDOS attacks.
“In addition to the network’s activities estimated to be over 4,000 supporters, the group was also able to build its own botnet consisting of hundreds of servers used to increase the attack load,” Europol said.
“Game-like dynamics, regular screams, leaderboards, or badges mimicked volunteers with a sense of status. This ginged manipulation, often targeting young criminals, was emotionally reinforced by the narrative of defending Russia or revenging political events.”

In recent years, threat actors have been observed to stage a series of attacks targeting Swedish authorities and bank websites against 250 German companies and institutions over the course of 14 separate waves since November 2023.
Last July, Spain’s La Guardia Civil arrested three suspected members of the group for participating in a “denial of service cyberattack on public institutions and strategic sectors of Spain and other NATO countries.”
This development is because Russian hackitivist groups like Z-Pentest, Dark Engine and Sector 16 are increasingly training their vision on critical infrastructure, surpassing the weakness of websites related to DDOS attacks and usually ideologically motivated cyberattacks.
“The group coordinates messaging, adjusts timing and shares targeting priorities, suggesting intentional collaboration to support Russia’s strategic cyber goals,” Cyble said.
Source link